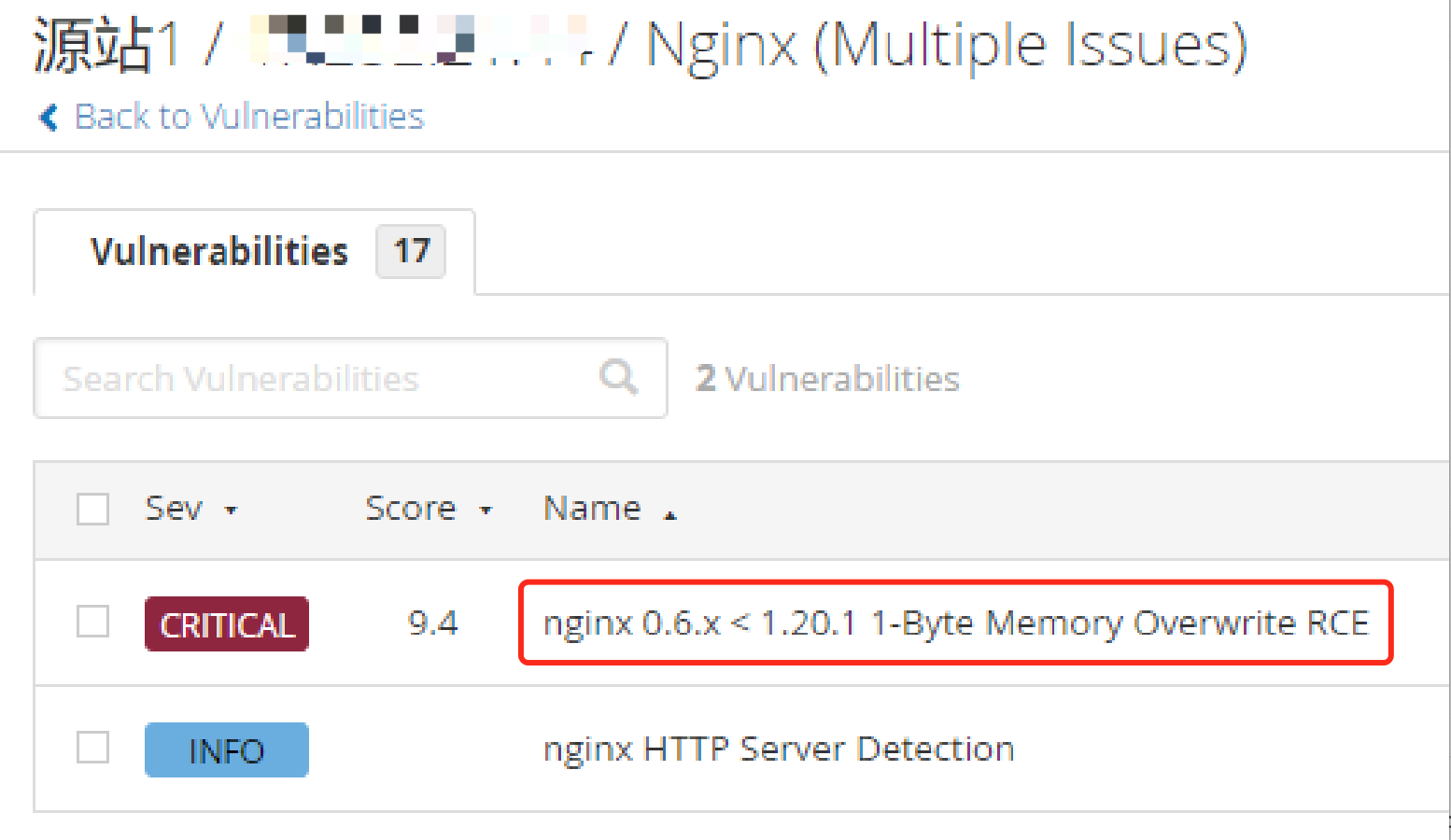
nginx 1.20.1 稳定版和 1.21.0 主线版已发布。这两个版本均修复了一个高危的安全漏洞——1-byte memory overwrite。此漏洞存在于 nginx 的 DNS 解析模块,并且仅在配置文件中使用”resolver”指令时才会影响 nginx。攻击者可以利用该漏洞进行远程 DDoS 攻击,甚至远程执行。
解决方案
从nginx官网获得apt源的公钥
这里是地址 http://nginx.org/keys/nginx_signing.key,为了方便我也复制一份到这里新建一个文本文件nginx_signing.key,把公钥写入到此文本文件之中
root@iZ0xi3fckpb4cq63wknd2fZ:~#vim nginx_signing.key-----BEGIN PGP PUBLIC KEY BLOCK-----Version: GnuPG v2.0.22 (GNU/Linux)mQENBE5OMmIBCAD+FPYKGriGGf7NqwKfWC83cBV01gabgVWQmZbMcFzeW+hMsgxHW6iimD0RsfZ9oEbfJCPG0CRSZ7ppq5pKamYs2+EJ8Q2ysOFHHwpGrA2C8zyNAs4IQxnZZIbETgcSwFtDun0XiqPwPZgyuXVm9PAbLZRbfBzm8wR/3SWygqZBBLdQk5TEfDR+Eny/M1RVR4xClECONF9UBB2ejFdI1LD45APbP2hsN/piFByU1t7yK2gpFyRt97WzGHn9MV5/TL7AmRPM4pcr3JacmtCnxXeCZ8nLqedoSuHFuhwyDnlAbu8I16O5XRrfzhrHRJFM1JnIiGmzZi6zBvH0ItfyX6ttABEBAAG0KW5naW54IHNpZ25pbmcga2V5IDxzaWduaW5nLWtleUBuZ2lueC5jb20+iQE+BBMBAgAoAhsDBgsJCAcDAgYVCAIJCgsEFgIDAQIeAQIXgAUCV2K1+AUJGB4fQQAKCRCr9b2Ce9m/YloaB/9XGrolkocm7l/tsVjaBQCteXKuwsm4XhCuAQ6YAwA1L1UheGOG/aa2xJvrXE8X32tgcTjrKoYoXWcdxaFjlXGTt6jV85qRguUzvMOxxSEM2Dn115etN9piPl0Zz+4rkx8+2vJGF+eMlruPXg/zd88NvyLq5gGHEsFRBMVufYmHtNfcp4okC1klWiRIRSdp4QY1wdrN1O+/oCTl8Bzy6hcHjLIq3aoumcLxMjtBoclc/5OTioLDwSDfVx7rWyfRhcBzVbwDoe/PD08AoAA6fxXvWjSxy+dGhEaXoTHjkCbz/l6NxrK3JFyauDgU4K4MytsZ1HDiMgMW8hZXxszoICTTiQEcBBABAgAGBQJOTkelAAoJEKZP1bF62zmo79oH/1XDb29SYtWp+MTJTPFEwlWRiyRuDXy3wBd/BpwBRIWfWzMs1gnCjNjk0EVBVGa2grvy9JtxJKMd6l/PWXVucSt+U/+GO8rBkw14SdhqxaS2l14v6gyMeUrSbY3XfToGfwHC4sa/Thn8X4jFaQ2XN5dAIzJGU1s5JA0tjEzUwCnmrKmyMlXZaoQVrmORGjCuH0I0aAFkRS0UtnB9HPpxhGVbs24xXZQnZDNbUQeulFxS4uP3OLDBAeCHl+v4t/uotIad8v6JSO93vc1evIje6lguE81HHmJn9noxPItvOvSMb2yPsE8mH4cJHRTFNSEhPW6ghmlfWa9ZwiVX5igxcvaIRgQQEQIABgUCTk5b0gAKCRDs8OkLLBcgg1G+AKCnacLb/+W6cflirUIExgZdUJqoogCeNPVwXiHEIVqithAM1pdY/gcaQZmIRgQQEQIABgUCTk5fYQAKCRCpN2E5pSTFPnNWAJ9gUozyiS+9jf2rJvqmJSeWuCgVRwCcCUFhXRCpQO2YVa3l3WuB+rgKjsQ==EWWI-----END PGP PUBLIC KEY BLOCK-----
添加公钥到apt包管理器
root@iZ0xi3fckpb4cq63wknd2fZ:~# apt-key add nginx_signing.keyOK
备份之前的apt源
root@iZ0xi3fckpb4cq63wknd2fZ:~# cp /etc/apt/sources.list /etc/apt/sources.list.bak
查看ubuntu对应的版本代码
此命令的输出会有一行如Codename: xxxx,记住这个版本代码,在下一步会用到。
root@iZ0xi3fckpb4cq63wknd2fZ:~# lsb_release -aLSB Version: core-11.1.0ubuntu2-noarch:security-11.1.0ubuntu2-noarchDistributor ID: UbuntuDescription: Ubuntu 20.04.3 LTSRelease: 20.04Codename: focal
更新nginx的apt安装源
使用vim打开source.list,在末尾添加两行,记得把下面标红code字样替换成为上面”lsb_release -a”查询结果codename后面的值
root@iZ0xi3fckpb4cq63wknd2fZ:~# vim /etc/apt/sources.list......deb http://nginx.org/packages/ubuntu/ code nginxdeb-src http://nginx.org/packages/ubuntu/ code nginx$apt updateGet:1 http://nginx.org/packages/ubuntu focal InRelease [3,584 B]Hit:2 http://us2.mirrors.cloud.aliyuncs.com/ubuntu focal InReleaseGet:3 http://nginx.org/packages/ubuntu focal/nginx Sources [9,696 B]Get:4 http://nginx.org/packages/ubuntu focal/nginx amd64 Packages [15.4 kB]Hit:5 http://us2.mirrors.cloud.aliyuncs.com/ubuntu focal-updates InReleaseHit:6 http://us2.mirrors.cloud.aliyuncs.com/ubuntu focal-backports InReleaseHit:7 http://us2.mirrors.cloud.aliyuncs.com/ubuntu focal-security InReleaseFetched 28.7 kB in 2s (12.0 kB/s)Reading package lists... DoneBuilding dependency treeReading state information... Done1 package can be upgraded. Run 'apt list --upgradable' to see it.N: Skipping acquire of configured file 'nginx/binary-i386/Packages' as repository 'http://nginx.org/packages/ubuntu focal InRelease' doesn't support architecture 'i386'
在更新apt安装源的时候可能会遇到上面的错误,这个时候我们只需要将原来的
deb http://nginx.org/packages/ubuntu/ focal nginxdeb-src http://nginx.org/packages/ubuntu/ focal nginx更改为deb [arch=amd64] http://nginx.org/packages/ubuntu/ focal nginxdeb-src http://nginx.org/packages/ubuntu/ focal nginx
再重新执行apt update即可。
重新安装并重新启动nginx服务
$ apt install nginx$ nginx -s reload
查询nginx版本
$ nginx -vnginx version: nginx/1.20.2

