Orz 最近碰到的几道题都是用到了它,出师不利2333
IO_FILE相关结构
覆盖 _IO_list_all (全局变量) 指向伪造的结构,然后改写 vtable 指针来 getshell
FILE 结构在程序执行 fopen 的时候动态创建并且分配在堆中
_IO_FILE 结构体
struct _IO_FILE {int _flags; /* High-order word is _IO_MAGIC; rest is flags. */#define _IO_file_flags _flags/* The following pointers correspond to the C++ streambuf protocol. *//* Note: Tk uses the _IO_read_ptr and _IO_read_end fields directly. */char* _IO_read_ptr; /* Current read pointer */char* _IO_read_end; /* End of get area. */char* _IO_read_base; /* Start of putback+get area. */char* _IO_write_base; /* Start of put area. */char* _IO_write_ptr; /* Current put pointer. */char* _IO_write_end; /* End of put area. */char* _IO_buf_base; /* Start of reserve area. */char* _IO_buf_end; /* End of reserve area. *//* The following fields are used to support backing up and undo. */char *_IO_save_base; /* Pointer to start of non-current get area. */char *_IO_backup_base; /* Pointer to first valid character of backup area */char *_IO_save_end; /* Pointer to end of non-current get area. */struct _IO_marker *_markers;struct _IO_FILE *_chain;int _fileno;#if 0int _blksize;#elseint _flags2;#endif_IO_off_t _old_offset; /* This used to be _offset but it's too small. */#define __HAVE_COLUMN /* temporary *//* 1+column number of pbase(); 0 is unknown. */unsigned short _cur_column;signed char _vtable_offset;char _shortbuf[1];/* char* _save_gptr; char* _save_egptr; */_IO_lock_t *_lock;#ifdef _IO_USE_OLD_IO_FILE};
然后通过 _chain 连接成一个链表,全局变量 _IO_list_all 指向链表头部
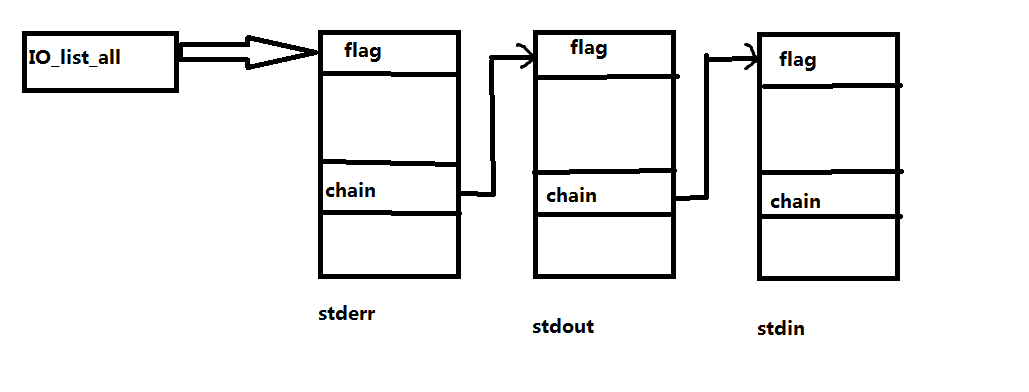
实际上在 IO_FILE 结构体是包含在一个叫 _IO_FILE_plus 中的
struct _IO_FILE_plus{_IO_FILE file;IO_jump_t *vtable;}
里面还有个 IO_jump_t 类型的指针 vtable
struct _IO_jump_t{JUMP_FIELD(size_t, __dummy);JUMP_FIELD(size_t, __dummy2);JUMP_FIELD(_IO_finish_t, __finish);JUMP_FIELD(_IO_overflow_t, __overflow);JUMP_FIELD(_IO_underflow_t, __underflow);JUMP_FIELD(_IO_underflow_t, __uflow);JUMP_FIELD(_IO_pbackfail_t, __pbackfail);/* showmany */JUMP_FIELD(_IO_xsputn_t, __xsputn);JUMP_FIELD(_IO_xsgetn_t, __xsgetn);JUMP_FIELD(_IO_seekoff_t, __seekoff);JUMP_FIELD(_IO_seekpos_t, __seekpos);JUMP_FIELD(_IO_setbuf_t, __setbuf);JUMP_FIELD(_IO_sync_t, __sync);JUMP_FIELD(_IO_doallocate_t, __doallocate);JUMP_FIELD(_IO_read_t, __read);JUMP_FIELD(_IO_write_t, __write);JUMP_FIELD(_IO_seek_t, __seek);JUMP_FIELD(_IO_close_t, __close);JUMP_FIELD(_IO_stat_t, __stat);JUMP_FIELD(_IO_showmanyc_t, __showmanyc);JUMP_FIELD(_IO_imbue_t, __imbue);#if 0get_column;set_column;#endif};
伪造 vtable 劫持程序流程
linux 中常见的 IO 函数都需要经过 FILE 结构体进行处理,尤其是 IO_FILE_plus 结构体中的 vtable,一些函数会取出 vtable 中的指针进行调用
所以这种攻击方法的核心思想是:对 _IO_FILE_plus 的 vtable 动手脚,通过把 vtable 指向我们控制的内存,并在其中布置函数指针来实现
攻击方法有两种:一种是通过任意地址写改写 vtable 中的函数指针
一种是覆盖 vtable 的指针指向我们控制的内存,然后在上面布置函数指针
FSOP
前面的 house of orange 用的就是这种方法来 getshell 的
语雀内容

