0x01 Hook整体框架代码
import frida,sysjscode = """Java.perform(function () {// hook构造函数var auto = Java.use('com.dongchedi.cisn.policy.AutoPrivacyPolicyDialog');auto.$init.implementation = function(obj){send("Hook start...");return this.$init(obj);}// hook普通函数var test = Java.use('com.dongchedi.cisn.policy.Utils');test.getCalc.implementation = function(a,b){console.log("Hook start....");return this.getCalc(a,b);}// hook重载函数var add = Java.use('com.dongchedi.cisn.policy.Utils');add.addCalc.overload("int","java.lang.String").implementation = function(a,b){console.log("Hook start....");return this.getCalc(a,b);}// 调用其它类方法var cls = Java.use('com.dongchedi.cisn.policy.Cls');var test = Java.use('com.dongchedi.cisn.policy.Utils');test.getCalc.implementation = function(a,b){console.log("Hook start....");var c = cls.new();send(c.test());// 修改类的值test.name.value = 123;return this.getCalc(a,b);}});"""def message(message,data):if message["type"] == 'send':print("[*] {0}".format(message['payload']))else:print(message)# process = frida.get_remote_device().attach('pingan2')# 当使用get_remote_device需要开启端口转发,语句如下:# adb forward tcp:27043 tcp:27043# adb forward tcp:27042 tcp:27042# 很多情况下进程名与包名并不相同,需要使用frida-ps查看进程名进行hookprocess = frida.get_usb_device().attach('com.dongchedi.cisn.android')script = process.create_script(jscode)script.on("message",message)script.load()sys.stdin.read()
0x02 Hook native层代码
1)有导出的so层函数
可以直接在导出表查看导出函数名,进行hook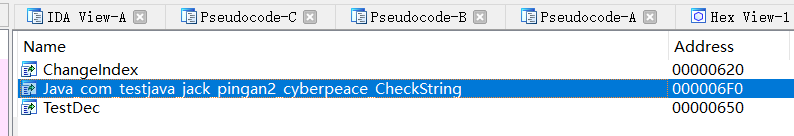
hook脚本:
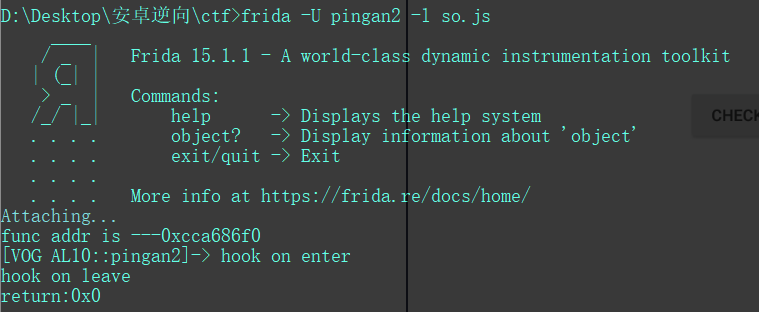
var str_name_so = "libcyberpeace.so"; //要hook的so名var str_name_func = "Java_com_testjava_jack_pingan2_cyberpeace_CheckString";//要hook的函数名var n_addr_func = Module.findExportByName(str_name_so , str_name_func);console.log("func addr is ---" + n_addr_func);Interceptor.attach(n_addr_func, {//在hook函数之前执行的语句onEnter: function(args){console.log("hook on enter")},//在hook函数之后执行的语句onLeave:function(retval){console.log("hook on leave");console.log("return:"+retval); //返回值retval.replace(1); //替换返回值为100}});
2)无导出的so层函数
无法通过函数名找到该函数,只能通过字符串或者上下级调用手工找到偏移地址。
hook脚本:
var str_name_so = "libcyberpeace.so"; //要hook的so名var n_addr_func_offset = 0x000006F0; //需要hook的函数的偏移var n_addr_so = Module.findBaseAddress(str_name_so);//加载到内存后 函数地址 = so地址+函数偏移var n_addr_func = parseInt(n_addr_so, 16) + n_addr_func_offset;var n_addr_func = new NativePointer(n_addr_func);console.log("func addr is ---" + n_addr_func);Interceptor.attach(n_addr_func, {//在hook函数之前执行的语句onEnter: function(args){console.log("hook on enter")},//在hook函数之后执行的语句onLeave:function(retval){console.log("hook on leave");console.log("return:"+retval); //返回值retval.replace(1); //替换返回值为100}});