Abstract
Group Policy
Centrally distribute and configure Settings to user or to
computer.
Domain Group Policy
Configure Settings to user or to computer centrally on Domain Controllers, and the settings can be distributed and enforced on all users or computers in the domain.
Group Policy Object
GPT and GPC. GPT (group policy template )stores in Domain Controller SYSVOL Shared folder. GPC (group policy container) stores in Active Directory Database.
Group Policy Management
You manage Group Policy on domain controller using Group Policy Management Console
Definition
Group Policy Container
- Stored in the Active Directory: CN=Policies,CN=System,DC=Domain_Name
- gPCFileSysPath, Version number, Display Name, Object GUID, Client-side Extensions called
-
Group Policy Templates
Stored within the File System\
\SYSVOL\ \Policies - GPT.ini (version number & default GPO display name)
- SecEdit, Documents and Settings folder
-
Permission
•Delegation: Read and Apply Group Policy permissions on the GPO.
- •Security Filtering in Group Policy Management Console (GPMC).
-
GPMC
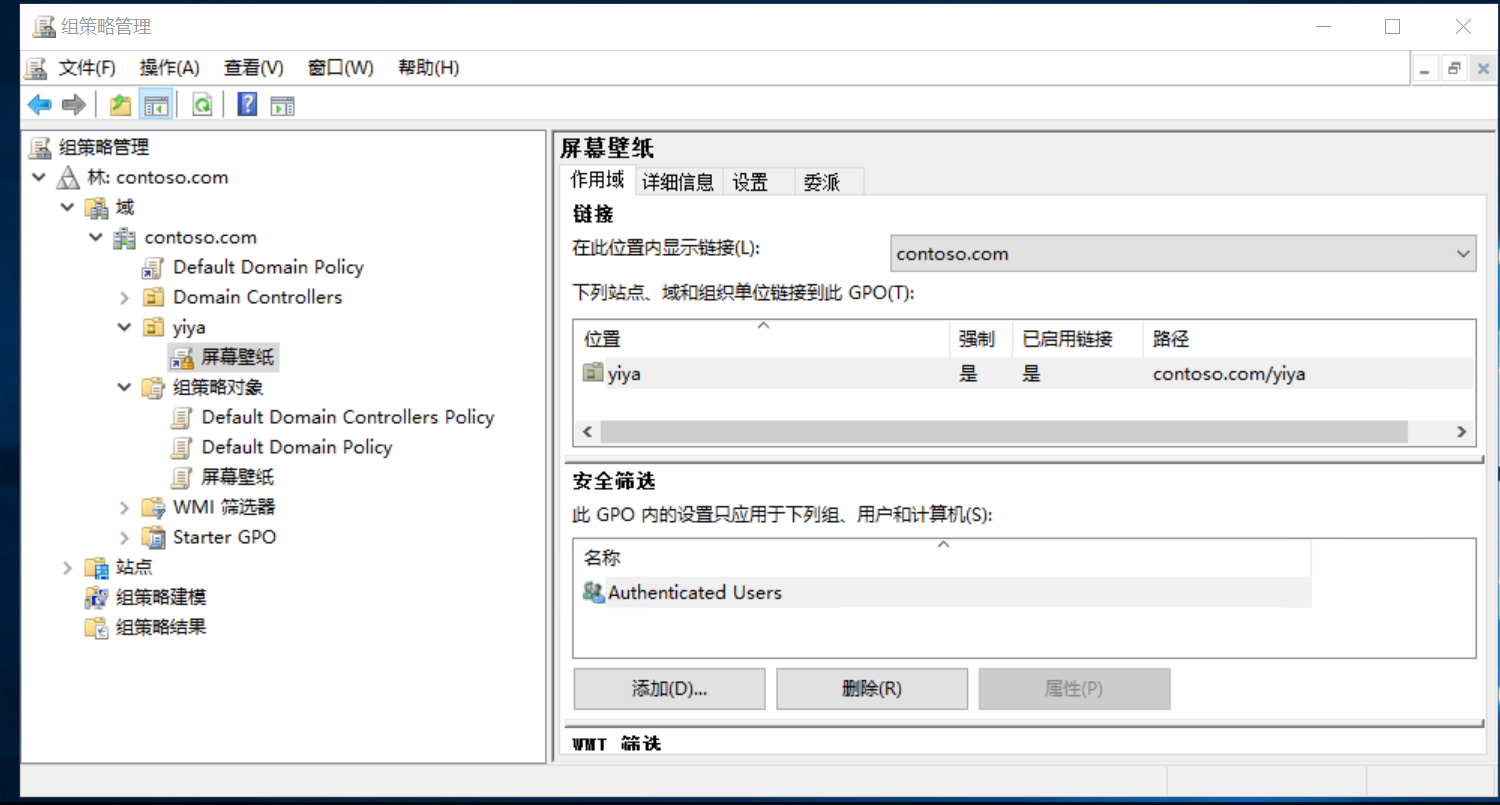
Creating a new group policy scope
- details
- settings
-
Client-Side Extensions
A client-side extension (CSE) is an integral component of enterprise group policy administration that applies Group Policy to users or endpoint systems.
Group Policy is designed using server-side and client-side elements. The server-side elements include a user interface for creating each Group Policy Object (GPO). When a client system logs into the environment through Active Directory (AD), the client-side elements — typically implemented as a series of .DLL files — receive and interpret the appropriate GPOs in order to make corresponding changes to the client system. CSE receives a list of GPOs to apply.
CSEs job is to retrieve the settings and apply them.
• How
CSE performs the application may differ
• This
happens outside of control of Group Policy Service
Each CSE stores setting in it’s own way
•Security:
GptTmpl.inf
•Folder redirection: fdeploy.ini
•Administrative Templates: registry.pol
•Preferences: *.xml
•Wireless: XML stored in ADSome CSEs share storage
•Windows
Firewall are stored in registry.pol
•NRPT
is stored in registry.pol
GUID
Each CSE is identified by a unique 128-bit number called a global unique identifier (GUID). As the server initializes Windows Server, the list of GPOs is passed to each endpoint’s CSE.(the client) The CSE, in turn, uses the GPO list to apply appropriate policies. GUIDs are also recorded by the CSE into event logs, so any problems or issues with GPO processing can be isolated and reviewed by its GUID.
For Group Policy extensions that implement both a client-side and administrative-side, the Extension list that is stored in a GPO specifies a list of GUID pairs. The first GUID of each pair is the CSE GUID, and the second GUID of each pair is an Administrative tool extension GUID.
Troubleshooting
server: unable to apply any OU
client: Unable to apply some of the OUs
- Permission problems
- Replication
- Refresh
- Network Connectivity
- Inaccesible Data
- Empty GPO
- …
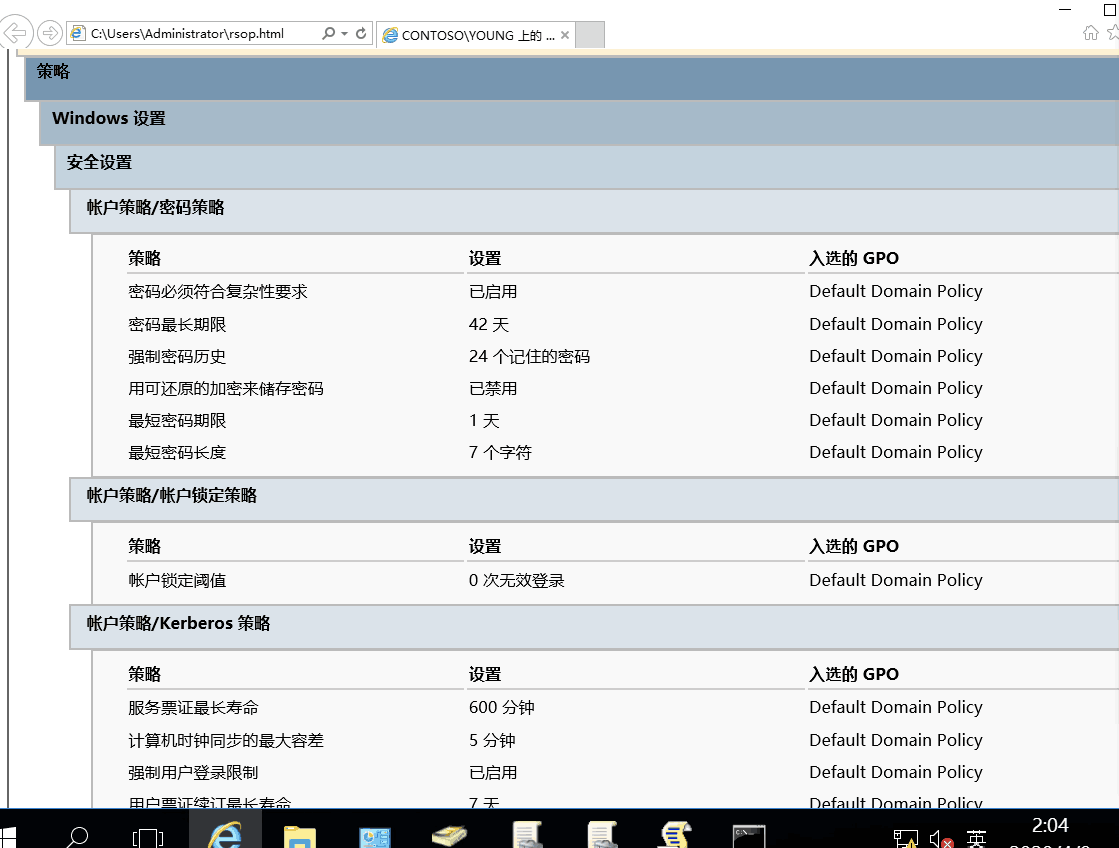
##The quickest way to see the Group Policies applied in your computers or User Accounts
Gpresult /
The easiest way to see all the Group Policy settings you’ve applied to your PC or user account is by using the Resultant Set of Policy tool. It doesn’t show every last policy applied to your PC. However, it does show pretty much all the policies you will have set for regular use. And it provides a simple, graphical interface for browsing through the Group Policy settings currently in effect on your PC—whether those settings come from Group Policy or Local Group Policy.
This makes it easy to browse through and see what policies are in effect.
If you’re comfortable using the Command Prompt, it does provide a couple of advantages over using the Resultant Set of Policy tool. First, it can show every last policy in effect on your PC. Second, it will show some additional security information—like what security groups a user is part of or what privileges they have.
And there are other things you can do with the gpresult command. For example, if you’d like to save the report instead of viewing it at the Command Prompt.
Command Prompt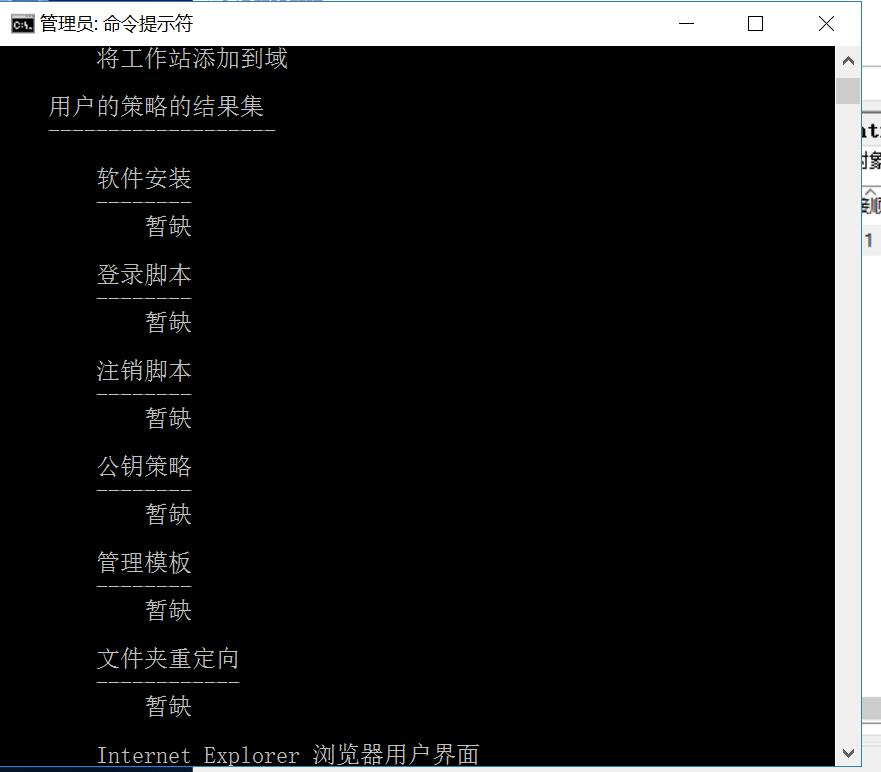
Generate Report via Html