Web 接口查看
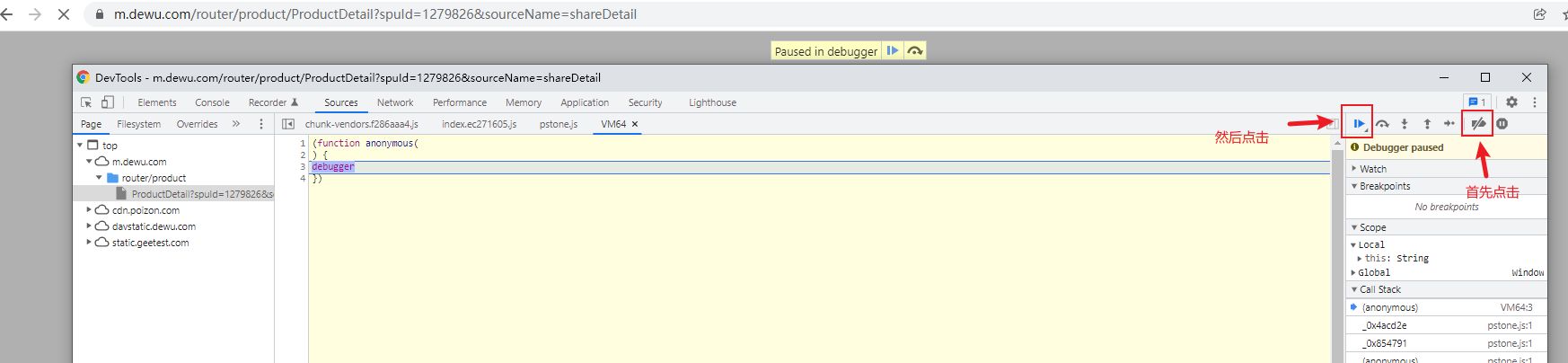
问题:打开控制台会有debugger陷阱
- 首先点击禁用
debugger按钮 - 然后点击“播放”按钮
- 使用 js 文件
[https://github.com/xuejianrong/my-project/blob/master/src/static/pstone.es5.js](https://github.com/xuejianrong/my-project/blob/master/src/static/pstone.es5.js) sign签名方式直接调用getSign(params),params为没有sign的其他参数销售记录api :https://app.dewu.com/api/v1/h5/commodity/fire/last-sold-list headers: Connection: keep-alive AppId: h5 User-Agent: Mozilla/5.0 (iPhone; CPU iPhone OS 13_2_3 like Mac OS X) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/13.0.3 Mobile/15E148 Safari/604.1 Content-Type: application/json Accept: application/json, text/plain, / sks: 1,hdw3 platform: h5 appVersion: 4.4.0 Origin: https://m.dewu.com Sec-Fetch-Site: same-site Sec-Fetch-Mode: cors Sec-Fetch-Dest: empty Referer: https://m.dewu.com/ Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
发送请求前 调用
window.dw.bindUser(userId)- 再调用
window.dw.Fun110(JSON.stringify(params), method),params为请求数据(但不是最终请求数据),如果销售记录{lastId: "",limit: 30,sign: "a6564b673e4e0f498fab551a9cac8255",sourceApp: "app",spuId: "1279826"}method为请求类型 如:GET、POST
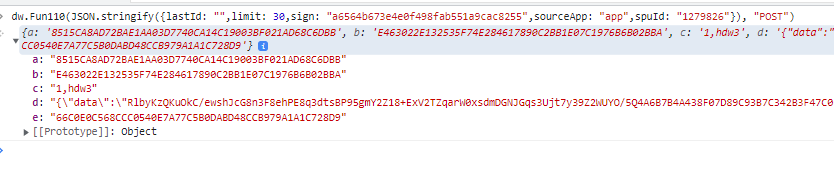
- 得到类似:
{a: "836BA8CA11070F71BF68004200386CAD18948816E79400EC", // 用于解密b: "578CB17C367F48870E8D4A0FC766D055608D40B870153FD6",c: "1,hdw3",d: "{\"data\":\"GZKkLGleFzMxF6jvX9q1wnjol69qtY7Q3telf5qysMMTa1s6N3sUnLWIOWpCvU5Qe3jy7fwznK2k/m7eEdOu6A2C4B950434477EAB346407B46A494D5E6361F100E9916826223291BFF92DD6E0F7E1D90BCCAB0EA1671ACE564F74F526350AAE863AD6FC61C91FA53F8DC5D13E333E065517FEA23E85F6DB76941E35D176382CBF690008F3F62C1350830136075A3153E0D3370EC70B219DBCFC8A5A96\"}",e: "4C22B9EDFA5E29DFDAF8C27B978A244C2D6E5DFDB25FD2F8"}
a是用来解密的d最终的请求数据
- 解密:
window.dw.Fun99(data, a, sks)
data接口返回的加密数据a3里面的sks观察到都是 “1,1”,这个字段在放在请求头的
例如:
window.dw.Fun99('xxxxxxxxxxxxxxxxxx', '8515CA8AD72BAE1AA03D7740CA14C19003BF021AD68C6DBB', '1,1')

