iptable 合集
https://www.zsythink.net/archives/tag/iptables/
http://www.shikexu.com/archives/419
iptable 概念
https://www.zsythink.net/archives/1199
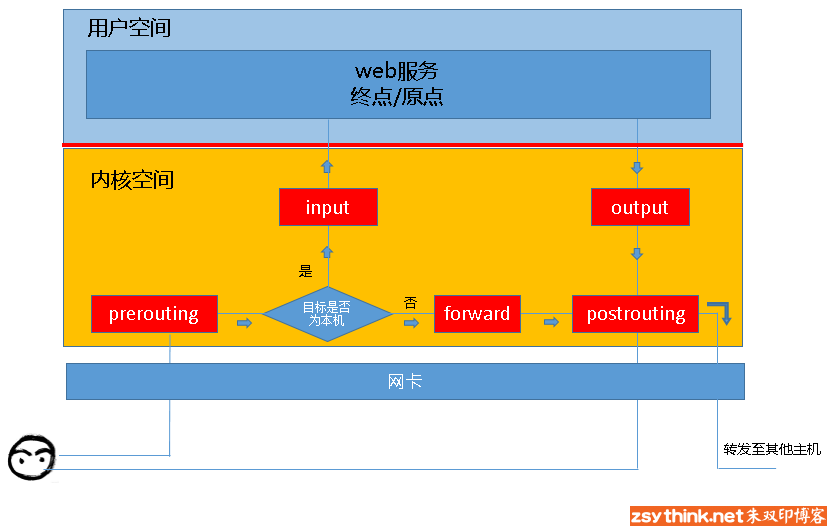
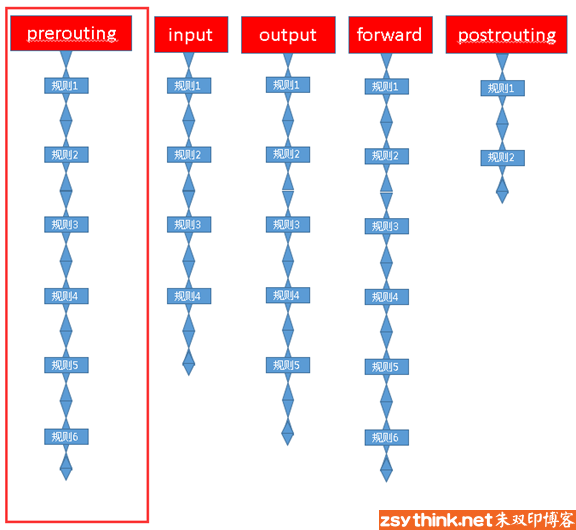<br /> <br /> 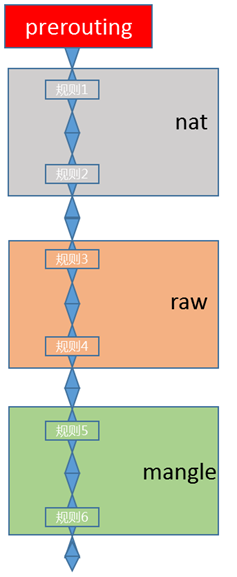 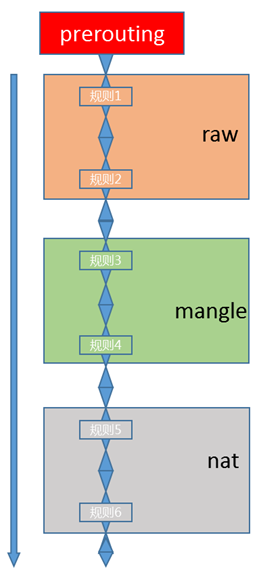
安装相关软件包
yum install iptables iptables-services -ysystemctl mask firewalldsystemctl stop firewalldsystemctl disable firewalldsystemctl unmask iptablessystemctl enable --now iptablessystemctl status iptables.service
[root@riyimei ~]# rpm -qa iptables*iptables-1.4.21-35.el7.x86_64iptables-services-1.4.21-35.el7.x86_64[root@riyimei ~]#
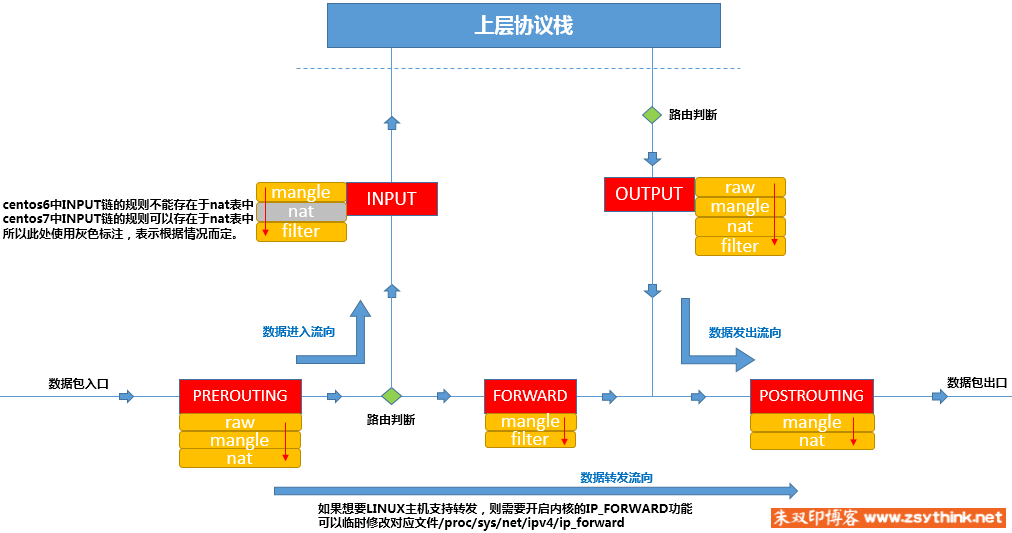
查看默认规则
[root@riyimei ~]# iptables -LChain INPUT (policy ACCEPT)target prot opt source destinationACCEPT all -- anywhere anywhere state RELATED,ESTABLISHEDACCEPT icmp -- anywhere anywhereACCEPT all -- anywhere anywhereACCEPT tcp -- anywhere anywhere state NEW tcp dpt:sshREJECT all -- anywhere anywhere reject-with icmp-host-prohibitedChain FORWARD (policy ACCEPT)target prot opt source destinationREJECT all -- anywhere anywhere reject-with icmp-host-prohibitedChain OUTPUT (policy ACCEPT)target prot opt source destination[root@riyimei ~]#
target列表示操作决定,
ACCEPT表示允许,
REJECT或DROP表示拒绝
prot列表示本规则针对的协议
opt列表示参数、选项
source列表示针对的源ip
destination列表示针对的目的ip
最后一列表示 相关参数、状态等介绍,相当于备注
清空所有规则
[root@riyimei ~]# iptables -F && iptables -LChain INPUT (policy ACCEPT)target prot opt source destinationChain FORWARD (policy ACCEPT)target prot opt source destinationChain OUTPUT (policy ACCEPT)target prot opt source destination[root@riyimei ~]#
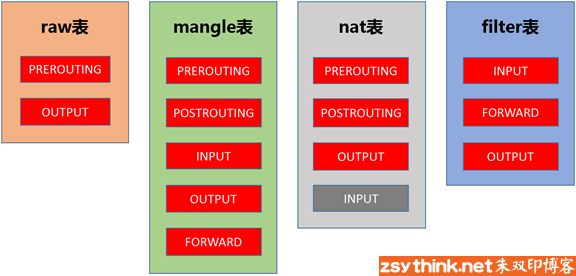
拒绝任何来源ftp请求的规则
[root@riyimei ~]# iptables -t filter -A INPUT -i eth0 -p tcp --dport 21 -j DROP[root@riyimei ~]# iptables -LChain INPUT (policy ACCEPT)target prot opt source destinationDROP tcp -- anywhere anywhere tcp dpt:ftpChain FORWARD (policy ACCEPT)target prot opt source destinationChain OUTPUT (policy ACCEPT)target prot opt source destination[root@riyimei ~]# iptables-save# Generated by iptables-save v1.4.21 on Mon Apr 19 21:08:43 2021*mangle:PREROUTING ACCEPT [4069:358430]:INPUT ACCEPT [4062:358042]:FORWARD ACCEPT [7:388]:OUTPUT ACCEPT [2257:243121]:POSTROUTING ACCEPT [2288:244257]COMMIT# Completed on Mon Apr 19 21:08:43 2021# Generated by iptables-save v1.4.21 on Mon Apr 19 21:08:43 2021*nat:PREROUTING ACCEPT [136:12684]:INPUT ACCEPT [131:12384]:OUTPUT ACCEPT [38:3168]:POSTROUTING ACCEPT [38:3168]COMMIT# Completed on Mon Apr 19 21:08:43 2021# Generated by iptables-save v1.4.21 on Mon Apr 19 21:08:43 2021*filter:INPUT ACCEPT [54:3144]:FORWARD ACCEPT [0:0]:OUTPUT ACCEPT [26:2621]-A INPUT -i eth0 -p tcp -m tcp --dport 21 -j DROPCOMMIT# Completed on Mon Apr 19 21:08:43 2021[root@riyimei ~]#
在INPUT 插入第一条规则
[root@riyimei ~]# iptables -t filter -I INPUT -i eth0 -p tcp --dport 21 -s 192.168.6.0/24 -j ACCEPT[root@riyimei ~]# iptables -L -nChain INPUT (policy ACCEPT)target prot opt source destinationACCEPT tcp -- 192.168.6.0/24 0.0.0.0/0 tcp dpt:21DROP tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:21Chain FORWARD (policy ACCEPT)target prot opt source destinationChain OUTPUT (policy ACCEPT)target prot opt source destination[root@riyimei ~]#
只允许 192.168.6.99 访问 192.168.6.95 的ssh 22端口
切记需要在192.168.6.99 上添加防火墙规则 否则无法再次登记主机
[root@riyimei ~]# iptables -t filter -I INPUT -i eth0 -p tcp --dport 22 -s 192.168.6.99 -j ACCEPT[root@riyimei ~]# iptables -t filter -I INPUT 2 -i eth0 -p tcp --dport 22 -j DROP[root@riyimei ~]# iptables -t filter -I INPUT 3 -i eth0 -p tcp --dport 22 -m tos ! --tos 0x10 -j ACCEPT
[root@rancher-server ~]# ssh 192.168.6.95root@192.168.6.95's password:Last login: Mon Apr 19 21:25:06 2021 from 192.168.6.99[root@riyimei ~]# iptables -L -nChain INPUT (policy ACCEPT)target prot opt source destinationACCEPT tcp -- 192.168.6.99 0.0.0.0/0 tcp dpt:22DROP tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:22ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:22 tos match!0x10/0xffChain FORWARD (policy ACCEPT)target prot opt source destinationChain OUTPUT (policy ACCEPT)target prot opt source destinationChain DOCKER (0 references)target prot opt source destinationChain DOCKER-ISOLATION (0 references)target prot opt source destination[root@riyimei ~]#
https://blog.51cto.com/u_13553337/2338639
仅拒绝ssh 协议 放行scp sftp
ssh: tos 0x0 0x10scp: tos 0x0 0x8rsync: tos 0x0 0x8
iptables -t filter -I INPUT 2 -i eth0 -p tcp —dport 22 -m tos ! —tos 0x8 -j DROP
[root@riyimei ~]# iptables -t filter -I INPUT -i eth0 -p tcp --dport 22 -s 192.168.6.99 -j ACCEPT[root@riyimei ~]# iptables -t filter -I INPUT 2 -i eth0 -p tcp --dport 22 -m tos ! --tos 0x10 -j DROP
[root@riyimei ~]# iptables -L -nChain INPUT (policy ACCEPT)target prot opt source destinationACCEPT tcp -- 192.168.6.99 0.0.0.0/0 tcp dpt:22DROP tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:22 tos match!0x10/0xffChain FORWARD (policy ACCEPT)target prot opt source destinationChain OUTPUT (policy ACCEPT)target prot opt source destinationChain DOCKER (0 references)target prot opt source destinationChain DOCKER-ISOLATION (0 references)target prot opt source destination[root@riyimei ~]#
[root@riyimei ~]# scp /etc/hosts 192.168.6.100:/tmp/root@192.168.6.100's password:hosts 100% 158 19.3KB/s 00:00[root@riyimei ~]#
[root@riyimei ~]# iptables -t filter -I INPUT -i eth0 -p tcp --dport 22 -m tos ! --tos 0x10 -j ACCEPT[root@riyimei ~]# iptables -L -nChain INPUT (policy ACCEPT)target prot opt source destinationACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:22 tos match!0x10/0xffACCEPT tcp -- 192.168.6.99 0.0.0.0/0 tcp dpt:22DROP tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:22 tos match!0x08/0xffChain FORWARD (policy ACCEPT)target prot opt source destinationChain OUTPUT (policy ACCEPT)target prot opt source destinationChain DOCKER (0 references)target prot opt source destinationChain DOCKER-ISOLATION (0 references)target prot opt source destination[root@riyimei ~]#
-m state —state NEW -m tcp
-m state跟TCP中的状态没有关系NEW 新生态ESTABLISHED 连接态(客户端发出请求,服务端回应后)RELATED 衍生态 (相关联的,有数据端口和传输端口的都符合)INVALID 无效态[root@uplook ~]# iptables -t filter -I INPUT -m state --state ESTABLISHED,RELATED -j ACCEPTNEW:表示数据包将要或已经开始建立一个新的链接,或者这个包和一个还没有在两端都有数据发送的链接有关。ESTABLISHED:数据包完全有效,而且属于一个已建立的链接,这个链接的两端都已经有数据发送RELATED:说明包正在建立一个新的链接,这个链接是和一个已建立的链接有关的INVALID:说明这个包没有已知的流或链接与之关联
[root@riyimei ~]# cat /etc/sysconfig/iptables# sample configuration for iptables service# you can edit this manually or use system-config-firewall# please do not ask us to add additional ports/services to this default configuration*filter:INPUT ACCEPT [0:0]:FORWARD ACCEPT [0:0]:OUTPUT ACCEPT [0:0]-A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT-A INPUT -p icmp -j ACCEPT-A INPUT -i lo -j ACCEPT-A INPUT -p tcp -m state --state NEW -m tcp --dport 22 -j ACCEPT-A INPUT -j REJECT --reject-with icmp-host-prohibited-A FORWARD -j REJECT --reject-with icmp-host-prohibitedCOMMIT[root@riyimei ~]#

