Harbor概述
Harbor是由VMware公司开源的容器镜像仓库。事实上,Harbor是在Docker Registry上进行了相应的企业级扩展,从而获得了更加广泛的应用,这些新的企业级特性包括:管理用户界面,基于角色的访问控制,AD/LDAP集成以及审计日志等,足以满足基本企业需求。
官方:https://goharbor.io/
GitHub:https://github.com/goharbor/harbor
Harbor部署先决条件
服务器硬件配置:
最低要求:CPU2核/内存4G/硬盘40GB
推荐:CPU4核/内存8G/硬盘160GB
软件:
Docker CE 17.06版本+
Docker Compose 1.18版本+
Harbor安装有2种方式:
在线安装:从Docker Hub下载Harbor相关镜像,因此安装软件包非常小
离线安装:安装包包含部署相关镜像,因此安装包较大
安装最新版的Harbor
wget https://github.com/goharbor/harbor/releases/download/v1.10.1/harbor-offline-installer-v1.10.1.tgztar -xf harbor-offline-installer-v1.10.1.tgzcd harbor#导入镜像docker load -i harbor.v1.10.1.tar.gz#修改配置文件并把https去掉vim harbor.ymlhostname = 192.168.10.130#安装docker-composecurl -L https://github.com/docker/compose/releases/download/1.24.0-rc1/docker-compose-`uname -s`-`uname -m` -o /usr/local/bin/docker-composechmod +x /usr/local/bin/docker-compose./prepare./install.shdocker-compose startdocker-compose stop
Harbor部署HTTP
1、先安装Docker和Docker Compose安装依赖包yum install -y yum-utils添加Docker软件包源yum-config-manager \--add-repo \https://download.docker.com/linux/centos/docker-ce.repo安装Docker CEyum install -y docker-ce启动Dockersystemctl start dockersystemctl enable docker配置Docker加速器源cat /etc/docker/daemon.json{"registry-mirrors": ["https://b9pmyelo.mirror.aliyuncs.com"]}重启Dockersystemctl restart docker安装Docker Compose下载好docker-compose-Linux-x86_64mv docker-compose-Linux-x86_64 /usr/bin/docker-composechmod +x /usr/bin/docker-compose2、部署Harbor HTTPtar -zxvf harbor-offline-installer-v2.0.0.tgzcd harborcp harbor.yml.tmpl harbor.ymlvi harbor.yml配置内容如下:hostname: reg.harbor.com# http related confighttp:# port for http, default is 80. If https enabled, this port will redirect to https portport: 80#先注释掉https相关配置# https related config#https:# https port for harbor, default is 443# port: 443harbor_admin_password: Harbor12345 #harbor密码./prepare./install.sh
Harbor部署HTTPS
1、生成SSL证书cat cfssl.shwget https://pkg.cfssl.org/R1.2/cfssl_linux-amd64wget https://pkg.cfssl.org/R1.2/cfssljson_linux-amd64wget https://pkg.cfssl.org/R1.2/cfssl-certinfo_linux-amd64chmod +x cfssl*mv cfssl_linux-amd64 /usr/bin/cfsslmv cfssljson_linux-amd64 /usr/bin/cfssljsonmv cfssl-certinfo_linux-amd64 /usr/bin/cfssl-certinfocat certs.shcat > ca-config.json <<EOF{"signing": {"default": {"expiry": "87600h"},"profiles": {"kubernetes": {"expiry": "87600h","usages": ["signing","key encipherment","server auth","client auth"]}}}}EOFcat > ca-csr.json <<EOF{"CN": "kubernetes","key": {"algo": "rsa","size": 2048},"names": [{"C": "CN","L": "Beijing","ST": "Beijing"}]}EOFcfssl gencert -initca ca-csr.json | cfssljson -bare ca -cat > reg.harbor.com-csr.json <<EOF{"CN": "reg.harbor.com","hosts": [],"key": {"algo": "rsa","size": 2048},"names": [{"C": "CN","L": "BeiJing","ST": "BeiJing"}]}EOFcfssl gencert -ca=ca.pem -ca-key=ca-key.pem -config=ca-config.json -profile=kubernetes reg.harbor.com-csr.json | cfssljson -bare reg.harbor.com2、Harbor启动HTTPSvi harbor.yml配置内容如下:#注释掉http# http related config#http:# port for http, default is 80. If https enabled, this port will redirect to https port# port: 80#启动https# https related confighttps:# https port for harbor, default is 443port: 443# The path of cert and key files for nginxcertificate: /root/harbor/ssl/reg.harbor.com.pemprivate_key: /root/harbor/ssl/reg.harbor.com-key.pem3、重新配置并部署Harbor./preparedocker-compose downdocker-compose up -d4、将数字证书复制到Docker主机mkdir -p /etc/docker/certs.d/reg.harbor.comcp /root/ssl/reg.harbor.com.pem /etc/docker/certs.d/reg.harbor.com5、验证绑定本地hostsvi /etc/hosts192.168.211.128 reg.harbor.comdocker login reg.harbor.comusername: adminpassword: Harbor12345浏览器访问https://reg.harbor.com
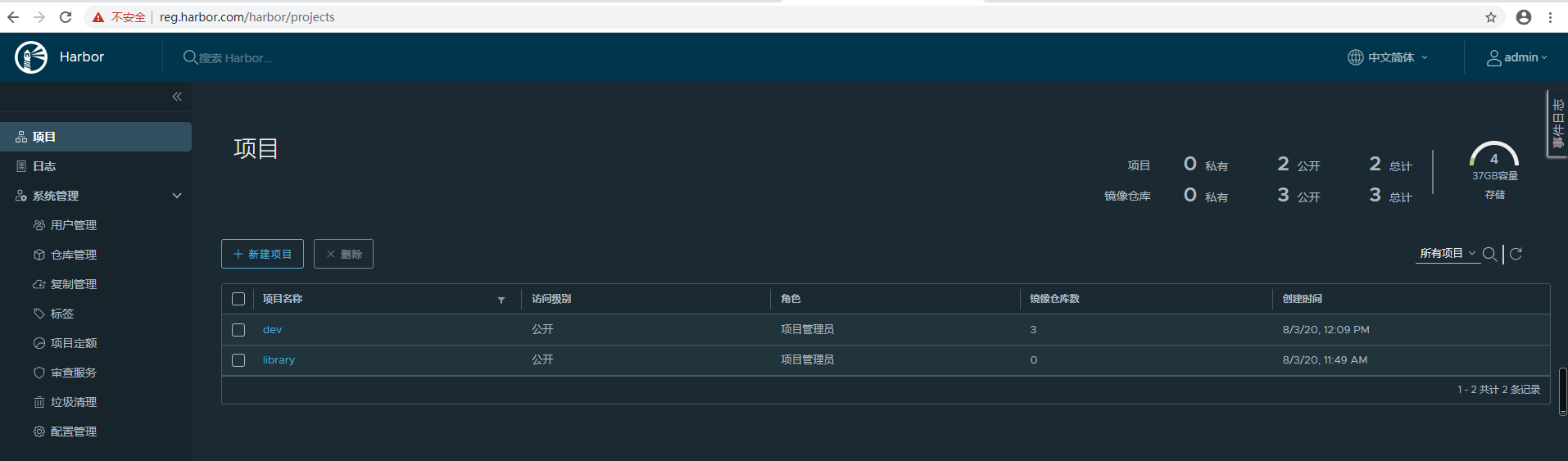
Harbor镜像漏洞扫描
闲聊:我们知道 镜像安全也是容器化建设中一个很重要的环节,像一些商业软件如:Aqua就很专业但是收费也是很昂贵的,今天我们介绍下Harbor自带的镜像扫描器
添加扫描模块
./prepare --with-clair
prepare base dir is set to /root/harbor
Clearing the configuration file: /config/log/logrotate.conf
Clearing the configuration file: /config/log/rsyslog_docker.conf
Clearing the configuration file: /config/nginx/nginx.conf
Clearing the configuration file: /config/core/env
Clearing the configuration file: /config/core/app.conf
Clearing the configuration file: /config/registry/passwd
Clearing the configuration file: /config/registry/config.yml
Clearing the configuration file: /config/registry/root.crt
Clearing the configuration file: /config/registryctl/env
Clearing the configuration file: /config/registryctl/config.yml
Clearing the configuration file: /config/db/env
Clearing the configuration file: /config/jobservice/env
Clearing the configuration file: /config/jobservice/config.yml
Generated configuration file: /config/log/logrotate.conf
Generated configuration file: /config/log/rsyslog_docker.conf
Generated configuration file: /config/nginx/nginx.conf
Generated configuration file: /config/core/env
Generated configuration file: /config/core/app.conf
Generated configuration file: /config/registry/config.yml
Generated configuration file: /config/registryctl/env
Generated configuration file: /config/registryctl/config.yml
Generated configuration file: /config/db/env
Generated configuration file: /config/jobservice/env
Generated configuration file: /config/jobservice/config.yml
loaded secret from file: /data/secret/keys/secretkey
Generated configuration file: /config/clair/postgres_env
Generated configuration file: /config/clair/config.yaml
Generated configuration file: /config/clair/clair_env
Generated configuration file: /config/clair-adapter/env
Generated configuration file: /compose_location/docker-compose.yml
Clean up the input dir
重启启动harbor服务(注意这里要指定docker-compose.yaml文件)
docker-compose down
Stopping harbor-jobservice ... done
Stopping nginx ... done
Stopping harbor-core ... done
Stopping redis ... done
Stopping registryctl ... done
Stopping registry ... done
Stopping harbor-db ... done
Stopping harbor-portal ... done
Stopping harbor-log ... done
Removing harbor-jobservice ... done
Removing nginx ... done
Removing harbor-core ... done
Removing redis ... done
Removing registryctl ... done
Removing registry ... done
Removing harbor-db ... done
Removing harbor-portal ... done
Removing harbor-log ... done
Removing network harbor_harbor
Removing network harbor_harbor-clair
WARNING: Network harbor_harbor-clair not found.
docker-compose -f docker-compose.yml up -d
Creating network "harbor_harbor" with the default driver
Creating network "harbor_harbor-clair" with the default driver
Creating harbor-log ... done
Creating harbor-db ... done
Creating redis ... done
Creating registryctl ... done
Creating harbor-portal ... done
Creating registry ... done
Creating harbor-core ... done
Creating clair ... done
Creating clair-adapter ... done
Creating nginx ... done
Creating harbor-jobservice ... done
测试扫描
可以看到在项目里面已经显示安装好了扫描器插件,不安装这里是没有的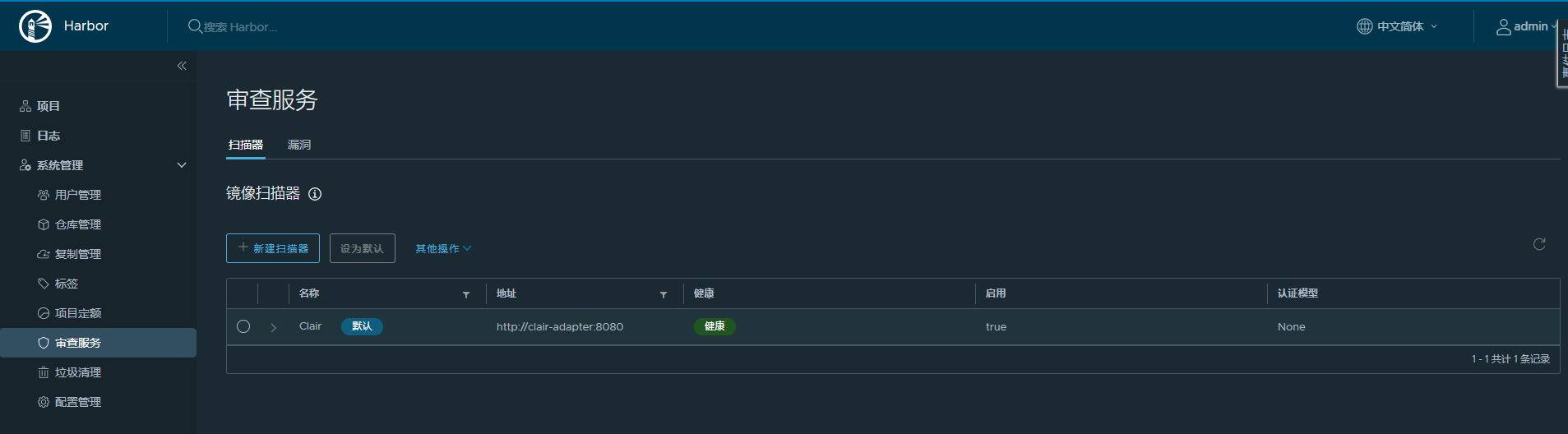
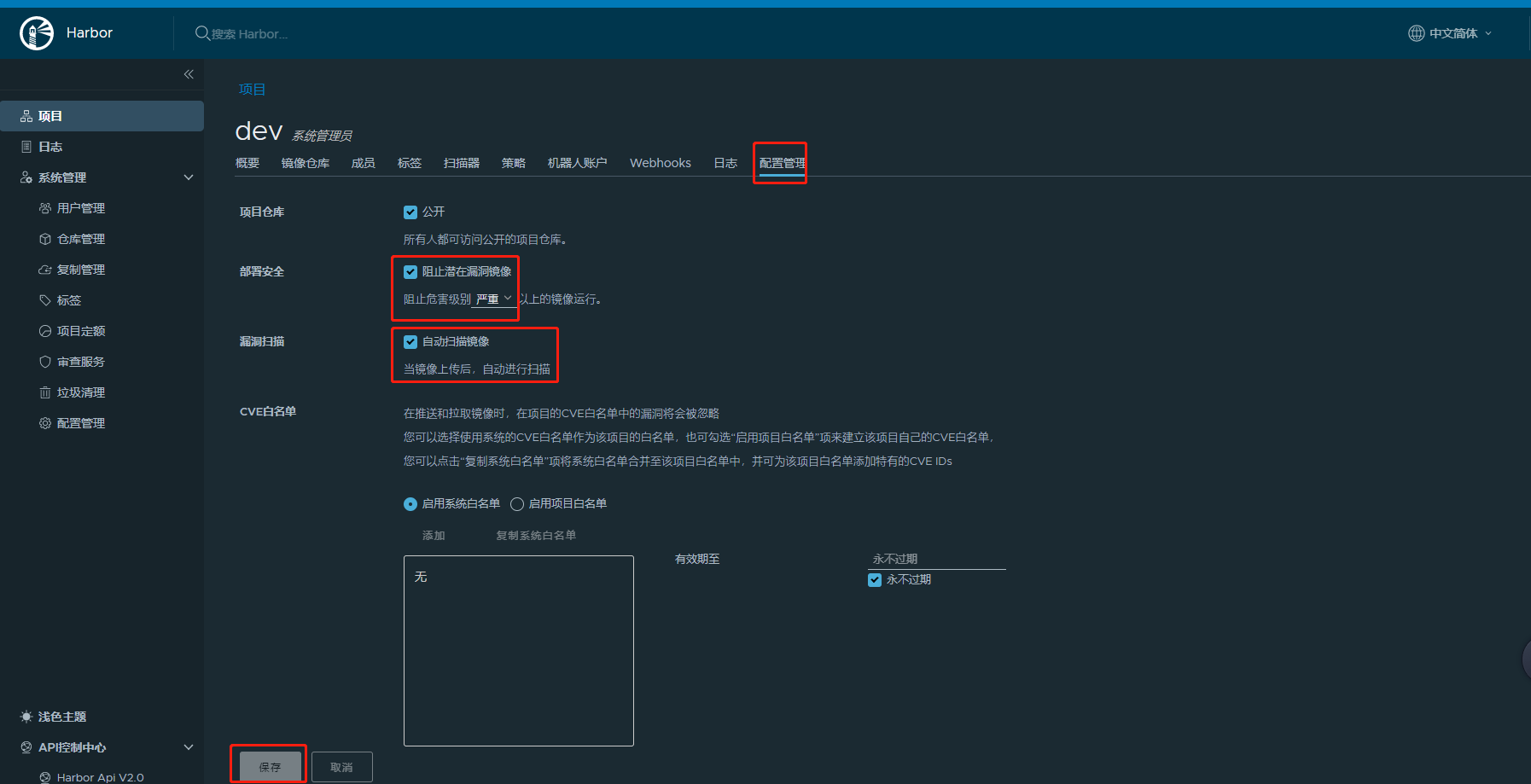
docker tag df_java reg.harbor.com/dev/df_java
docker push reg.harbor.com/dev/df_java
The push refers to repository [reg.harbor.com/dev/df_java]
ae8399399072: Pushed
86840743f5c8: Pushed
a1e7033f082e: Pushed
78075328e0da: Pushed
9f8566ee5135: Pushed
latest: digest: sha256:0c5886ed44504f08900a7a10327491e14b2d4d908cc2378b0770abb98db2a8c7 size: 1365
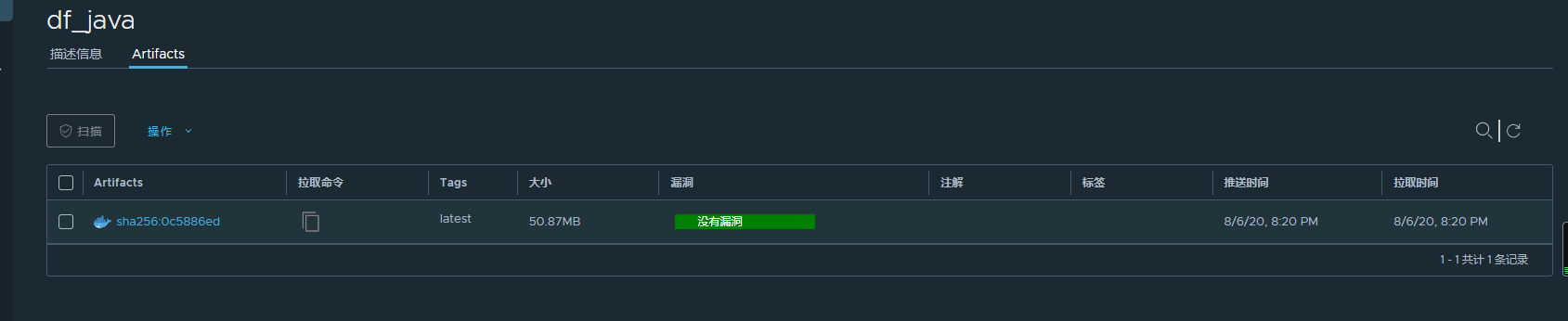
Harbor基本使用
1、配置http镜像仓库可信任
vi /etc/docker/daemon.json
{
"registry-mirrors": ["https://b9pmyelo.mirror.aliyuncs.com"],
"insecure-registries": ["reg.harbor.com"]
}
systemctl restart docker
2、打标签
docker tag centos:7 reg.harbor.com/library/centos:7
3、上传
docker push reg.harbor.com/library/centos:7
4、下载
docker pull reg.harbor.com/library/centos:7
Harbor运维
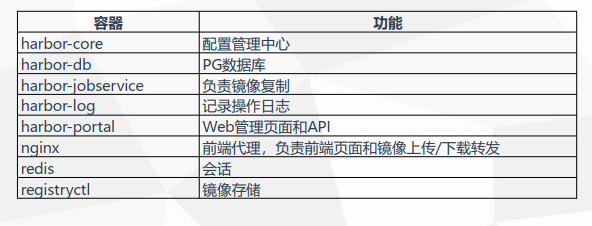
容器数据持久化目录:/data
日志文件目录:/var/log/harbor

