PHP/5.6.40字符逃逸
<?php/*# -*- coding: utf-8 -*-# @Author: h1xa# @Date: 2020-12-03 02:37:19# @Last Modified by: h1xa# @Last Modified time: 2020-12-03 16:05:38# @message.php# @email: h1xa@ctfer.com# @link: https://ctfer.com*/error_reporting(0);session_start();class message{public $from;public $msg;public $to;public $token='user';public function __construct($f,$m,$t){$this->from = $f;$this->msg = $m;$this->to = $t;}}$f = $_GET['f'];$m = $_GET['m'];$t = $_GET['t'];if(isset($f) && isset($m) && isset($t)){$msg = new message($f,$m,$t);$umsg = str_replace('fuck', 'loveU', serialize($msg));$_SESSION['msg']=base64_encode($umsg);echo 'Your message has been sent';}highlight_file(__FILE__);
看注释发现 message.php
<?php/*# -*- coding: utf-8 -*-# @Author: h1xa# @Date: 2020-12-03 15:13:03# @Last Modified by: h1xa# @Last Modified time: 2020-12-03 15:17:17# @email: h1xa@ctfer.com# @link: https://ctfer.com*/session_start();highlight_file(__FILE__);include('flag.php');class message{public $from;public $msg;public $to;public $token='user';public function __construct($f,$m,$t){$this->from = $f;$this->msg = $m;$this->to = $t;}}if(isset($_COOKIE['msg'])){$msg = unserialize(base64_decode($_SESSION['msg']));if($msg->token=='admin'){echo $flag;}}
看注释发现 message.php
<?php/*# -*- coding: utf-8 -*-# @Author: h1xa# @Date: 2020-12-03 15:13:03# @Last Modified by: h1xa# @Last Modified time: 2020-12-03 15:17:17# @email: h1xa@ctfer.com# @link: https://ctfer.com*/session_start();highlight_file(__FILE__);include('flag.php');class message{public $from;public $msg;public $to;public $token='user';public function __construct($f,$m,$t){$this->from = $f;$this->msg = $m;$this->to = $t;}}if(isset($_COOKIE['msg'])){$msg = unserialize(base64_decode($_SESSION['msg']));if($msg->token=='admin'){echo $flag;}}
一开始没看出和 web262 有啥区别,仔细看了一下发现,反序列化时使用了 session 而不是直接通过 Cookie 接收
做法和 web262中第二种做法一样,虽然不是通过 Cookie 接收,也别忘了了 Cookie 的 msg 字段附加个值,不然不满足
if(isset($_COOKIE['msg'])){
先请求 index.php (这里 poc 不明白怎么构造看一下 web262 第二种做法)
因为 PHP 的 session 是通过 Cookie 里的 PHPSESSID 获取的(不清除参考 web263 session 伪造),所以要记录下来,然后在 message.php 里带上。
然后请求一下 message.php , 别忘了 Cookie 部分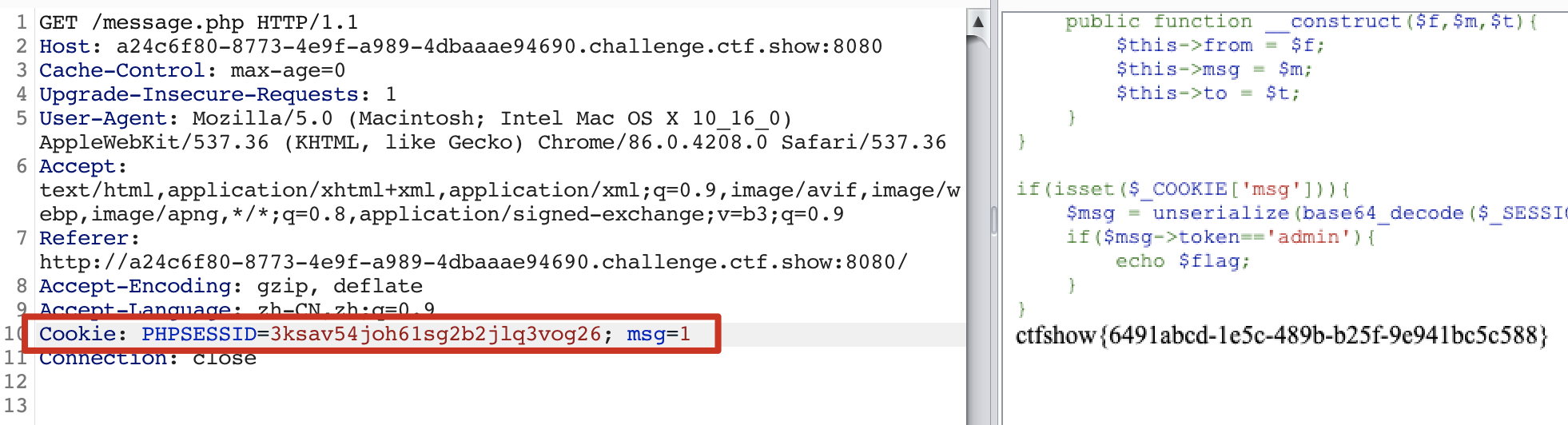
flag
ctfshow{6491abcd-1e5c-489b-b25f-9e941bc5c588}

