1.安装环境依赖
注意:此工具环境基于Python3
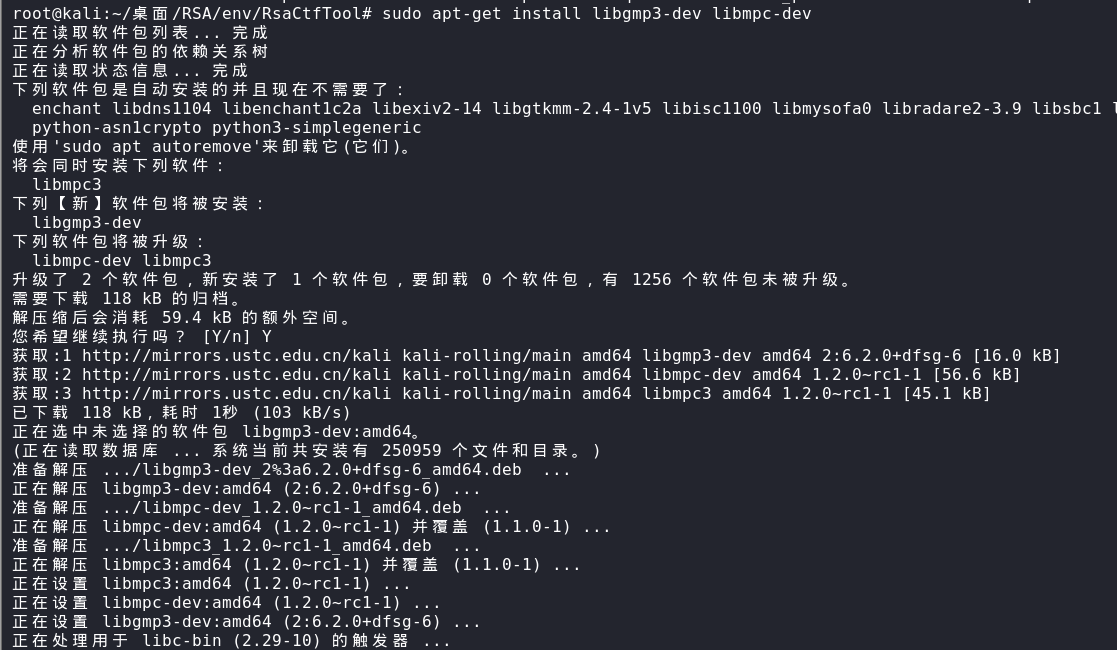
root@kali:~/桌面/RSA/env/RsaCtfTool# sudo apt-get install libgmp3-dev libmpc-dev
2.安装python支持库,这里使用的是python3
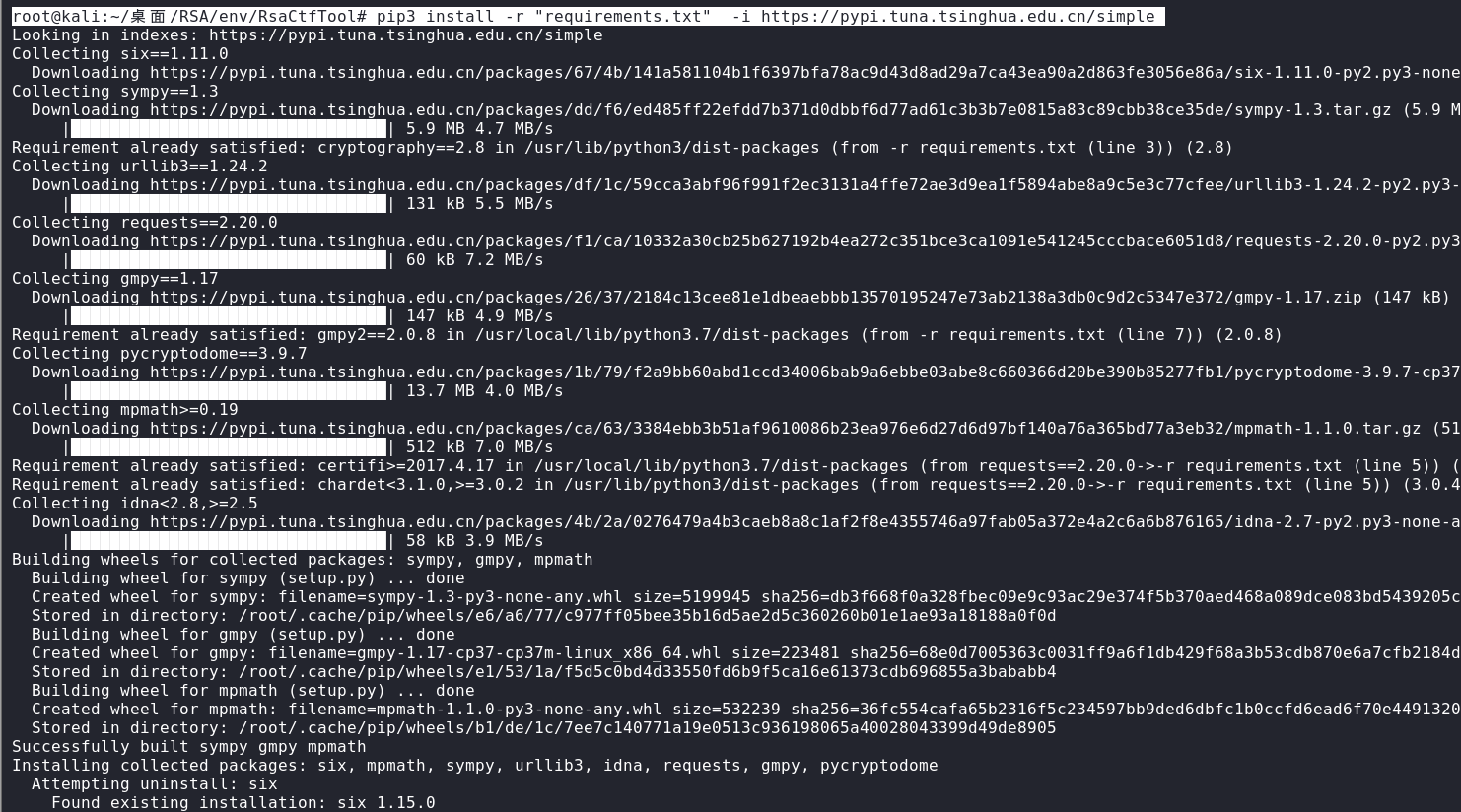
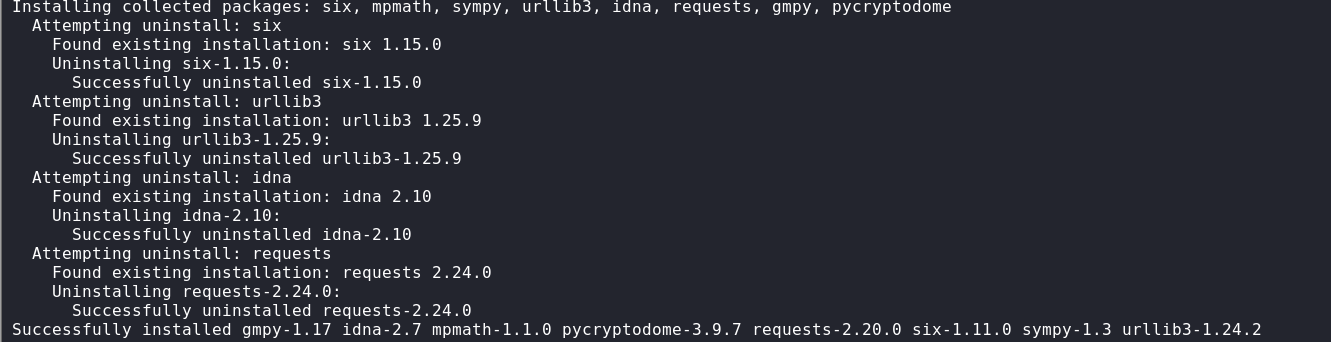
root@kali:~/桌面/RSA/env/RsaCtfTool# pip3 install -r "requirements.txt" -i https://pypi.tuna.tsinghua.edu.cn/simple
3.验证一下,是否安装成功
root@kali:~/桌面/RSA/env/RsaCtfTool# python3 RsaCtfTool.py
usage: RsaCtfTool.py [-h] [--publickey PUBLICKEY] [--output OUTPUT]
[--timeout TIMEOUT] [--createpub] [--dumpkey] [--ext]
[--uncipherfile UNCIPHERFILE] [--uncipher UNCIPHER]
[--verbosity {CRITICAL,ERROR,WARNING,DEBUG,INFO}]
[--private] [--ecmdigits ECMDIGITS] [-n N] [-p P] [-q Q]
[-e E] [--key KEY] [--password PASSWORD]
[--attack {boneh_durfee,roca,pollard_p_1,noveltyprimes,smallfraction,comfact_cn,pastctfprimes,siqs,smallq,ecm,primefac,mersenne_primes,partial_q,ecm2,factordb,londahl,fermat,wiener,qicheng,cube_root,hastads,same_n_huge_e,commonfactors,all}]
RSA CTF Tool
optional arguments:
-h, --help show this help message and exit
--publickey PUBLICKEY
public key file. You can use wildcards for multiple
keys.
--output OUTPUT output file for results (privates keys, plaintext
data).
--timeout TIMEOUT Timeout for long attacks.
--createpub Take n and e from cli and just print a public key then
exit
--dumpkey Just dump the RSA variables from a key - n,e,d,p,q
--ext Extended dump of RSA private variables in --dumpkey
mode - dp,dq,pinv,qinv).
--uncipherfile UNCIPHERFILE
uncipher a file
--uncipher UNCIPHER uncipher a cipher
--verbosity {CRITICAL,ERROR,WARNING,DEBUG,INFO}
verbose mode
--private Display private key if recovered
--ecmdigits ECMDIGITS
Optionally an estimate as to how long one of the
primes is for ECM method
-n N Specify the modulus. format : int or 0xhex
-p P Specify the first prime number. format : int or 0xhex
-q Q Specify the second prime number. format : int or 0xhex
-e E Specify the public exponent. format : int or 0xhex
--key KEY Specify the private key file.
--password PASSWORD Private key password if needed.
--attack {boneh_durfee,roca,pollard_p_1,noveltyprimes,smallfraction,comfact_cn,pastctfprimes,siqs,smallq,ecm,primefac,mersenne_primes,partial_q,ecm2,factordb,londahl,fermat,wiener,qicheng,cube_root,hastads,same_n_huge_e,commonfactors,all}
Specify the attack mode.
4.用法
1). 已知公钥(自动求私钥) –publickey,密文 — uncipherfile
此题以攻防世界中级区—wtc_rsa_bbq为例
将文件解压复制到RsaCtfTool里:(或者指定路径)
root@kali:~/桌面/RSA/env/RsaCtfTool# python3 RsaCtfTool.py --publickey /root/桌面/_cry200.extracted/key.pem --uncipherfile /root/桌面/_cry200.extracted/cipher.bin
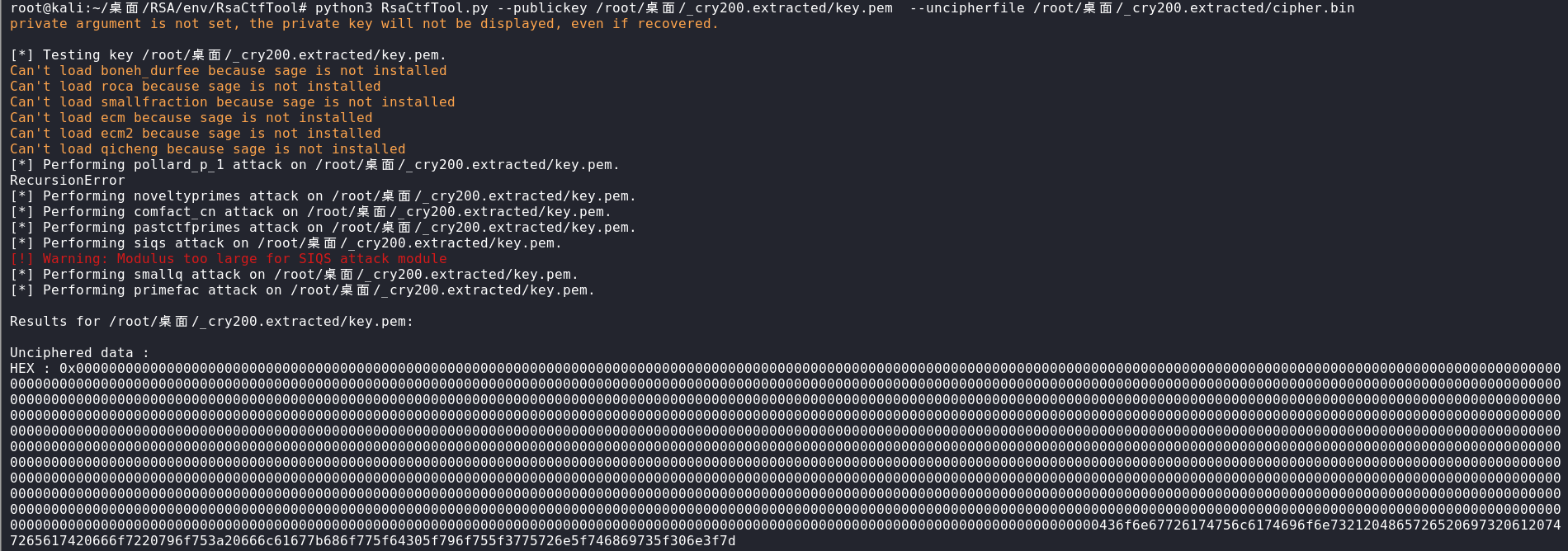
解密的16进制信息如上图,往后翻一点可以看到flag,其实丢入Hxd也是一样的效果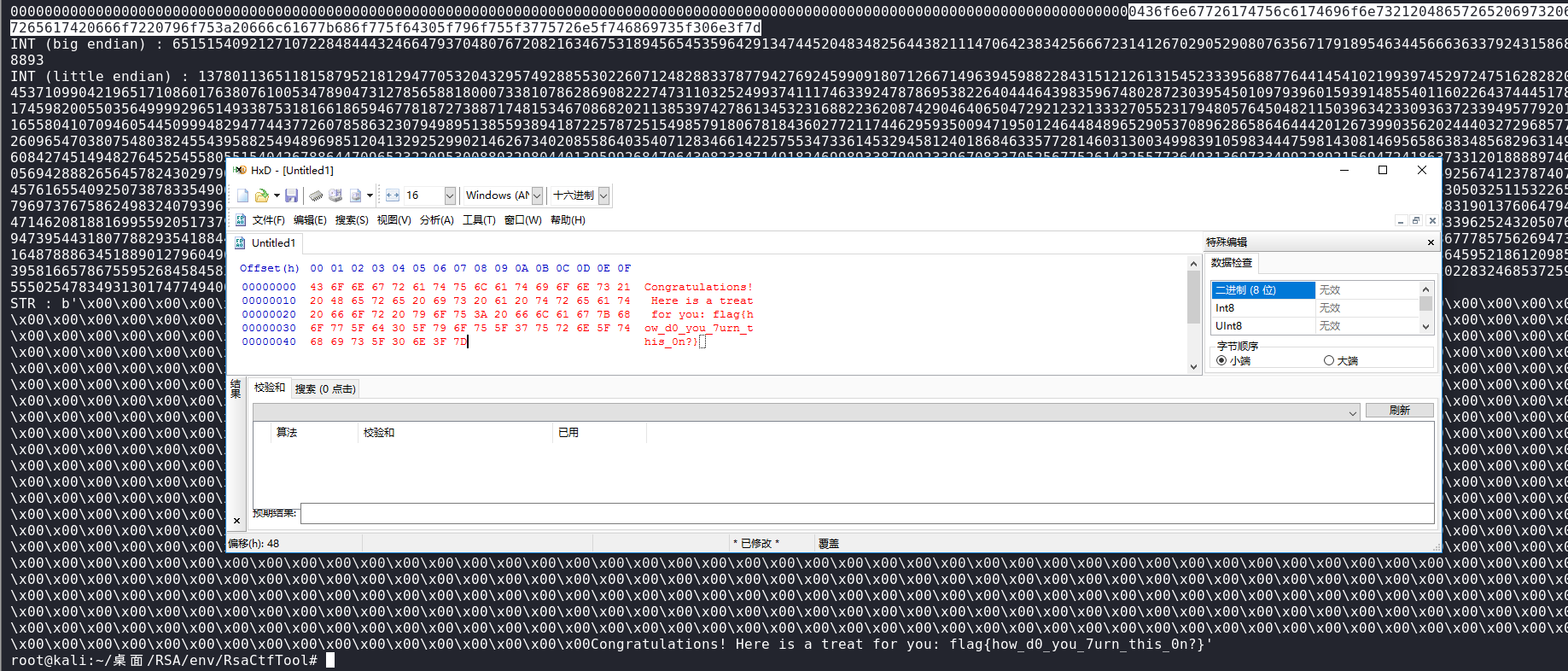
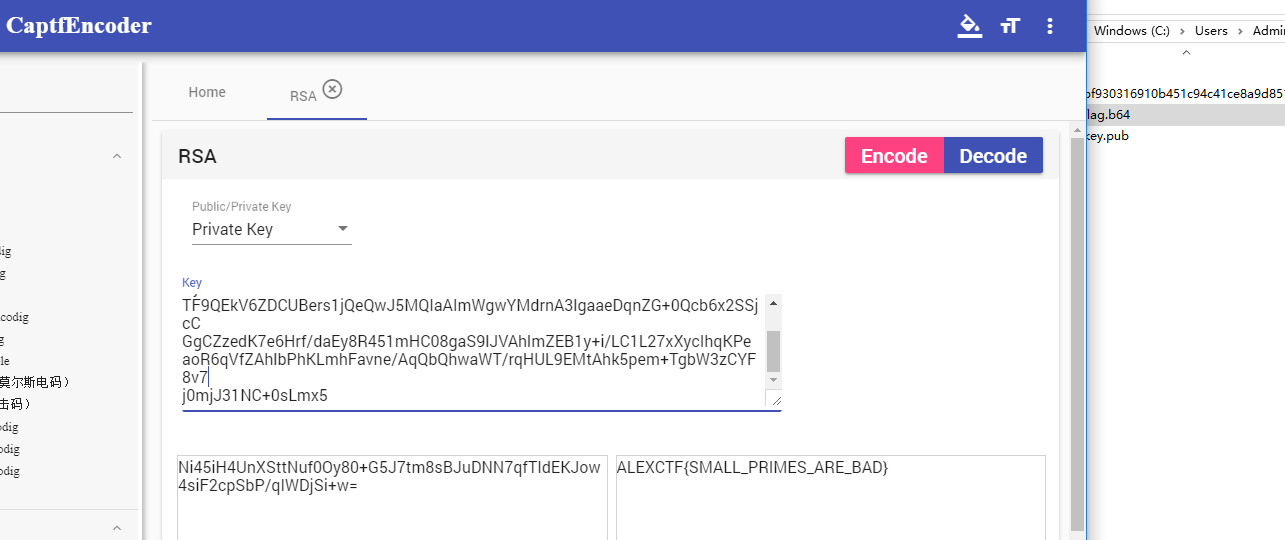
2)已知公钥求私钥(cr4-poor-rsa 攻防世界)
python3 RsaCtfTool.py --publickey 公钥文件 --private
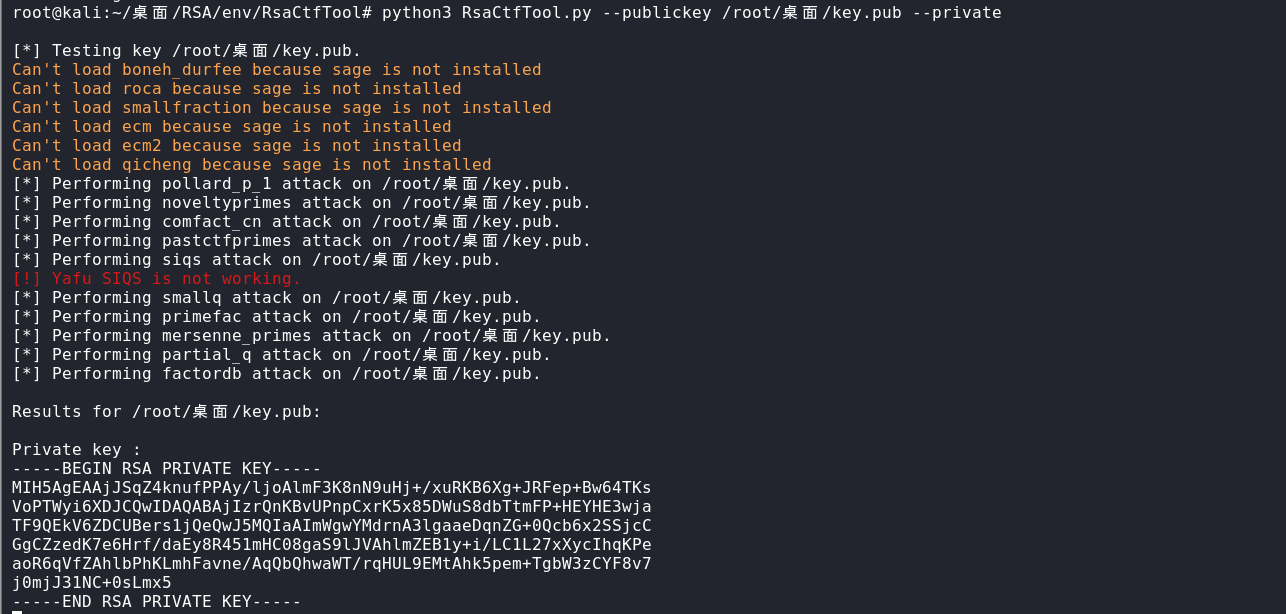
由此计算出私钥为:
-----BEGIN RSA PRIVATE KEY-----
MIH5AgEAAjJSqZ4knufPPAy/ljoAlmF3K8nN9uHj+/xuRKB6Xg+JRFep+Bw64TKs
VoPTWyi6XDJCQwIDAQABAjIzrQnKBvUPnpCxrK5x85DWuS8dbTtmFP+HEYHE3wja
TF9QEkV6ZDCUBers1jQeQwJ5MQIaAImWgwYMdrnA3lgaaeDqnZG+0Qcb6x2SSjcC
GgCZzedK7e6Hrf/daEy8R451mHC08gaS9lJVAhlmZEB1y+i/LC1L27xXycIhqKPe
aoR6qVfZAhlbPhKLmhFavne/AqQbQhwaWT/rqHUL9EMtAhk5pem+TgbW3zCYF8v7
j0mjJ31NC+0sLmx5
-----END RSA PRIVATE KEY-----
由于加密信息给的是一段base64(这里可以直接将base64转换为一个文件,再使用Openssl 解密rsa),为方便所以这里使用CaptfEncoder进行解密RSA: