For IT professionals using SCCM or MDT for Windows 10 / Server OS deployment, you may experience failures during the domain join process of your task sequence. Typically, the computer account fails to join the OU because the OU(s) don’t have the correct join account permissions set. Often, when working with customers I see that their Active Directory domain join service account permissions are incorrectly configured. In some cases, customers are using a DOMAIN ADMIN account which is a bad security best practice.
This article outlines the proper permissions you need to set to for an Active Directory domain join service account for use during the Windows OS deployment task sequence.
IMPORTANT NOTE: It is not a security best practice to use a DOMAIN ADMIN account for joining systems to the domain as this is a domain-wide account with access to every server and computer typically. Also, domain admin accounts usually have access to many other Windows resources within the Active Directory domain. For these reasons and more, the least privilege account approach should always be used instead.
Requirements
Create a standard user domain account (new accounts are better to ensure they’re not used by anything else but the auto domain join process)
Set the password to a strong password that includes upper/lower case, symbols, etc.
username examples: djoin or domainjoin
Set the service account password to “PASSWORD NEVER EXPIRES”
Applies to Server 2019 or Server 2016 Domain Controllers
Note: If using Server 2012 Domain Functional Level, the screens will look slightly different on the permissions page. See older pics later in this article for Server 2012.
Create OU(s) where you intend to automatically join systems to and plan to set permissions on these OUs – better yet the parent OU if you have several child OUs
Requires setting 2 different “Applies To” scopes for “This object and all descendant objects” and “Descendant Computer Objects” or the service account join process will fail. Pay special attention to the specifics below.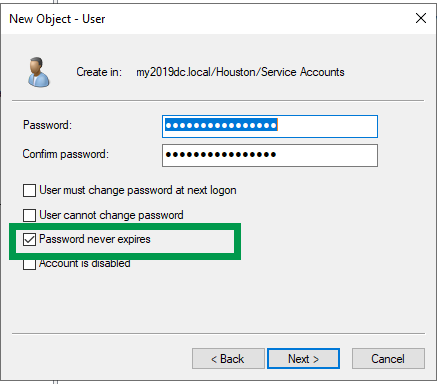
If creating a NEW domain join service account make sure to set “Password never expires” and UN-CHECK “User must change password at next logon.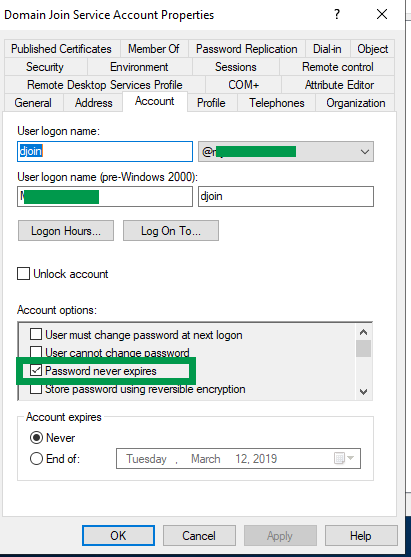
Confirm “Password Never Expires” is checked and “Account expires” is set to “NEVER”.
Step-by-Step: Set Permissions For The Service Account
Launch Active Directory Users and Computers, click on the “View” Menu and on the drop down, check the “Advanced Features” option.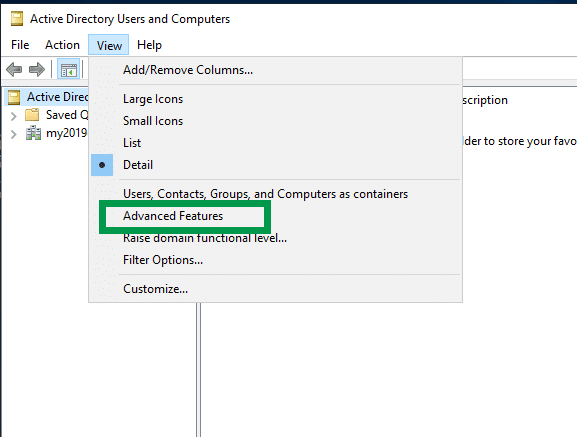
Navigate to the OU, right-click on your target OU and select “Properties“.
Note: It’s recommended to set permissions on the parent OU depending on the companies OU structure. This helps avoid setting permissions on multiple OUs for each location. Typically, creating a Root / top-level OU called “Workstations” or “Servers” is a good start.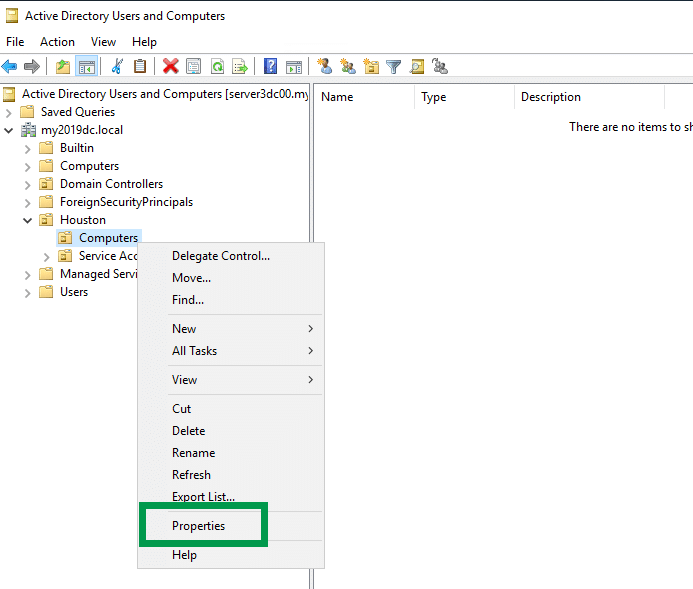
From the properties page, click on the “Security” Tab, “Advanced” button on the bottom and click the “Add” button.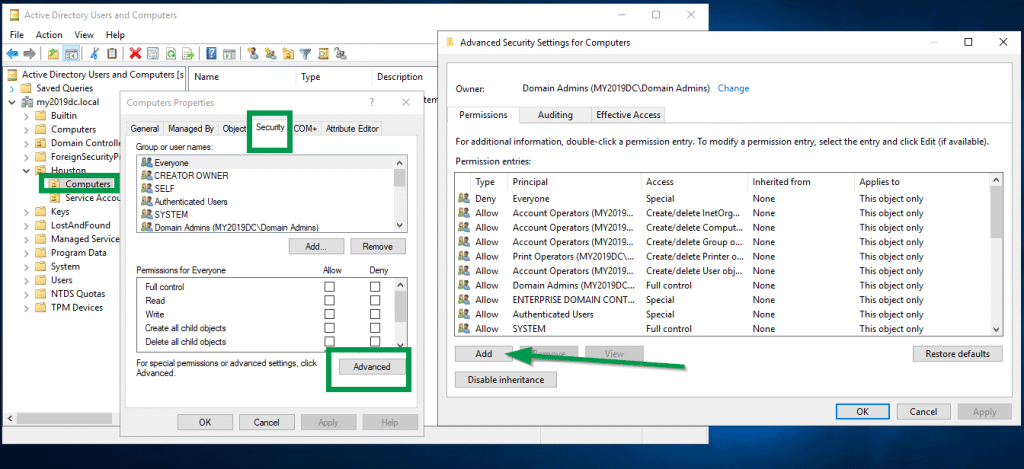
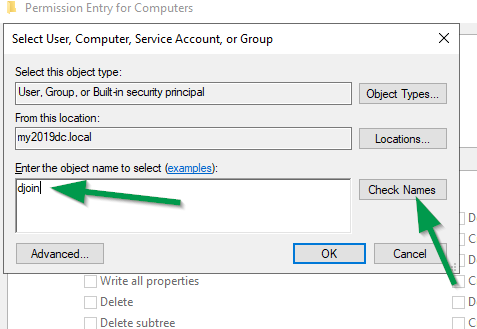
Click on the “Select a principal” link on the top and type the name of the service account previously created, click “Check Names” to confirm and click “Ok”.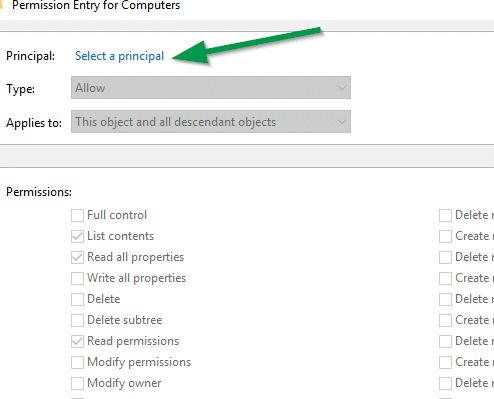
From the “Applies to” dropdown, lect “This object and all descendant objects” and check the 2 boxes for “Create Computer Object” and “Delete Computer Object“. Click “Ok” to save changes.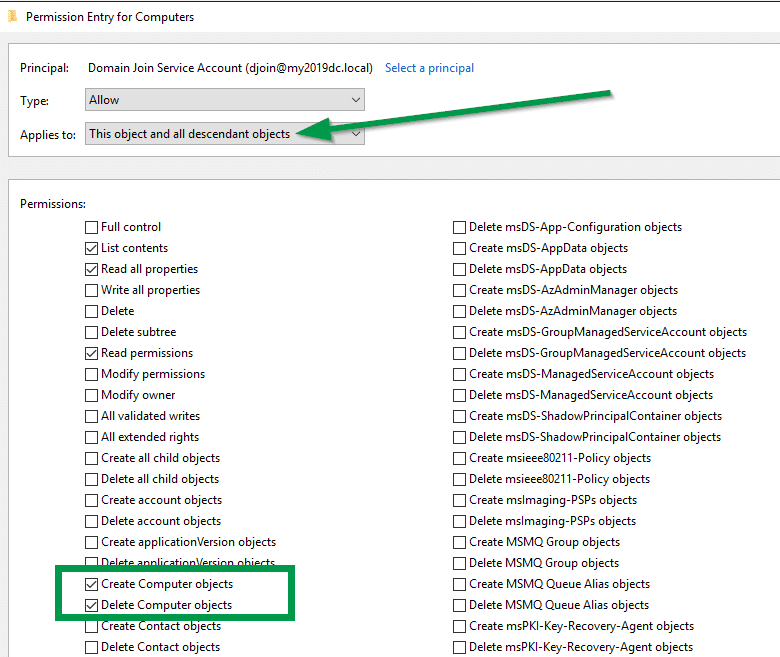
Click the “Add” button again, click the “Select a principal” and enter the service account again, check the name and click OK again. Change the “Applies to” to “Descendant Computer Objects“.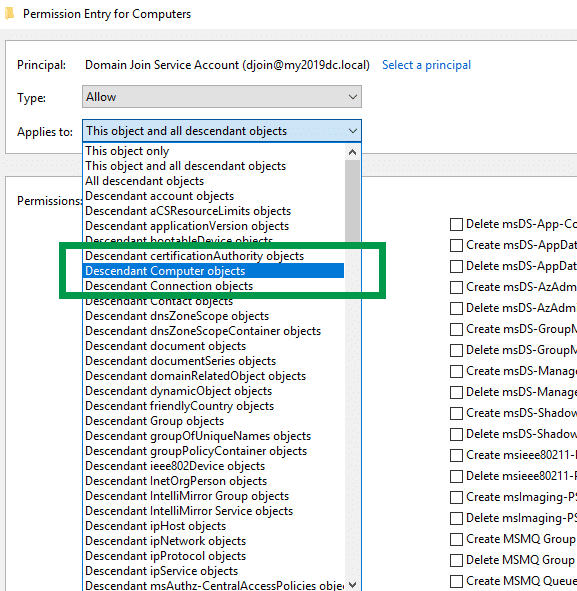
Check the following options for the “Descendant Computer Objects” > “Applies to“, click “Ok” 3 times to save all changes.
Read All Properties
Write All Properties
Read Permissions
Modify Permissions
Change Password
Reset Password
Validate Write to DNS hostname
Validate Write to Service Principal Name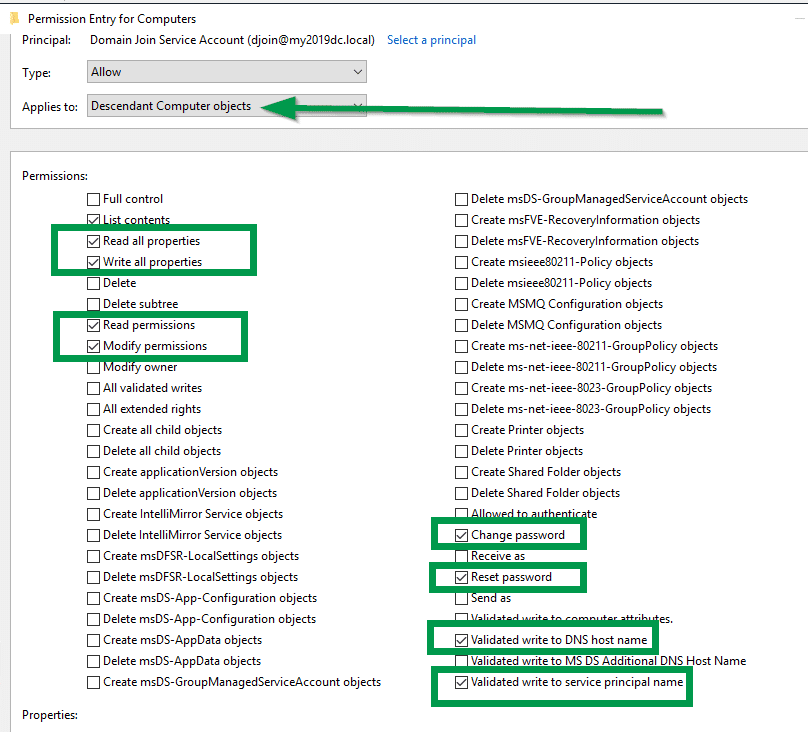
Legacy: Server 2012 functional domain Look and Feel
For Server 2012 the screens will look slightly different for the 2 sets of permissions but be sure to set the same permissions as shown above.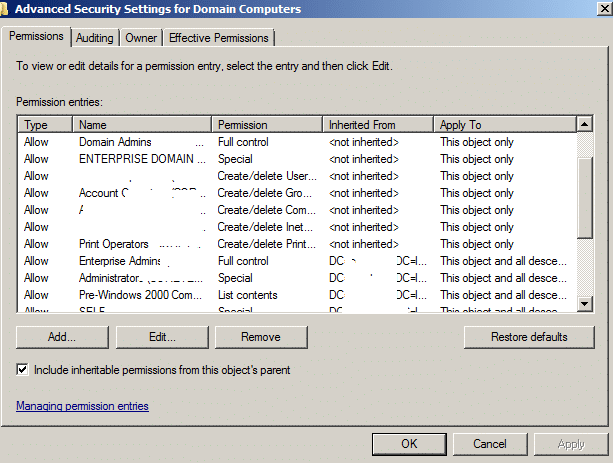
Add screen looks slightly different for Server 2012 Domain Functional Level.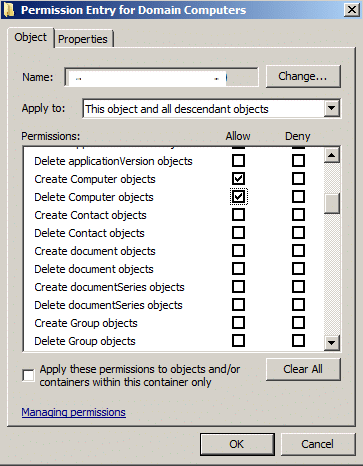
Create and Delete Computer object for “This object and all descendant objects” Apply to.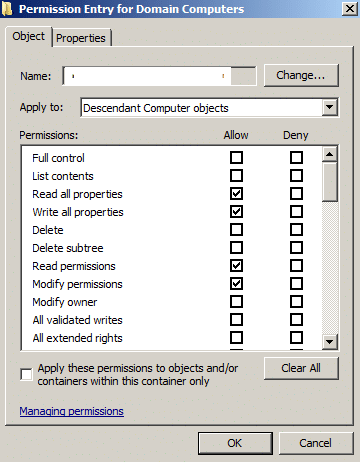
Make sure to also check “Validate write to Service Principal Name“.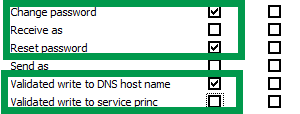
That completes this guide to correctly set the domain service account for the computer join process. Test and add the service account to the OS Deployment task sequences steps for MDT or SCCM.
Troubleshoot: Computer Join Failures
To troubleshoot issues with the join process, use Microsoft CMtrace Utility or notepad to review the “NetSetup.log” located at C:\Windows\Debug.
References
Strong Password Generator:
https://passwordsgenerator.net/
Microsoft CMTrace .log file viewer download:
https://www.microsoft.com/en-us/download/details.aspx?id=50012

