行为1:setup.exe创建了spoclsv.exe这样一个程序
行为2:删除了c盘和admin用户文件夹的默认共享(不考虑)
行为3:删除了安全类软件的自启动项(用户自行重装杀毒软件,不考虑)
行为4:在run键下创建了一个svcshare的自启动项,每次开机时病毒自动运行
行为5:在注册表下修改hidden\showall和hidden\showall\checkvalue两个键达到在文件管理器中即使查看隐藏文件夹也无法显现病毒
行为6:将自身拷贝c盘根目录下命名为setup.exe,并且创建autorun.inf用于病毒的启动
行为7:在某些文件夹中创建Desktop_.ini这样的文件
行为8:向内网外网发送数据,并连接局域网中的其他电脑(删除病毒本体解决,不考虑)
新建mfc程序
CRC32():计算病毒程序的散列值
DWORD CRC32(BYTE* ptr,DWORD Size){DWORD crcTable[256],crcTmp1;//动态生成CRC-32表for (int i=0; i<256; i++){crcTmp1 = i;for (int j=8; j>0; j--){if (crcTmp1&1) crcTmp1 = (crcTmp1 >> 1) ^ 0xEDB88320L;else crcTmp1 >>= 1;}crcTable[i] = crcTmp1;}//计算CRC32值DWORD crcTmp2= 0xFFFFFFFF;while(Size--){crcTmp2 = ((crcTmp2>>8) & 0x00FFFFFF) ^ crcTable[ (crcTmp2^(*ptr)) & 0xFF ];ptr++;}return (crcTmp2^0xFFFFFFFF);}
FindVirProcess():查找病毒进程
BOOL FindVirProcess(char *pszProcessName,DWORD *dwPid){BOOL bFind = FALSE;HANDLE hProcessSnap = CreateToolhelp32Snapshot(TH32CS_SNAPPROCESS,0);if (hProcessSnap == INVALID_HANDLE_VALUE){return bFind;}PROCESSENTRY32 pe = { 0 };pe.dwSize = sizeof(pe);BOOL bRet = Process32First(hProcessSnap,&pe);while (bRet){if (lstrcmp(pe.szExeFile,pszProcessName) == 0){*dwPid = pe.th32ProcessID;bFind = TRUE;break;}bRet = Process32Next(hProcessSnap,&pe);}CloseHandle(hProcessSnap);return bFind;}
EnableDebugerPrivilege提升权限
BOOL EnableDebugPrivilege(char *pszPrivilege){HANDLE hToken = INVALID_HANDLE_VALUE;LUID luid;TOKEN_PRIVILEGES tp;BOOL bRet = OpenProcessToken(GetCurrentProcess(),TOKEN_ADJUST_PRIVILEGES | TOKEN_QUERY,&hToken);if (bRet == FALSE){return bRet;}bRet = LookupPrivilegeValue(NULL,pszPrivilege,&luid);if (bRet == FALSE){return bRet;}tp.PrivilegeCount = 1;tp.Privileges[0].Luid = luid;tp.Privileges[0].Attributes = SE_PRIVILEGE_ENABLED;bRet = AdjustTokenPrivileges(hToken,FALSE,&tp,sizeof(tp),NULL,NULL);return bRet;}
FindFiles():删除Desktop_.ini文件
DWORD WINAPI FindFiles(LPVOID lpszPath){WIN32_FIND_DATA stFindFile;HANDLE hFindFile;// 扫描路径char szPath[MAX_PATH];char szFindFile[MAX_PATH];char szSearch[MAX_PATH];char *szFilter;int len;int ret = 0;szFilter = "*.*";lstrcpy(szPath, (char *)lpszPath);len = lstrlen(szPath);if(szPath[len-1] != '\\'){szPath[len] = '\\';szPath[len+1] = '\0';}lstrcpy(szSearch, szPath);lstrcat(szSearch,szFilter);hFindFile = FindFirstFile(szSearch, &stFindFile);if(hFindFile != INVALID_HANDLE_VALUE){do{lstrcpy(szFindFile, szPath);lstrcat(szFindFile, stFindFile.cFileName);if(stFindFile.dwFileAttributes & FILE_ATTRIBUTE_DIRECTORY){if(stFindFile.cFileName[0] != '.'){FindFiles(szFindFile);}}else{if(!lstrcmp(stFindFile.cFileName,"Desktop_.ini")){// 去除文件的隐藏、系统以及只读属性DWORD dwFileAttributes = GetFileAttributes(szFindFile);dwFileAttributes &= ~FILE_ATTRIBUTE_HIDDEN;dwFileAttributes &= ~FILE_ATTRIBUTE_SYSTEM;dwFileAttributes &= ~FILE_ATTRIBUTE_READONLY;SetFileAttributes(szFindFile, dwFileAttributes);// 删除Desktop_.iniBOOL bRet = DeleteFile(szFindFile);csTxt += szFindFile;if (bRet){csTxt += _T("被删除!\r\n");}else{csTxt += _T("无法删除\r\n");}}}ret = FindNextFile(hFindFile, &stFindFile);}while(ret != 0);}FindClose(hFindFile);return 0;}
OnBtnKill():主程序
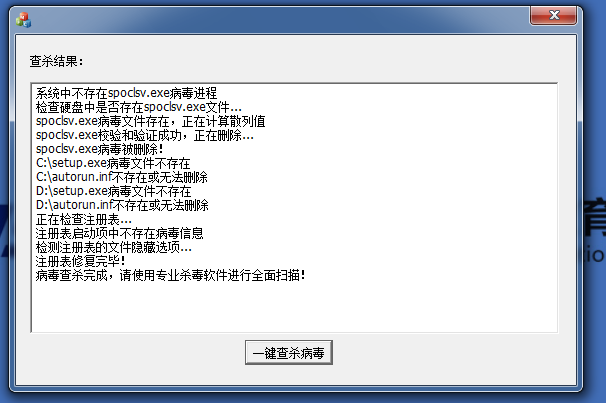
void CKillWhBoyDlg::OnBtnKill(){// TODO: Add your control notification handler code hereBOOL bRet = FALSE;DWORD dwPid = 0;///// 结束spoclsv.exe进程,并删除病毒程序本身///bRet = FindTargetProcess("spoclsv.exe", &dwPid);if (bRet == TRUE){csTxt = _T("检查系统内存...\r\n");csTxt += _T("系统中存在病毒进程:spoclsv.exe\r\n");csTxt += _T("准备进行查杀...\r\n");SetDlgItemText(IDC_LIST,csTxt);// 提升权限bRet = EnableDebugPrivilege(SE_DEBUG_NAME);if (bRet == FALSE){csTxt += _T("提升权限失败\r\n");}else{csTxt += _T("提升权限成功!\r\n");}SetDlgItemText(IDC_LIST,csTxt);// 打开并尝试结束病毒进程HANDLE hProcess = OpenProcess(PROCESS_ALL_ACCESS,FALSE,dwPid);if (hProcess == INVALID_HANDLE_VALUE){csTxt += _T("无法结束病毒进程\r\n");return ;}bRet = TerminateProcess(hProcess,0);if (bRet == FALSE){csTxt += _T("无法结束病毒进程\r\n");return ;}csTxt += _T("病毒进程已经结束\r\n");SetDlgItemText(IDC_LIST,csTxt);CloseHandle(hProcess);}else{csTxt += _T("系统中不存在spoclsv.exe病毒进程\r\n");}Sleep(10);// 查杀磁盘中是否存在名为spoclsv.exe的病毒文件char szSysPath[MAX_PATH] = { 0 };GetSystemDirectory(szSysPath,MAX_PATH);lstrcat(szSysPath,"\\drivers\\spoclsv.exe");csTxt += _T("检查硬盘中是否存在spoclsv.exe文件...\r\n");if (GetFileAttributes(szSysPath) == 0xFFFFFFFF){csTxt += _T("spoclsv.exe病毒文件不存在\r\n");}else{csTxt += _T("spoclsv.exe病毒文件存在,正在计算散列值\r\n");HANDLE hFile = CreateFile(szSysPath,GENERIC_READ,FILE_SHARE_READ,NULL,OPEN_EXISTING,FILE_ATTRIBUTE_NORMAL,NULL);if (hFile == INVALID_HANDLE_VALUE){AfxMessageBox("Create Error");return ;}DWORD dwSize = GetFileSize(hFile,NULL);if (dwSize == 0xFFFFFFFF){AfxMessageBox("GetFileSize Error");return ;}BYTE *pFile = (BYTE*)malloc(dwSize);if (pFile == NULL){AfxMessageBox("malloc Error");return ;}DWORD dwNum = 0;ReadFile(hFile,pFile,dwSize,&dwNum,NULL);// 计算spoclsv.exe的散列值DWORD dwCrc32 = CRC32(pFile,dwSize);if (pFile != NULL){free(pFile);pFile = NULL;}CloseHandle(hFile);// 0x89240FCD是“熊猫烧香”病毒的散列值if (dwCrc32 != 0x89240FCD){csTxt += _T("spoclsv.exe校验和验证失败\r\n");}else{csTxt += _T("spoclsv.exe校验和验证成功,正在删除...\r\n");// 去除文件的隐藏、系统以及只读属性DWORD dwFileAttributes = GetFileAttributes(szSysPath);dwFileAttributes &= ~FILE_ATTRIBUTE_HIDDEN;dwFileAttributes &= ~FILE_ATTRIBUTE_SYSTEM;dwFileAttributes &= ~FILE_ATTRIBUTE_READONLY;SetFileAttributes(szSysPath, dwFileAttributes);// 删除spoclsv.exebRet = DeleteFile(szSysPath);if (bRet){csTxt += _T("spoclsv.exe病毒被删除!\r\n");}else{csTxt += _T("spoclsv.exe病毒无法删除\r\n");}}}SetDlgItemText(IDC_LIST,csTxt);Sleep(10);///// 删除每个盘符下的setup.exe与autorun.inf,以及Desktop_.ini///char szDriverString[MAXBYTE] = { 0 };char *pTmp = NULL;//获取字符串类型的驱动器列表GetLogicalDriveStrings(MAXBYTE, szDriverString);pTmp = szDriverString;while( *pTmp ){char szAutorunPath[MAX_PATH] = { 0 };char szSetupPath[MAX_PATH] = { 0 };lstrcat(szAutorunPath,pTmp);lstrcat(szAutorunPath,"autorun.inf");lstrcat(szSetupPath,pTmp);lstrcat(szSetupPath,"setup.exe");if (GetFileAttributes(szSetupPath) == 0xFFFFFFFF){csTxt += pTmp;csTxt += _T("setup.exe病毒文件不存在\r\n");}else{csTxt += pTmp;csTxt += _T("setup.exe病毒文件存在,正在进行计算校验和...\r\n");HANDLE hFile = CreateFile(szSetupPath,GENERIC_READ,FILE_SHARE_READ,NULL,OPEN_EXISTING,FILE_ATTRIBUTE_NORMAL,NULL);if (hFile == INVALID_HANDLE_VALUE){AfxMessageBox("Create Error");return ;}DWORD dwSize = GetFileSize(hFile,NULL);if (dwSize == 0xFFFFFFFF){AfxMessageBox("GetFileSize Error");return ;}BYTE *pFile = (BYTE*)malloc(dwSize);if (pFile == NULL){AfxMessageBox("malloc Error");return ;}DWORD dwNum = 0;ReadFile(hFile,pFile,dwSize,&dwNum,NULL);DWORD dwCrc32 = CRC32(pFile,dwSize);if (pFile != NULL){free(pFile);pFile = NULL;}CloseHandle(hFile);if (dwCrc32 != 0x89240FCD){csTxt += _T("校验和验证失败\r\n");}else{csTxt += _T("校验和验证成功,正在删除...\r\n");// 去除文件的隐藏、系统以及只读属性DWORD dwFileAttributes = GetFileAttributes(szSetupPath);dwFileAttributes &= ~FILE_ATTRIBUTE_HIDDEN;dwFileAttributes &= ~FILE_ATTRIBUTE_SYSTEM;dwFileAttributes &= ~FILE_ATTRIBUTE_READONLY;SetFileAttributes(szSetupPath, dwFileAttributes);// 删除setup.exebRet = DeleteFile(szSetupPath);if (bRet){csTxt += pTmp;csTxt += _T("setup.exe病毒被删除!\r\n");}else{csTxt += pTmp;csTxt += _T("setup.exe病毒无法删除\r\n");}}}// 去除文件的隐藏、系统以及只读属性DWORD dwFileAttributes = GetFileAttributes(szAutorunPath);dwFileAttributes &= ~FILE_ATTRIBUTE_HIDDEN;dwFileAttributes &= ~FILE_ATTRIBUTE_SYSTEM;dwFileAttributes &= ~FILE_ATTRIBUTE_READONLY;SetFileAttributes(szAutorunPath, dwFileAttributes);// 删除autorun.infbRet = DeleteFile(szAutorunPath);csTxt += pTmp;if (bRet){csTxt += _T("autorun.inf被删除!\r\n");}else{csTxt += _T("autorun.inf不存在或无法删除\r\n");}// 删除Desktop_.iniFindFiles(pTmp);// 检查下一个盘符pTmp += 4;}Sleep(10);///// 修复注册表内容,删除病毒启动项并修复文件的隐藏显示///csTxt += _T("正在检查注册表...\r\n");SetDlgItemText(IDC_LIST,csTxt);// 首先检查启动项char RegRun[] = "Software\\Microsoft\\Windows\\CurrentVersion\\Run";HKEY hKeyHKCU = NULL;LONG lSize = MAXBYTE;char cData[MAXBYTE] = { 0 };long lRet = RegOpenKey(HKEY_CURRENT_USER, RegRun, &hKeyHKCU);if(lRet == ERROR_SUCCESS){lRet = RegQueryValueEx(hKeyHKCU,"svcshare",NULL,NULL,(unsigned char *)cData,(unsigned long *)&lSize);if ( lRet == ERROR_SUCCESS){if (lstrcmp(cData,"C:\\WINDOWS\\system32\\drivers\\spoclsv.exe") == 0){csTxt += _T("注册表启动项中存在病毒信息\r\n");}lRet = RegDeleteValue(hKeyHKCU,"svcshare");if (lRet == ERROR_SUCCESS){csTxt += _T("注册表启动项中的病毒信息已删除!\r\n");}else{csTxt += _T("注册表启动项中的病毒信息无法删除\r\n");}}else{csTxt += _T("注册表启动项中不存在病毒信息\r\n");}RegCloseKey(hKeyHKCU);}else{csTxt += _T("注册表启动项信息读取失败\r\n");}// 接下来修复文件的隐藏显示,需要将CheckedValue的值设置为1char RegHide[] = "SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Explorer\\Advanced\\Folder\\Hidden\\SHOWALL";HKEY hKeyHKLM = NULL;DWORD dwFlag = 1;long lRetHide = RegOpenKey(HKEY_LOCAL_MACHINE, RegHide, &hKeyHKLM);if(lRetHide == ERROR_SUCCESS){csTxt += _T("检测注册表的文件隐藏选项...\r\n");if( ERROR_SUCCESS == RegSetValueEx(hKeyHKLM, //subkey handle"CheckedValue", //value name0, //must be zeroREG_DWORD, //value type(CONST BYTE*)&dwFlag, //pointer to value data4)) //length of value data{csTxt += _T("注册表修复完毕!\r\n");}else{csTxt += _T("无法恢复注册表的文件隐藏选项\r\n");}}///// 病毒查杀完成///csTxt += _T("病毒查杀完成,请使用专业杀毒软件进行全面扫描!\r\n");SetDlgItemText(IDC_LIST,csTxt);}