Harbor是构建企业级私有docker镜像的仓库的开源解决方案,它是Docker Registry的更高级封装,它除了提供友好的Web UI界面,角色和用户权限管理,用户操作审计等功能外,它还整合了K8s的插件(Add-ons)仓库。
准备工作
详细配置参数,参考:https://github.com/goharbor/harbor-helm
创建存储池
这里使用storageClass,则需要先创建storageClass,请参考ceph。
cmd.sh "sudo modprobe rbd"ceph osd pool create k8s 256
创建秘钥:
cat << EOF | kubectl create -f -apiVersion: v1kind: Secretmetadata:name: ceph-admin-secrettype: "kubernetes.io/rbd"data:key: $(grep key /etc/ceph/ceph.client.admin.keyring |awk '{printf "%s", $NF}'|base64)EOF
创建存储类:
cat << EOF | kubectl create -f -apiVersion: storage.k8s.io/v1kind: StorageClassmetadata:name: ceph-rbdprovisioner: kubernetes.io/rbdparameters:monitors: 192.168.56.111:6789adminId: adminadminSecretName: ceph-admin-secretadminSecretNamespace: defaultpool: k8suserId: adminuserSecretName: ceph-admin-secretuserSecretNamespace: default# 设置回收策略默认为:RetainreclaimPolicy: Retain# 添加动态扩容allowVolumeExpansion: trueEOF
将存储类设置为默认:
kubectl patch storageclass ceph-rbd -p \'{"metadata": {"annotations":{"storageclass.kubernetes.io/is-default-class":"true"}}}'
创建命名空间
kubectl create namespace harbor
添加仓库
helm repo add harbor https://helm.goharbor.io
创建证书
使用letsencrypt生成证书文件
参考 使用Cert Manager配置Let’s Encrypt证书 ,先要创建一个ClusterIssuer:javachen-space-letsencrypt-prod。
cat << EOF | kubectl create -f -apiVersion: cert-manager.io/v1alpha2kind: ClusterIssuermetadata:name: javachen-space-letsencrypt-prodspec:acme:server: https://acme-v02.api.letsencrypt.org/directoryemail: junecloud@163.comprivateKeySecretRef:name: javachen-space-letsencrypt-prodsolvers:- selector:dnsNames:- '*.javachen.space'dns01:webhook:groupName: acme.javachen.spacesolverName: godaddyconfig:authApiKey: e4hN4QrFgzdo_RHXe1ef2qpBPmiJPD2ZUcWauthApiSecret: QsHuDdnnCbzp5DmEQzq4tsproduction: truettl: 600EOF
因为证书是有命名空间的,所以需要在harbor命名空间创建证书:
cat << EOF | kubectl create -f -apiVersion: cert-manager.io/v1alpha2kind: Certificatemetadata:name: harbor-cert-prodnamespace: harborspec:secretName: harbor-javachen-space-certrenewBefore: 240hgroupName: acme.javachen.spacednsNames:- "*.javachen.space"issuerRef:name: javachen-space-letsencrypt-prodkind: ClusterIssuerEOF
安装Harbor
不配置存储,使用默认的证书,禁用clair、notary、chartmuseum,通过helm3安装:
helm install harbor harbor/harbor --namespace harbor --debug \--set externalURL=https://harbor.javachen.space \--set expose.ingress.hosts.core=harbor.javachen.space \--set expose.ingress.hosts.notary=harbor.javachen.space \--set persistence.enabled=false \--set clair.enabled=false \--set notary.enabled=false \--set chartmuseum.enabled=false \--set harborAdminPassword=admin123
配置存储,使用默认的证书,通过helm3安装:
helm install harbor harbor/harbor --namespace harbor --debug \--set externalURL=https://harbor.javachen.space \--set expose.ingress.hosts.core=harbor.javachen.space \--set expose.ingress.hosts.notary=harbor.javachen.space \--set persistence.persistentVolumeClaim.registry.storageClass=ceph-rbd \--set persistence.persistentVolumeClaim.registry.size=50Gi \--set persistence.persistentVolumeClaim.chartmuseum.storageClass=ceph-rbd \--set persistence.persistentVolumeClaim.jobservice.storageClass=ceph-rbd \--set persistence.persistentVolumeClaim.database.storageClass=ceph-rbd \--set persistence.persistentVolumeClaim.database.size=5Gi \--set persistence.persistentVolumeClaim.redis.storageClass=ceph-rbd \--set harborAdminPassword=admin123
配置存储,使用前面letsencrypt生成的harbor-javachen-space-cert证书,通过helm3安装:
helm install harbor harbor/harbor --namespace harbor --debug \--set externalURL=https://harbor.javachen.space \--set expose.tls.secretName="harbor-javachen-space-cert" \--set expose.tls.notarySecretName="notary-javachen-space-cert" \--set expose.ingress.hosts.core=harbor.javachen.space \--set expose.ingress.hosts.notary=notary.javachen.space \--set persistence.persistentVolumeClaim.registry.storageClass=ceph-rbd \--set persistence.persistentVolumeClaim.registry.size=50Gi \--set persistence.persistentVolumeClaim.chartmuseum.storageClass=ceph-rbd \--set persistence.persistentVolumeClaim.jobservice.storageClass=ceph-rbd \--set persistence.persistentVolumeClaim.database.storageClass=ceph-rbd \--set persistence.persistentVolumeClaim.database.size=5Gi \--set persistence.persistentVolumeClaim.redis.storageClass=ceph-rbd \--set harborAdminPassword=admin123
配置存储,使用ingress自动生成证书(参考 结合Cert-Manager完成Harbor的Https证书自动签发),通过helm3安装:
创建harbor-values.yaml
expose:type: ingresstls:enabled: true# 这里可以随意填写一个,cert-manager会自动创建并挂载secretName: "harbor-javachen-space-cert"notarySecretName: "notary-javachen-space-cert"commonName: ""ingress:hosts:core: harbor.javachen.spacenotary: notary.javachen.spaceannotations:ingress.kubernetes.io/ssl-redirect: "true"cert-manager.io/issuer: javachen-space-letsencrypt-prodexternalURL: https://harbor.javachen.spaceharborAdminPassword: admin123persistence:persistentVolumeClaim:registry:storageClass: ceph-rbdsize: 50Gichartmuseum:storageClass: ceph-rbdjobservice:storageClass: ceph-rbddatabase:storageClass: ceph-rbdsize: 5Giredis:storageClass: ceph-rbd
运行安装:
helm install harbor harbor/harbor -n harbor -f harbor-values.yaml
查看状态
kubectl get pod -o wide -n harbor#如果pod初始化很慢,可以查看具体日志:kubectl describe pod harbor-harbor-database-0 -n harborkubectl get pod,pv,pvc,sc,ingress,deployment,ingress -n harbor
如果下载镜像慢,则手动下载:
docker pull busybox:latestdocker pull goharbor/harbor-db:v1.9.3
查看rbd上创建的块:
$ rbd list k8skubernetes-dynamic-pvc-44f0325a-ec2e-414c-bc93-34503050fa1dkubernetes-dynamic-pvc-76dedc13-a83d-485e-a4cb-41280cd0e7d0kubernetes-dynamic-pvc-99414704-8eac-4adc-aa65-9a458fe859eckubernetes-dynamic-pvc-c8dd8c01-07b1-4d31-9b82-0aecf9f76f3ckubernetes-dynamic-pvc-f9b96d83-3859-4942-8c25-c72c515bb997
查看Rancher上创建的pvc: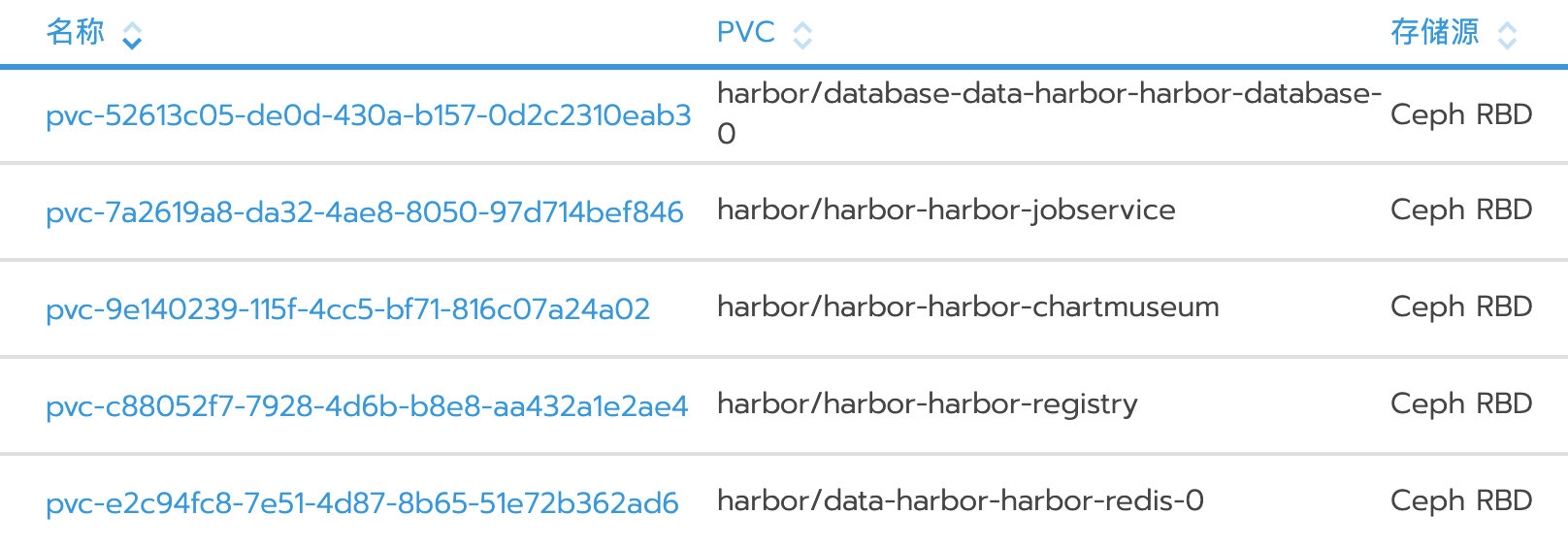
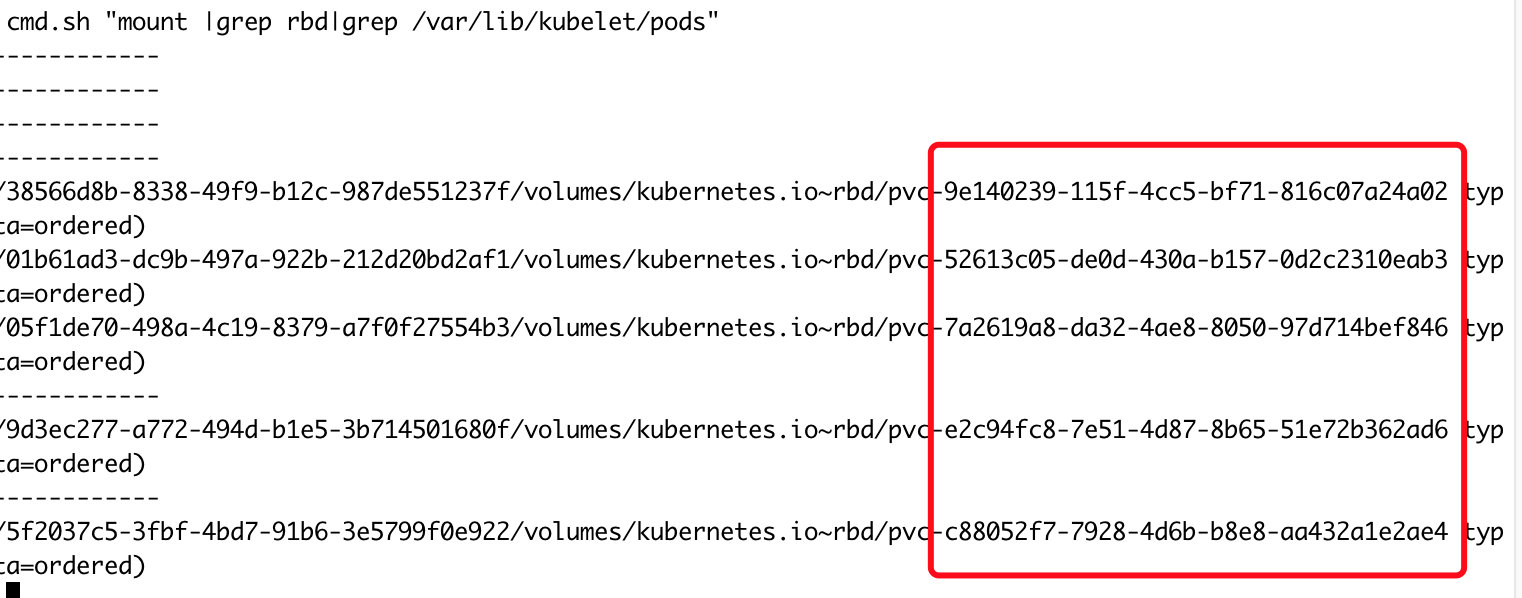
在ceph节点上查看挂载信息
cmd.sh "mount |grep rbd|grep /var/lib/kubelet/pods"
查看证书
kubectl get secret -n harborkubectl get secret -n harbor harbor-harbor-ingress \-o jsonpath="{.data.ca\.crt}" | base64 --decode
可以将证书导入到docker证书目录下面,这样docker就会信任该镜像仓库
kubectl get secret -n harbor harbor-harbor-ingress \-o jsonpath="{.data.ca\.crt}" | base64 --decode | \sudo tee /etc/docker/certs.d/harbor.javachen.space/ca.crt
可以查看harbor密码:
kubectl get secret -n harbor harbor-harbor-core -o \jsonpath="{.data.HARBOR_ADMIN_PASSWORD}" | base64 --decode
浏览器访问服务
浏览器访问harbor:https://harbor.javachen.space/ ,用户名和密码:admin/admin123,可以看到证书是被浏览器信任的。
docker 登陆验证
docker登陆:
$ docker login harbor.javachen.spaceUsername: adminPassword:
在kubernetes中使用harbor,为了避免输入账号密码,需要创建secret。以下操作在master上执行:
创建secret
kubectl create secret docker-registry harbor-registry-secret \--docker-server=harbor.javachen.space -n harbor --docker-username=admin \--docker-password=admin123
创建完成后,可以用以下命令查看:
kubectl get secret -n harbor
出现异常:
x509: certificate is valid for ingress.local, not harbor.javachen.space
参考:解决harbor+cert-manager出现ingress-nginx x509: certificate is valid for ingress.local
原因:在于证书的CA签发组织不对,使用Helm生成的证书默认域名是ingress.local,不是harbor.javachen.space。
出现异常:
Error response from daemon: Get https://harbor.javachen.space/v2/: x509: certificate signed by unknown authority
参考前面,将harbor证书导入到docker证书目录下面,这样docker就会信任该镜像仓库
sudo mkdir -p /etc/docker/certs.d/harbor.javachen.space/kubectl get secret -n harbor harbor-harbor-ingress \-o jsonpath="{.data.ca\.crt}" | base64 --decode | \sudo tee /etc/docker/certs.d/harbor.javachen.space/ca.crt
上传下载测试
在harbor管理界面,创建一个soft项目
上传镜像:
$ docker imagesrancher/pause 3.1 da86e6ba6ca1 21 months ago 742kBdocker tag rancher/pause:3.1 harbor.javachen.space/soft/pause:3.2docker push harbor.javachen.space/soft/pause:3.2docker tag rancher/pause:3.1 harbor.javachen.space/soft/pause:latestdocker push harbor.javachen.space/soft/pause:latest
然后,在harbor管理界面中查看上传的镜像。
升级
升级到harbor2.0对应的chart版本为1.4.0
$ helm search repo harborNAME CHART VERSION APP VERSION DESCRIPTIONharbor/harbor 1.4.0 2.0.0 An open source trusted cloud native registry th...
升级:
helm upgrade harbor harbor/harbor -n harbor --version 1.4.0 -f harbor-values.yaml
卸载
#删除releasehelm del --purge harbor#删除pvckubectl delete pvc -n harbor data-harbor-harbor-redis-0 \database-data-harbor-harbor-database-0 \harbor-harbor-chartmuseum \harbor-harbor-jobservice \harbor-harbor-registrykubectl delete pod,service,deploy,statefulset,ingress,secret,pvc,replicaset,\daemonset,ConfigMap --all -n harbor#删除证书kubectl delete Certificate,secret harbor-javachen-space-cert -n harbor#还要删除rbd上的块rbd list k8s

