六、整合SpringBoot项目实战
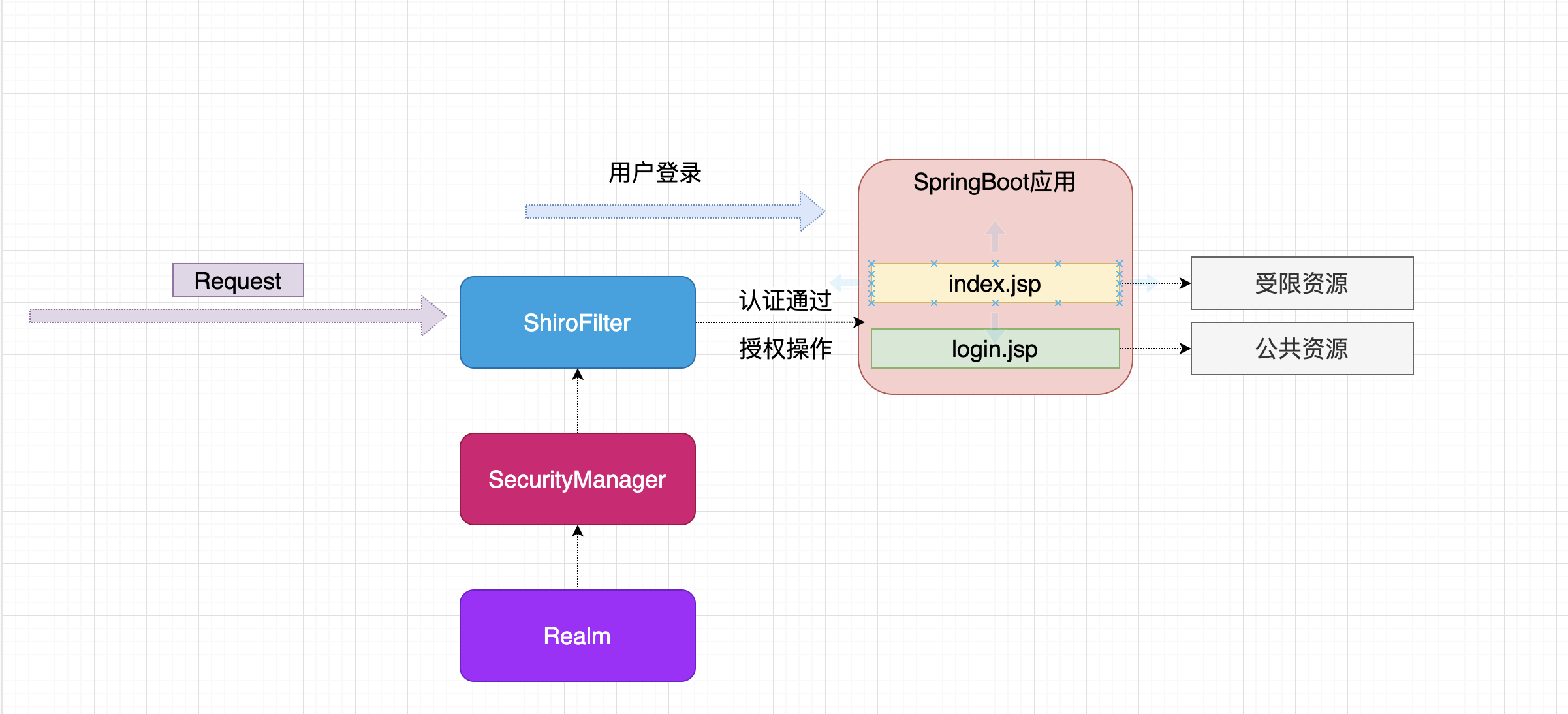
6.1 整合思路
6.2 配置环境
1.创建项目

2.引入依赖
<!--引入JSP解析依赖--><dependency><groupId>org.apache.tomcat.embed</groupId><artifactId>tomcat-embed-jasper</artifactId></dependency><dependency><groupId>jstl</groupId><artifactId>jstl</artifactId><version>1.2</version></dependency>
<!--引入shiro整合Springboot依赖--><dependency><groupId>org.apache.shiro</groupId><artifactId>shiro-spring-boot-starter</artifactId><version>1.5.3</version></dependency>
3.修改视图
application.properties 文件
server.port=8080server.servlet.context-path=/shirospring.application.name=shirospring.mvc.view.prefix=/spring.mvc.view.suffix=.jsp
4.修改配置
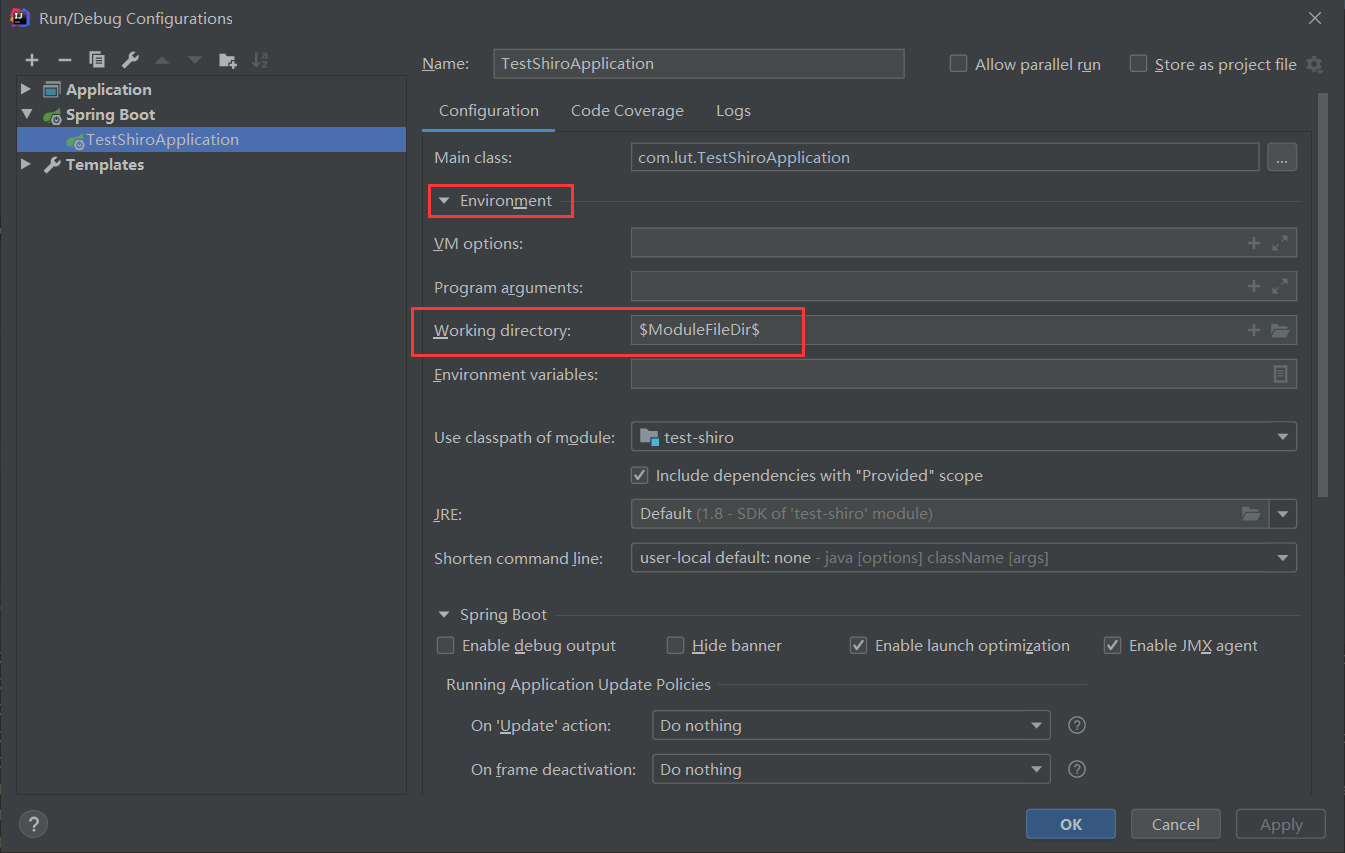
JSP 与IDEA 与SpringBoot存在一定的不兼容,修改此配置即可解决

6.3 简单使用
1.创建配置类
用来整合shiro框架相关的配置类
package com.lut.config;import com.lut.shiro.realms.CustomerRealm;import org.apache.shiro.authc.credential.HashedCredentialsMatcher;import org.apache.shiro.realm.Realm;import org.apache.shiro.spring.web.ShiroFilterFactoryBean;import org.apache.shiro.web.mgt.DefaultWebSecurityManager;import org.springframework.context.annotation.Bean;import org.springframework.context.annotation.Configuration;import java.util.HashMap;import java.util.Map;/*** 用来整合shiro框架相关的配置类*/@Configurationpublic class ShiroConfig {//1.创建shiroFilter //负责拦截所有请求@Beanpublic ShiroFilterFactoryBean getShiroFilterFactoryBean(DefaultWebSecurityManager defaultWebSecurityManager){ShiroFilterFactoryBean shiroFilterFactoryBean = new ShiroFilterFactoryBean();//给filter设置安全管理器shiroFilterFactoryBean.setSecurityManager(defaultWebSecurityManager);//配置系统受限资源//配置系统公共资源Map<String,String> map = new HashMap<String,String>();map.put("/index.jsp","authc");//authc 请求这个资源需要认证和授权//默认认证界面路径---当认证不通过时跳转shiroFilterFactoryBean.setLoginUrl("/login.jsp");shiroFilterFactoryBean.setFilterChainDefinitionMap(map);return shiroFilterFactoryBean;}//2.创建安全管理器@Beanpublic DefaultWebSecurityManager getDefaultWebSecurityManager(Realm realm){DefaultWebSecurityManager defaultWebSecurityManager = new DefaultWebSecurityManager();//给安全管理器设置defaultWebSecurityManager.setRealm(realm);return defaultWebSecurityManager;}//3.创建自定义realm@Beanpublic Realm getRealm(){CustomerRealm customerRealm = new CustomerRealm();return customerRealm;}}
2.自定义realm
package com.lut.shiro.realms;import org.apache.shiro.authc.AuthenticationException;import org.apache.shiro.authc.AuthenticationInfo;import org.apache.shiro.authc.AuthenticationToken;import org.apache.shiro.authc.SimpleAuthenticationInfo;import org.apache.shiro.authz.AuthorizationInfo;import org.apache.shiro.authz.SimpleAuthorizationInfo;import org.apache.shiro.realm.AuthorizingRealm;import org.apache.shiro.subject.PrincipalCollection;import org.springframework.util.CollectionUtils;import org.springframework.util.ObjectUtils;import java.util.List;//自定义realmpublic class CustomerRealm extends AuthorizingRealm {@Overrideprotected AuthorizationInfo doGetAuthorizationInfo(PrincipalCollection principals) {return null;}@Overrideprotected AuthenticationInfo doGetAuthenticationInfo(AuthenticationToken token) throws AuthenticationException {return null;}}
3.JSP文件
index.jsp
<%@page contentType="text/html;utf-8" pageEncoding="utf-8" isELIgnored="false" %><!doctype html><html lang="en"><head><meta charset="UTF-8"><meta name="viewport"content="width=device-width, user-scalable=no, initial-scale=1.0, maximum-scale=1.0, minimum-scale=1.0"><meta http-equiv="X-UA-Compatible" content="ie=edge"><title>Document</title></head><body><%-- 受限资源--%><h1>系统主页</h1><ul><li><a href="#">用户管理</a></li><li><a href="#">商品管理</a></li><li><a href="#">订单管理</a></li><li><a href="#">物流管理</a></li></ul></body></html>
login.jsp
<%@page contentType="text/html;utf-8" pageEncoding="utf-8" isELIgnored="false" %><!doctype html><html lang="en"><head><meta charset="UTF-8"><meta name="viewport"content="width=device-width, user-scalable=no, initial-scale=1.0, maximum-scale=1.0, minimum-scale=1.0"><meta http-equiv="X-UA-Compatible" content="ie=edge"><title>Document</title></head><body><h1>登录界面</h1><form action="${pageContext.request.contextPath}/user/login" method="post">用户名:<input type="text" name="username" > <br/>密码 : <input type="text" name="password"> <br><input type="submit" value="登录"></form></body></html>
4.简单测试
访问:http://localhost:8080/shiro/index.jsp
由于没有验证成功,会跳转到登录页面

目前项目结构:
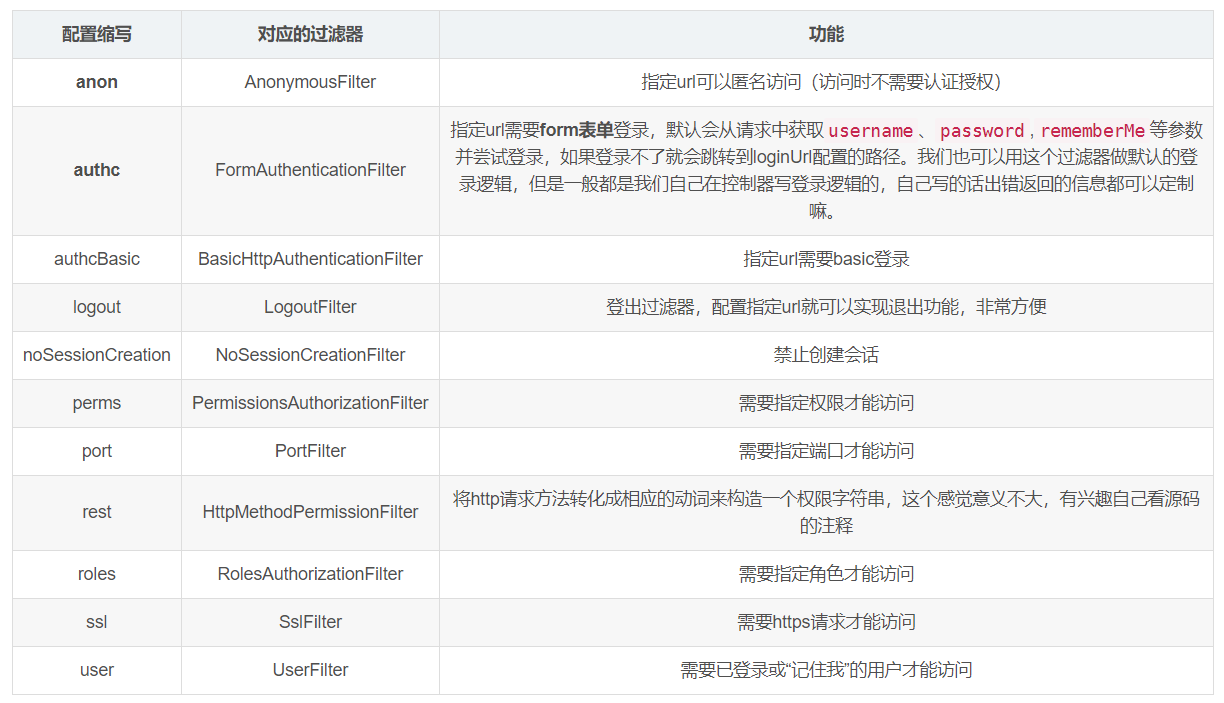
6.4 常见过滤器
- 注意: shiro提供和多个默认的过滤器,我们可以用这些过滤器来配置控制指定url的权限:
6.5 认证和退出实现
6.5.1 登录实现
1.login.jsp
<%@page contentType="text/html;utf-8" pageEncoding="utf-8" isELIgnored="false" %><!doctype html><html lang="en"><head><meta charset="UTF-8"><meta name="viewport"content="width=device-width, user-scalable=no, initial-scale=1.0, maximum-scale=1.0, minimum-scale=1.0"><meta http-equiv="X-UA-Compatible" content="ie=edge"><title>Document</title></head><body><h1>登录界面</h1><form action="${pageContext.request.contextPath}/user/login" method="post">用户名:<input type="text" name="username" > <br/>密码 : <input type="text" name="password"> <br><input type="submit" value="登录"></form></body></html>

2.UserController
package com.lut.controller;import org.apache.shiro.SecurityUtils;import org.apache.shiro.authc.IncorrectCredentialsException;import org.apache.shiro.authc.UnknownAccountException;import org.apache.shiro.authc.UsernamePasswordToken;import org.apache.shiro.subject.Subject;import org.springframework.beans.factory.annotation.Autowired;import org.springframework.stereotype.Controller;import org.springframework.web.bind.annotation.RequestMapping;import javax.servlet.ServletOutputStream;import javax.servlet.http.HttpServletResponse;import javax.servlet.http.HttpSession;import java.io.IOException;@Controller@RequestMapping("user")public class UserController {/*** 用来处理身份认证* @param username* @param password* @return*/@RequestMapping("login")public String login(String username, String password) {try {//获取主体对象Subject subject = SecurityUtils.getSubject();subject.login(new UsernamePasswordToken(username, password));return "redirect:/index.jsp";} catch (UnknownAccountException e) {e.printStackTrace();System.out.println("用户名错误!");} catch (IncorrectCredentialsException e) {e.printStackTrace();System.out.println("密码错误!");} catch (Exception e) {e.printStackTrace();System.out.println(e.getMessage());}return "redirect:/login.jsp";}}
- 在认证过程中使用subject.login进行认证
3.自定义Realm
package com.lut.shiro.realms;import org.apache.shiro.authc.AuthenticationException;import org.apache.shiro.authc.AuthenticationInfo;import org.apache.shiro.authc.AuthenticationToken;import org.apache.shiro.authc.SimpleAuthenticationInfo;import org.apache.shiro.authz.AuthorizationInfo;import org.apache.shiro.authz.SimpleAuthorizationInfo;import org.apache.shiro.realm.AuthorizingRealm;import org.apache.shiro.subject.PrincipalCollection;import org.springframework.util.CollectionUtils;import org.springframework.util.ObjectUtils;import java.util.List;//自定义realmpublic class CustomerRealm extends AuthorizingRealm {@Overrideprotected AuthorizationInfo doGetAuthorizationInfo(PrincipalCollection principals) {return null;}@Overrideprotected AuthenticationInfo doGetAuthenticationInfo(AuthenticationToken token) throws AuthenticationException {System.out.println("=============");//从传过来的token获取到的用户名String principal = (String) token.getPrincipal();System.out.println("用户名"+principal);//假设是从数据库获得的 用户名,密码String password_db="123";String username_db="zhangsan";if (username_db.equals(principal)){// SimpleAuthenticationInfo simpleAuthenticationInfo =return new SimpleAuthenticationInfo(principal,"123", this.getName());}return null;}}
4.ShiroConfig
主要的Shiro配置类中声明:哪些是需要验证的资源,哪些是公开的资源
注意:先配置公共资源,后配置需要认证/授权的资源
此时认证功能没有md5和随机盐的认证
package com.lut.config;import com.lut.shiro.realms.CustomerRealm;import org.apache.shiro.authc.credential.HashedCredentialsMatcher;import org.apache.shiro.realm.Realm;import org.apache.shiro.spring.web.ShiroFilterFactoryBean;import org.apache.shiro.web.mgt.DefaultWebSecurityManager;import org.springframework.context.annotation.Bean;import org.springframework.context.annotation.Configuration;import java.util.HashMap;import java.util.Map;/*** 用来整合shiro框架相关的配置类*/@Configurationpublic class ShiroConfig {//1.创建shiroFilter //负责拦截所有请求@Beanpublic ShiroFilterFactoryBean getShiroFilterFactoryBean(DefaultWebSecurityManager defaultWebSecurityManager){ShiroFilterFactoryBean shiroFilterFactoryBean = new ShiroFilterFactoryBean();//给filter设置安全管理器shiroFilterFactoryBean.setSecurityManager(defaultWebSecurityManager);//配置系统受限资源//配置系统公共资源Map<String,String> map = new HashMap<String,String>();map.put("/user/login","anon");//anon 设置为公共资源 放行资源放在下面map.put("/user/register","anon");//anon 设置为公共资源 放行资源放在下面map.put("/register.jsp","anon");//anon 设置为公共资源 放行资源放在下面map.put("/user/getImage","anon");map.put("/**","authc");//authc 请求这个资源需要认证和授权//默认认证界面路径---当认证不通过时跳转shiroFilterFactoryBean.setLoginUrl("/login.jsp");shiroFilterFactoryBean.setFilterChainDefinitionMap(map);return shiroFilterFactoryBean;}//2.创建安全管理器@Beanpublic DefaultWebSecurityManager getDefaultWebSecurityManager(Realm realm){DefaultWebSecurityManager defaultWebSecurityManager = new DefaultWebSecurityManager();//给安全管理器设置defaultWebSecurityManager.setRealm(realm);return defaultWebSecurityManager;}//3.创建自定义realm@Beanpublic Realm getRealm(){CustomerRealm customerRealm = new CustomerRealm();return customerRealm;}}
6.5.2 退出认证
1.index.jsp
添加登出链接
<%@page contentType="text/html;utf-8" pageEncoding="utf-8" isELIgnored="false" %><!doctype html><html lang="en"><head><meta charset="UTF-8"><meta name="viewport"content="width=device-width, user-scalable=no, initial-scale=1.0, maximum-scale=1.0, minimum-scale=1.0"><meta http-equiv="X-UA-Compatible" content="ie=edge"><title>Document</title></head><body><%--受限资源--%><h1>系统主页</h1><a href="${pageContext.request.contextPath}/user/logout">退出登录</a><ul><li><a href="#">用户管理</a></li><li><a href="#">商品管理</a></li><li><a href="#">订单管理</a></li><li><a href="#">物流管理</a></li></ul></body></html>
2.UserController
package com.lut.controller;import org.apache.shiro.SecurityUtils;import org.apache.shiro.authc.IncorrectCredentialsException;import org.apache.shiro.authc.UnknownAccountException;import org.apache.shiro.authc.UsernamePasswordToken;import org.apache.shiro.subject.Subject;import org.springframework.beans.factory.annotation.Autowired;import org.springframework.stereotype.Controller;import org.springframework.web.bind.annotation.RequestMapping;import javax.servlet.ServletOutputStream;import javax.servlet.http.HttpServletResponse;import javax.servlet.http.HttpSession;import java.io.IOException;@Controller@RequestMapping("user")public class UserController {/*** 退出登录*/@RequestMapping("logout")public String logout() {Subject subject = SecurityUtils.getSubject();subject.logout();//退出用户return "redirect:/login.jsp";}/*** 用来处理身份认证* @param username* @param password* @return*/@RequestMapping("login")public String login(String username, String password) {try {//获取主体对象Subject subject = SecurityUtils.getSubject();subject.login(new UsernamePasswordToken(username, password));return "redirect:/index.jsp";} catch (UnknownAccountException e) {e.printStackTrace();System.out.println("用户名错误!");} catch (IncorrectCredentialsException e) {e.printStackTrace();System.out.println("密码错误!");} catch (Exception e) {e.printStackTrace();System.out.println(e.getMessage());}return "redirect:/login.jsp";}}
3.测试
登录正常,登出正常,未登录和登出后不能访问index.jsp
6.7 MD5、Salt的认证实现
6.7.1 用户注册+随机盐处理
1.导入依赖
<!--mybatis相关依赖--><dependency><groupId>org.mybatis.spring.boot</groupId><artifactId>mybatis-spring-boot-starter</artifactId><version>2.1.2</version></dependency><!--mysql--><dependency><groupId>mysql</groupId><artifactId>mysql-connector-java</artifactId><version>5.1.38</version></dependency><!--druid--><dependency><groupId>com.alibaba</groupId><artifactId>druid</artifactId><version>1.1.19</version></dependency>
2.application.properties
spring.datasource.type=com.alibaba.druid.pool.DruidDataSourcespring.datasource.driver-class-name=com.mysql.jdbc.Driverspring.datasource.url=jdbc:mysql://localhost:3306/shiro?characterEncoding=UTF-8spring.datasource.username=rootspring.datasource.password=88888888mybatis.type-aliases-package=com.lut.entitymybatis.mapper-locations=classpath:mapper/*.xml
3.创建数据库
SET NAMES utf8mb4;SET FOREIGN_KEY_CHECKS = 0;-- ------------------------------ Table structure for t_user-- ----------------------------DROP TABLE IF EXISTS `t_user`;CREATE TABLE `t_user` (`id` int(6) NOT NULL AUTO_INCREMENT,`username` varchar(40) DEFAULT NULL,`password` varchar(40) DEFAULT NULL,`salt` varchar(255) DEFAULT NULL,PRIMARY KEY (`id`)) ENGINE=InnoDB AUTO_INCREMENT=2 DEFAULT CHARSET=utf8;SET FOREIGN_KEY_CHECKS = 1;

4.创建entity
package com.lut.entity;import lombok.AllArgsConstructor;import lombok.Data;import lombok.NoArgsConstructor;import lombok.experimental.Accessors;@Data@Accessors(chain = true)@AllArgsConstructor@NoArgsConstructorpublic class User {private String id;private String username;private String password;private String salt;}
5.创建DAO接口
package com.lut.dao;import com.lut.entity.User;import org.apache.ibatis.annotations.Mapper;@Mapperpublic interface UserDao {void save(User user);}
6.开发mapper配置文件
注意:mapper文件的位置要在 application.properties配置的目录下面
注意:mapper文件的命名 与 Dao接口保持一致
<?xml version="1.0" encoding="UTF-8" ?><!DOCTYPE mapperPUBLIC "-//mybatis.org//DTD Config 3.0//EN""http://mybatis.org/dtd/mybatis-3-mapper.dtd"><mapper namespace="com.lut.dao.UserDao"><insert id="save" parameterType="User" useGeneratedKeys="true" keyProperty="id">insert into t_user values(#{id},#{username},#{password},#{salt})</insert></mapper>
在图中,标红的地方要保持命名一致,不然会有莫名其妙的BUG
7.开发service接口
package com.lut.service;import com.lut.entity.User;public interface UserService {//注册用户方法void register(User user);}
8.创建salt工具类
package com.lut.utils;import java.util.Random;public class SaltUtils {/*** 生成salt的静态方法* @param n* @return*/public static String getSalt(int n){char[] chars = "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz01234567890!@#$%^&*()".toCharArray();StringBuilder sb = new StringBuilder();for (int i = 0; i < n; i++) {char aChar = chars[new Random().nextInt(chars.length)];sb.append(aChar);}return sb.toString();}}
9.开发service实现类
package com.lut.service;import com.lut.dao.UserDao;import com.lut.entity.User;import com.lut.utils.SaltUtils;import org.apache.shiro.crypto.hash.Md5Hash;import org.springframework.beans.factory.annotation.Autowired;import org.springframework.transaction.annotation.Transactional;import org.springframework.stereotype.Service;@Service@Transactionalpublic class UserServiceImpl implements UserService {@Autowiredprivate UserDao userDAO;@Overridepublic void register(User user) {//处理业务调用dao//1.生成随机盐String salt = SaltUtils.getSalt(8);//2.将随机盐保存到数据user.setSalt(salt);//3.明文密码进行md5 + salt + hash散列Md5Hash md5Hash = new Md5Hash(user.getPassword(),salt,1024);user.setPassword(md5Hash.toHex());userDAO.save(user);}}
10.开发Controller
@Controller@RequestMapping("user")public class UserController {@Autowiredprivate UserService userService;/*** 用户注册*/@RequestMapping("register")public String register(User user) {try {userService.register(user);return "redirect:/login.jsp";}catch (Exception e){e.printStackTrace();return "redirect:/register.jsp";}}}
11.设置公共资源
在ShiroConfig中添加
map.put("/user/register","anon");//anon 设置为公共资源map.put("/register.jsp","anon");//anon 设置为公共资源
12.测试
添加成功
6.7.2 开发数据库认证
1.开发DAO
@Mapperpublic interface UserDAO {void save(User user);//根据身份信息认证的方法User findByUserName(String username);}
2.开发mapper配置文件
<select id="findByUserName" parameterType="String" resultType="User">select id,username,password,salt from t_userwhere username = #{username}</select>
3.开发Service接口
public interface UserService {//注册用户方法void register(User user);//根据用户名查询业务的方法User findByUserName(String username);}
4.开发Service实现类
注意:一定别忘记添加注解:@Service(“userService”)
@Service("userService")@Transactionalpublic class UserServiceImpl implements UserService {@Autowiredprivate UserDAO userDAO;@Overridepublic User findByUserName(String username) {return userDAO.findByUserName(username);}}
5.开发工厂工具类
在工厂中获取bean对象的工具类
ApplicationContextUtils
package com.lut.utils;import org.springframework.beans.BeansException;import org.springframework.context.ApplicationContext;import org.springframework.context.ApplicationContextAware;import org.springframework.stereotype.Component;@Componentpublic class ApplicationContextUtils implements ApplicationContextAware {private static ApplicationContext context;@Overridepublic void setApplicationContext(ApplicationContext applicationContext) throws BeansException {this.context = applicationContext;}//根据bean名字获取工厂中指定bean 对象public static Object getBean(String beanName){System.out.println("beanName"+beanName);Object object=context.getBean(beanName);System.out.println("object"+object);return context.getBean(beanName);}}
6.修改自定义realm
//自定义realmpublic class CustomerRealm extends AuthorizingRealm {@Overrideprotected AuthorizationInfo doGetAuthorizationInfo(PrincipalCollection principals) {return null;}@Overrideprotected AuthenticationInfo doGetAuthenticationInfo(AuthenticationToken token) throws AuthenticationException {//根据身份信息//从传过来的token获取到的用户名String principal = (String) token.getPrincipal();//在工厂中获取service对象UserService userService = (UserService) ApplicationContextUtils.getBean("userService");//根据身份信息查询User user = userService.findByUserName(principal);System.out.println("User:"+user);//用户不为空if(!ObjectUtils.isEmpty(user)){//返回数据库信息SimpleAuthenticationInfo simpleAuthenticationInfo = new SimpleAuthenticationInfo(user.getUsername(), user.getPassword(),ByteSource.Util.bytes(user.getSalt()), this.getName());return simpleAuthenticationInfo;}return null;}}
7.修改ShiroConfig中realm
使用凭证匹配器以及hash散列
以及在 getShiroFilterFactoryBean 中添加公共资源
package com.lut.config;import com.lut.shiro.realms.CustomerRealm;import org.apache.shiro.authc.credential.HashedCredentialsMatcher;import org.apache.shiro.realm.Realm;import org.apache.shiro.spring.web.ShiroFilterFactoryBean;import org.apache.shiro.web.mgt.DefaultWebSecurityManager;import org.springframework.context.annotation.Bean;import org.springframework.context.annotation.Configuration;import java.util.HashMap;import java.util.Map;/*** 用来整合shiro框架相关的配置类*/@Configurationpublic class ShiroConfig {//1.创建shiroFilter //负责拦截所有请求@Beanpublic ShiroFilterFactoryBean getShiroFilterFactoryBean(DefaultWebSecurityManager defaultWebSecurityManager){ShiroFilterFactoryBean shiroFilterFactoryBean = new ShiroFilterFactoryBean();//给filter设置安全管理器shiroFilterFactoryBean.setSecurityManager(defaultWebSecurityManager);//配置系统受限资源//配置系统公共资源Map<String,String> map = new HashMap<String,String>();map.put("/user/login","anon");//anon 设置为公共资源 放行资源放在下面map.put("/user/register","anon");//anon 设置为公共资源 放行资源放在下面map.put("/register.jsp","anon");//anon 设置为公共资源 放行资源放在下面map.put("/user/getImage","anon");map.put("/**","authc");//authc 请求这个资源需要认证和授权//默认认证界面路径---当认证不通过时跳转shiroFilterFactoryBean.setLoginUrl("/login.jsp");shiroFilterFactoryBean.setFilterChainDefinitionMap(map);return shiroFilterFactoryBean;}//2.创建安全管理器@Beanpublic DefaultWebSecurityManager getDefaultWebSecurityManager(Realm realm){DefaultWebSecurityManager defaultWebSecurityManager = new DefaultWebSecurityManager();//给安全管理器设置defaultWebSecurityManager.setRealm(realm);return defaultWebSecurityManager;}@Beanpublic Realm getRealm(){CustomerRealm customerRealm = new CustomerRealm();//设置hashed凭证匹配器HashedCredentialsMatcher credentialsMatcher = new HashedCredentialsMatcher();//设置md5加密credentialsMatcher.setHashAlgorithmName("md5");//设置散列次数credentialsMatcher.setHashIterations(1024);customerRealm.setCredentialsMatcher(credentialsMatcher);return customerRealm;}}
8.启动测试

6.8 授权实现
6.8.1 没有数据库
1.页面资源授权
<%@page contentType="text/html;utf-8" pageEncoding="utf-8" isELIgnored="false" %><%@taglib prefix="shiro" uri="http://shiro.apache.org/tags" %><!doctype html><html lang="en"><head><meta charset="UTF-8"><meta name="viewport"content="width=device-width, user-scalable=no, initial-scale=1.0, maximum-scale=1.0, minimum-scale=1.0"><meta http-equiv="X-UA-Compatible" content="ie=edge"><title>Document</title></head><body><%-- 受限资源--%><h1>系统主页</h1><a href="${pageContext.request.contextPath}/user/logout">退出登录</a><ul><shiro:hasAnyRoles name="user_manager,admin,addinfo_manager"><li><a href="">用户管理</a><ul><shiro:hasPermission name="user:add:*"><li><a href="">添加</a></li></shiro:hasPermission><shiro:hasPermission name="user:delete:*"><li><a href="">删除</a></li></shiro:hasPermission><shiro:hasPermission name="user:update:*"><li><a href="">修改</a></li></shiro:hasPermission><shiro:hasPermission name="user:find:*"><li><a href="">查询</a></li></shiro:hasPermission></ul></li></shiro:hasAnyRoles><shiro:hasAnyRoles name="order_manager,admin,addinfo_manager"><li><a href="">订单管理</a></li><ul><shiro:hasPermission name="order:add:*"><li><a href="">添加</a></li></shiro:hasPermission><shiro:hasPermission name="order:delete:*"><li><a href="">删除</a></li></shiro:hasPermission><shiro:hasPermission name="order:update:*"><li><a href="">修改</a></li></shiro:hasPermission><shiro:hasPermission name="order:find:*"><li><a href="">查询</a></li></shiro:hasPermission></ul></shiro:hasAnyRoles><shiro:hasRole name="admin"><li><a href="">商品管理</a></li><li><a href="">物流管理</a></li></shiro:hasRole><shiro:hasRole name="user"><li><a href="">仅普通用户可见</a></li><li><a href="">公共资源</a></li></shiro:hasRole></ul></body></html>
2.代码方式授权
@RequestMapping("save")public String save(){System.out.println("进入方法");//基于角色//获取主体对象Subject subject = SecurityUtils.getSubject();//代码方式if (subject.hasRole("admin")) {System.out.println("保存订单!");}else{System.out.println("无权访问!");}//基于权限字符串//....return "redirect:/index.jsp";}
3.方法调用授权
- @RequiresRoles 用来基于角色进行授权
- @RequiresPermissions 用来基于权限进行授权 ```java import org.apache.shiro.authz.annotation.RequiresPermissions; import org.apache.shiro.authz.annotation.RequiresRoles; import org.springframework.stereotype.Controller; import org.springframework.web.bind.annotation.RequestMapping;
@Controller @RequestMapping(“order”) public class OrderController {
@RequiresRoles(value={"admin","user"})//用来判断角色 同时具有 admin user@RequiresPermissions("user:update:01") //用来判断权限字符串@RequestMapping("save")public String save(){System.out.println("进入方法");return "redirect:/index.jsp";}
}
<a name="xVBHj"></a>### 6.8.2 连接数据库<a name="xtO0f"></a>#### 4.授权数据持久化```sqlSET NAMES utf8mb4;SET FOREIGN_KEY_CHECKS = 0;-- ------------------------------ Table structure for t_perms-- ----------------------------DROP TABLE IF EXISTS `t_perms`;CREATE TABLE `t_pers` (`id` int(6) NOT NULL AUTO_INCREMENT,`name` varchar(80) DEFAULT NULL,`url` varchar(255) DEFAULT NULL,PRIMARY KEY (`id`)) ENGINE=InnoDB DEFAULT CHARSET=utf8;-- ------------------------------ Table structure for t_role-- ----------------------------DROP TABLE IF EXISTS `t_role`;CREATE TABLE `t_role` (`id` int(6) NOT NULL AUTO_INCREMENT,`name` varchar(60) DEFAULT NULL,PRIMARY KEY (`id`)) ENGINE=InnoDB DEFAULT CHARSET=utf8;-- ------------------------------ Table structure for t_role_perms-- ----------------------------DROP TABLE IF EXISTS `t_role_perms`;CREATE TABLE `t_role_perms` (`id` int(6) NOT NULL,`roleid` int(6) DEFAULT NULL,`permsid` int(6) DEFAULT NULL,PRIMARY KEY (`id`)) ENGINE=InnoDB DEFAULT CHARSET=utf8;-- ------------------------------ Table structure for t_user-- ----------------------------DROP TABLE IF EXISTS `t_user`;CREATE TABLE `t_user` (`id` int(6) NOT NULL AUTO_INCREMENT,`username` varchar(40) DEFAULT NULL,`password` varchar(40) DEFAULT NULL,`salt` varchar(255) DEFAULT NULL,PRIMARY KEY (`id`)) ENGINE=InnoDB AUTO_INCREMENT=2 DEFAULT CHARSET=utf8;-- ------------------------------ Table structure for t_user_role-- ----------------------------DROP TABLE IF EXISTS `t_user_role`;CREATE TABLE `t_user_role` (`id` int(6) NOT NULL,`userid` int(6) DEFAULT NULL,`roleid` int(6) DEFAULT NULL,PRIMARY KEY (`id`)) ENGINE=InnoDB DEFAULT CHARSET=utf8;SET FOREIGN_KEY_CHECKS = 1;

5.创建实体类
User
@Data@Accessors(chain = true)@AllArgsConstructor@NoArgsConstructorpublic class User implements Serializable {private String id;private String username;private String password;private String salt;//定义角色集合private List<Role> roles;}
Role
@Data@Accessors(chain = true)@AllArgsConstructor@NoArgsConstructorpublic class Perms implements Serializable {private String id;private String name;private String url;}
6.创建dao方法
//根据用户名查询所有角色User findRolesByUserName(String username);//根据角色id查询权限集合List<Perms> findPermsByRoleId(String id);
7.mapper实现
<resultMap id="userMap" type="User"><id column="uid" property="id"/><result column="username" property="username"/><!--角色信息--><collection property="roles" javaType="list" ofType="Role"><id column="id" property="id"/><result column="rname" property="name"/></collection></resultMap><select id="findRolesByUserName" parameterType="String" resultMap="userMap">SELECT u.id uid,u.username,r.id,r.NAME rnameFROM t_user uLEFT JOIN t_user_role urON u.id=ur.useridLEFT JOIN t_role rON ur.roleid=r.idWHERE u.username=#{username}</select><select id="findPermsByRoleId" parameterType="String" resultType="Perms">SELECT p.id,p.NAME,p.url,r.NAMEFROM t_role rLEFT JOIN t_role_perms rpON r.id=rp.roleidLEFT JOIN t_perms p ON rp.permsid=p.idWHERE r.id=#{id}</select>
8.Service接口
//根据用户名查询所有角色User findRolesByUserName(String username);//根据角色id查询权限集合List<Perms> findPermsByRoleId(String id);
9.Service实现
@Overridepublic List<Perms> findPermsByRoleId(String id) {return userDAO.findPermsByRoleId(id);}@Overridepublic User findRolesByUserName(String username) {return userDAO.findRolesByUserName(username);}
10.修改自定义realm
注意:如果你创建了一个用户,并为这个用户授予了一个角色,但这个角色并未关联任何的 授权字符串,那么调用数据库获得的结果是 List
perms=[null],此时 perms已经被初始化,里面只有一个属性null,使用判空的方法无法判别,此时继续遍历会报出空指针异常,此时应当添加判断条件 perms.get(0)!=null
package com.lut.shiro.realms;import com.lut.entity.Perms;import com.lut.entity.User;import com.lut.service.UserService;import com.lut.utils.ApplicationContextUtils;import org.apache.shiro.authc.AuthenticationException;import org.apache.shiro.authc.AuthenticationInfo;import org.apache.shiro.authc.AuthenticationToken;import org.apache.shiro.authc.SimpleAuthenticationInfo;import org.apache.shiro.authz.AuthorizationInfo;import org.apache.shiro.authz.SimpleAuthorizationInfo;import org.apache.shiro.realm.AuthorizingRealm;import org.apache.shiro.subject.PrincipalCollection;import org.apache.shiro.util.ByteSource;import org.springframework.util.CollectionUtils;import org.springframework.util.ObjectUtils;import java.util.List;//自定义realmpublic class CustomerRealm extends AuthorizingRealm {@Overrideprotected AuthorizationInfo doGetAuthorizationInfo(PrincipalCollection principals) {//获取身份信息String primaryPrincipal = (String) principals.getPrimaryPrincipal();System.out.println("调用授权验证: "+primaryPrincipal);//根据主身份信息获取角色 和 权限信息UserService userService = (UserService) ApplicationContextUtils.getBean("userService");User user = userService.findRolesByUserName(primaryPrincipal);System.out.println("user:"+user);//授权角色信息if(!CollectionUtils.isEmpty(user.getRoles())){SimpleAuthorizationInfo simpleAuthorizationInfo = new SimpleAuthorizationInfo();user.getRoles().forEach(role->{simpleAuthorizationInfo.addRole(role.getName()); //添加角色信息//权限信息List<Perms> perms = userService.findPermsByRoleId(role.getId());System.out.println("perms:"+perms);if(!CollectionUtils.isEmpty(perms) && perms.get(0)!=null ){perms.forEach(perm->{simpleAuthorizationInfo.addStringPermission(perm.getName());});}});return simpleAuthorizationInfo;}return null;}@Overrideprotected AuthenticationInfo doGetAuthenticationInfo(AuthenticationToken token) throws AuthenticationException {//根据身份信息//从传过来的token获取到的用户名String principal = (String) token.getPrincipal();//在工厂中获取service对象UserService userService = (UserService) ApplicationContextUtils.getBean("userService");//根据身份信息查询User user = userService.findByUserName(principal);System.out.println("User:"+user);//用户不为空if(!ObjectUtils.isEmpty(user)){//返回数据库信息SimpleAuthenticationInfo simpleAuthenticationInfo = new SimpleAuthenticationInfo(user.getUsername(), user.getPassword(),ByteSource.Util.bytes(user.getSalt()), this.getName());return simpleAuthenticationInfo;}return null;}}
11.向数据库添加信息
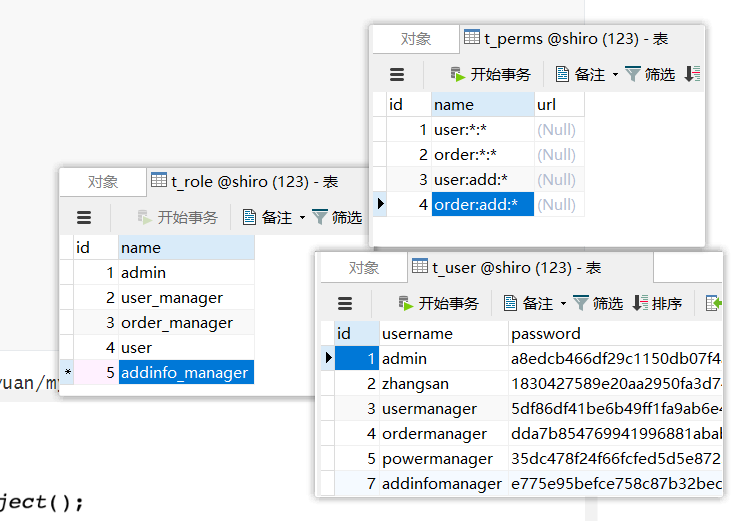
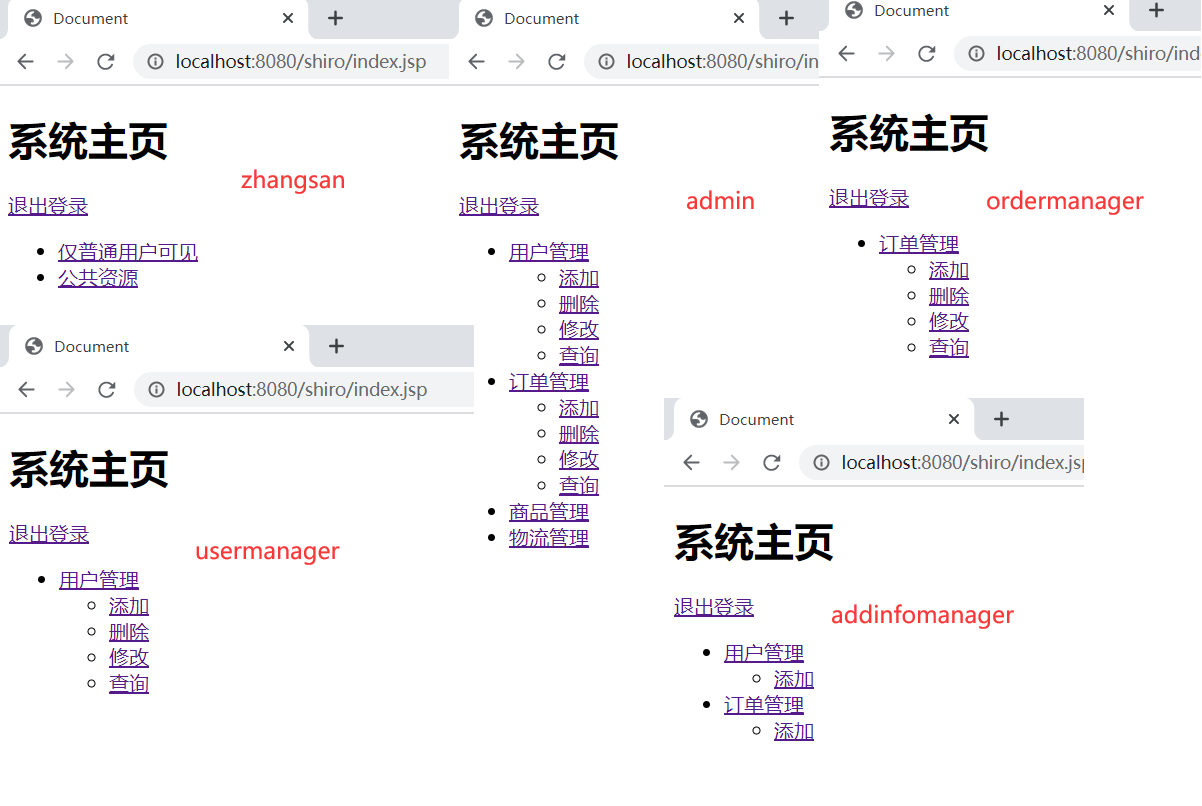
简单来说:
用户 admin 具有 admin的角色,具有 对于 user,order的所有权限
用户 zhangsan 具有 user的角色,没有权限,只能访问公共资源
用户 usermanager 具有 user_manager的角色,具有 对于 user的所有权限
用户 ordermanager 具有 order_manager的角色,具有 对于 order的所有权限
用户 addinfomanager 具有 addinfo_manager的角色,具有 对于 user,order 的添加权限
12.启动测试
6.9 使用CacheManager
6.9.1 Cache 作用
- Cache 缓存: 计算机内存中一段数据
- 作用: 用来减轻DB的访问压力,从而提高系统的查询效率
- 流程:
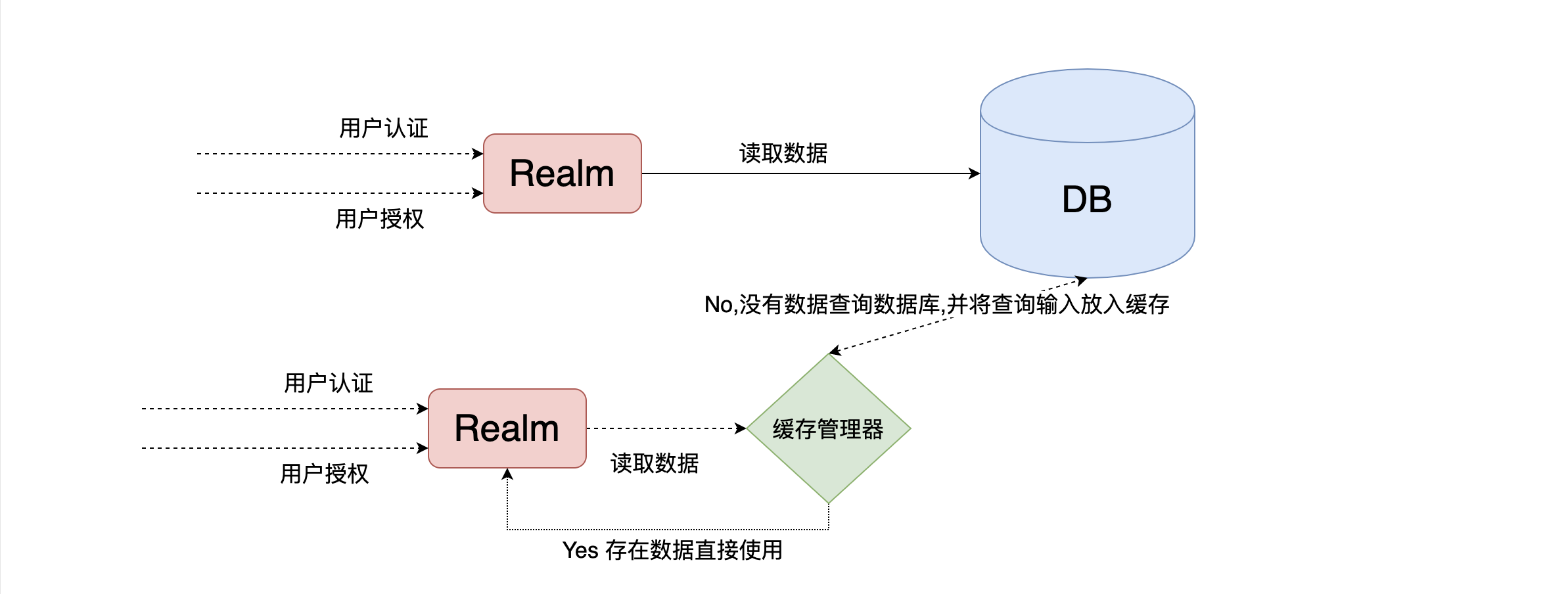
6.9.2 使用shiro中默认EhCache实现缓存
1.引入依赖
<!--引入shiro和ehcache--><dependency><groupId>org.apache.shiro</groupId><artifactId>shiro-ehcache</artifactId><version>1.5.3</version></dependency>
2.开启缓存
//3.创建自定义realm@Beanpublic Realm getRealm(){CustomerRealm customerRealm = new CustomerRealm();//修改凭证校验匹配器HashedCredentialsMatcher credentialsMatcher = new HashedCredentialsMatcher();//设置加密算法为md5credentialsMatcher.setHashAlgorithmName("MD5");//设置散列次数credentialsMatcher.setHashIterations(1024);customerRealm.setCredentialsMatcher(credentialsMatcher);//开启缓存管理器customerRealm.setCachingEnabled(true);customerRealm.setAuthorizationCachingEnabled(true);customerRealm.setAuthorizationCachingEnabled(true);customerRealm.setCacheManager(new EhCacheManager());return customerRealm;}
3.启动刷新页面进行测试
- 注意:如果控制台没有任何sql展示说明缓存已经开启
6.9.3 shiro中使用Redis作为缓存实现
1.引入redis依赖
<!--redis整合springboot--><dependency><groupId>org.springframework.boot</groupId><artifactId>spring-boot-starter-data-redis</artifactId></dependency>
2.配置redis连接
spring.redis.port=6379spring.redis.host=localhostspring.redis.database=0
3.启动redis服务
4.开发RedisCacheManager
自定义shiro缓存管理器
package com.lut.shiro.cache;import org.apache.shiro.cache.Cache;import org.apache.shiro.cache.CacheException;import org.apache.shiro.cache.CacheManager;//自定义shiro缓存管理器public class RedisCacheManager implements CacheManager {//参数1:认证或者是授权缓存的统一名称@Overridepublic <K, V> Cache<K, V> getCache(String cacheName) throws CacheException {System.out.println(cacheName);return new RedisCache<K,V>(cacheName);}}
5.开RedisCache实现
自定义redis缓存的实现
package com.lut.shiro.cache;import com.lut.utils.ApplicationContextUtils;import org.apache.shiro.cache.Cache;import org.apache.shiro.cache.CacheException;import org.springframework.data.redis.core.RedisTemplate;import org.springframework.data.redis.serializer.StringRedisSerializer;import java.util.Collection;import java.util.Set;//自定义redis缓存的实现public class RedisCache<k,v> implements Cache<k,v> {private String cacheName;public RedisCache() {}public RedisCache(String cacheName) {this.cacheName = cacheName;}@Overridepublic v get(k k) throws CacheException {System.out.println("get key:"+k);return (v) getRedisTemplate().opsForHash().get(this.cacheName,k.toString());}@Overridepublic v put(k k, v v) throws CacheException {System.out.println("put key: "+k);System.out.println("put value:"+v);getRedisTemplate().opsForHash().put(this.cacheName,k.toString(),v);return null;}@Overridepublic v remove(k k) throws CacheException {System.out.println("=============remove=============");return (v) getRedisTemplate().opsForHash().delete(this.cacheName,k.toString());}@Overridepublic void clear() throws CacheException {System.out.println("=============clear==============");getRedisTemplate().delete(this.cacheName);}@Overridepublic int size() {return getRedisTemplate().opsForHash().size(this.cacheName).intValue();}@Overridepublic Set<k> keys() {return getRedisTemplate().opsForHash().keys(this.cacheName);}@Overridepublic Collection<v> values() {return getRedisTemplate().opsForHash().values(this.cacheName);}private RedisTemplate getRedisTemplate(){RedisTemplate redisTemplate = (RedisTemplate) ApplicationContextUtils.getBean("redisTemplate");redisTemplate.setKeySerializer(new StringRedisSerializer());redisTemplate.setHashKeySerializer(new StringRedisSerializer());return redisTemplate;}}
6.启动项目测试发现报错


- 错误解释: 由于shiro中提供的simpleByteSource实现没有实现序列化,所有在认证时出现错误信息
- 解决方案:需要自动salt实现序列化
- 实现 实体类 序列化
- 自定义salt实现 实现序列化接口
package com.lut.shiro.salt;import org.apache.shiro.codec.Base64;import org.apache.shiro.codec.CodecSupport;import org.apache.shiro.codec.Hex;import org.apache.shiro.util.ByteSource;import java.io.File;import java.io.InputStream;import java.io.Serializable;import java.util.Arrays;//自定义salt实现 实现序列化接口public class MyByteSource implements ByteSource, Serializable {private byte[] bytes;private String cachedHex;private String cachedBase64;public MyByteSource(){}public MyByteSource(byte[] bytes) {this.bytes = bytes;}public MyByteSource(char[] chars) {this.bytes = CodecSupport.toBytes(chars);}public MyByteSource(String string) {this.bytes = CodecSupport.toBytes(string);}public MyByteSource(ByteSource source) {this.bytes = source.getBytes();}public MyByteSource(File file) {this.bytes = (new com.lut.shiro.salt.MyByteSource.BytesHelper()).getBytes(file);}public MyByteSource(InputStream stream) {this.bytes = (new com.lut.shiro.salt.MyByteSource.BytesHelper()).getBytes(stream);}public static boolean isCompatible(Object o) {return o instanceof byte[] || o instanceof char[] || o instanceof String || o instanceof ByteSource || o instanceof File || o instanceof InputStream;}public byte[] getBytes() {return this.bytes;}public boolean isEmpty() {return this.bytes == null || this.bytes.length == 0;}public String toHex() {if (this.cachedHex == null) {this.cachedHex = Hex.encodeToString(this.getBytes());}return this.cachedHex;}public String toBase64() {if (this.cachedBase64 == null) {this.cachedBase64 = Base64.encodeToString(this.getBytes());}return this.cachedBase64;}public String toString() {return this.toBase64();}public int hashCode() {return this.bytes != null && this.bytes.length != 0 ? Arrays.hashCode(this.bytes) : 0;}public boolean equals(Object o) {if (o == this) {return true;} else if (o instanceof ByteSource) {ByteSource bs = (ByteSource)o;return Arrays.equals(this.getBytes(), bs.getBytes());} else {return false;}}private static final class BytesHelper extends CodecSupport {private BytesHelper() {}public byte[] getBytes(File file) {return this.toBytes(file);}public byte[] getBytes(InputStream stream) {return this.toBytes(stream);}}
- 在realm中使用自定义salt```java@Overrideprotected AuthenticationInfo doGetAuthenticationInfo(AuthenticationToken token) throws AuthenticationException {System.out.println("==========================");//根据身份信息String principal = (String) token.getPrincipal();//在工厂中获取service对象UserService userService = (UserService) ApplicationContextUtils.getBean("userService");User user = userService.findByUserName(principal);if(!ObjectUtils.isEmpty(user)){return new SimpleAuthenticationInfo(user.getUsername(),user.getPassword(),new MyByteSource(user.getSalt()),this.getName());}return null;}

7.再次启动测试,发现可以成功放入redis缓存
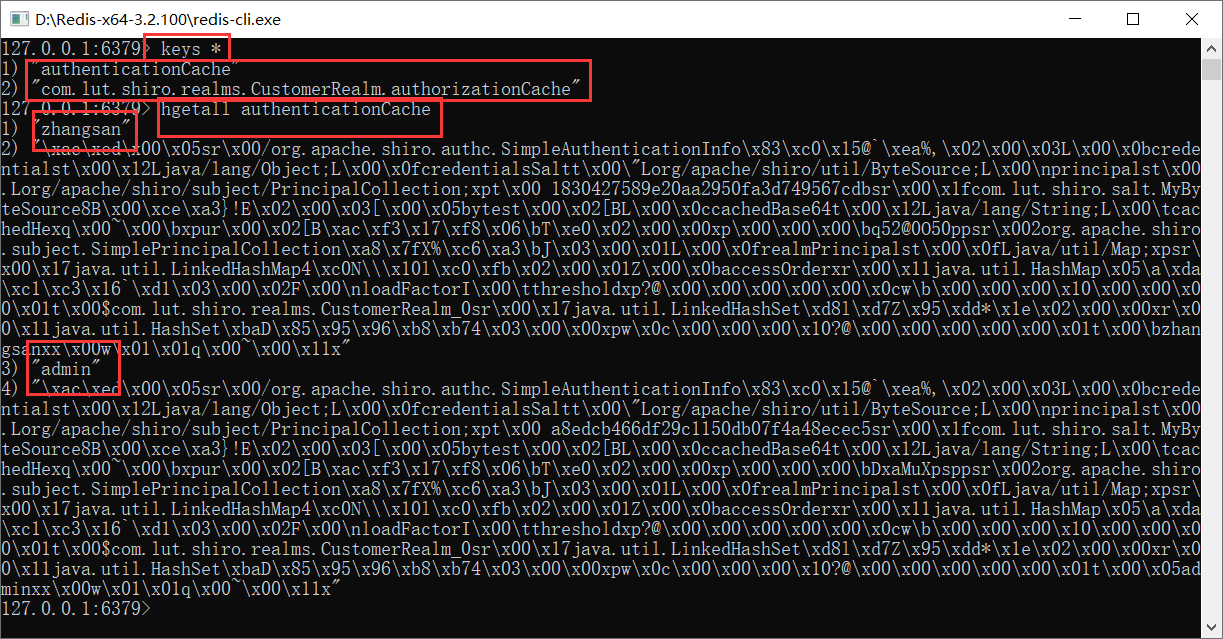

6.9.4 加入验证码验证
1.验证码工具类
package com.lut.utils;import javax.imageio.ImageIO;import java.awt.*;import java.awt.geom.AffineTransform;import java.awt.image.BufferedImage;import java.io.File;import java.io.FileOutputStream;import java.io.IOException;import java.io.OutputStream;import java.util.Arrays;import java.util.Random;/***@创建人 cx*@创建时间 2018/11/27 17:36*@描述 验证码生成*/public class VerifyCodeUtils{//使用到Algerian字体,系统里没有的话需要安装字体,字体只显示大写,去掉了1,0,i,o几个容易混淆的字符public static final String VERIFY_CODES = "23456789ABCDEFGHJKLMNPQRSTUVWXYZ";private static Random random = new Random();/*** 使用系统默认字符源生成验证码* @param verifySize 验证码长度* @return*/public static String generateVerifyCode(int verifySize){return generateVerifyCode(verifySize, VERIFY_CODES);}/*** 使用指定源生成验证码* @param verifySize 验证码长度* @param sources 验证码字符源* @return*/public static String generateVerifyCode(int verifySize, String sources){if(sources == null || sources.length() == 0){sources = VERIFY_CODES;}int codesLen = sources.length();Random rand = new Random(System.currentTimeMillis());StringBuilder verifyCode = new StringBuilder(verifySize);for(int i = 0; i < verifySize; i++){verifyCode.append(sources.charAt(rand.nextInt(codesLen-1)));}return verifyCode.toString();}/*** 生成随机验证码文件,并返回验证码值* @param w* @param h* @param outputFile* @param verifySize* @return* @throws IOException*/public static String outputVerifyImage(int w, int h, File outputFile, int verifySize) throws IOException{String verifyCode = generateVerifyCode(verifySize);outputImage(w, h, outputFile, verifyCode);return verifyCode;}/*** 输出随机验证码图片流,并返回验证码值* @param w* @param h* @param os* @param verifySize* @return* @throws IOException*/public static String outputVerifyImage(int w, int h, OutputStream os, int verifySize) throws IOException{String verifyCode = generateVerifyCode(verifySize);outputImage(w, h, os, verifyCode);return verifyCode;}/*** 生成指定验证码图像文件* @param w* @param h* @param outputFile* @param code* @throws IOException*/public static void outputImage(int w, int h, File outputFile, String code) throws IOException{if(outputFile == null){return;}File dir = outputFile.getParentFile();if(!dir.exists()){dir.mkdirs();}try{outputFile.createNewFile();FileOutputStream fos = new FileOutputStream(outputFile);outputImage(w, h, fos, code);fos.close();} catch(IOException e){throw e;}}/*** 输出指定验证码图片流* @param w* @param h* @param os* @param code* @throws IOException*/public static void outputImage(int w, int h, OutputStream os, String code) throws IOException{int verifySize = code.length();BufferedImage image = new BufferedImage(w, h, BufferedImage.TYPE_INT_RGB);Random rand = new Random();Graphics2D g2 = image.createGraphics();g2.setRenderingHint(RenderingHints.KEY_ANTIALIASING,RenderingHints.VALUE_ANTIALIAS_ON);Color[] colors = new Color[5];Color[] colorSpaces = new Color[] { Color.WHITE, Color.CYAN,Color.GRAY, Color.LIGHT_GRAY, Color.MAGENTA, Color.ORANGE,Color.PINK, Color.YELLOW };float[] fractions = new float[colors.length];for(int i = 0; i < colors.length; i++){colors[i] = colorSpaces[rand.nextInt(colorSpaces.length)];fractions[i] = rand.nextFloat();}Arrays.sort(fractions);g2.setColor(Color.GRAY);// 设置边框色g2.fillRect(0, 0, w, h);Color c = getRandColor(200, 250);g2.setColor(c);// 设置背景色g2.fillRect(0, 2, w, h-4);//绘制干扰线Random random = new Random();g2.setColor(getRandColor(160, 200));// 设置线条的颜色for (int i = 0; i < 20; i++) {int x = random.nextInt(w - 1);int y = random.nextInt(h - 1);int xl = random.nextInt(6) + 1;int yl = random.nextInt(12) + 1;g2.drawLine(x, y, x + xl + 40, y + yl + 20);}// 添加噪点float yawpRate = 0.05f;// 噪声率int area = (int) (yawpRate * w * h);for (int i = 0; i < area; i++) {int x = random.nextInt(w);int y = random.nextInt(h);int rgb = getRandomIntColor();image.setRGB(x, y, rgb);}shear(g2, w, h, c);// 使图片扭曲g2.setColor(getRandColor(100, 160));int fontSize = h-4;Font font = new Font("Algerian", Font.ITALIC, fontSize);g2.setFont(font);char[] chars = code.toCharArray();for(int i = 0; i < verifySize; i++){AffineTransform affine = new AffineTransform();affine.setToRotation(Math.PI / 4 * rand.nextDouble() * (rand.nextBoolean() ? 1 : -1), (w / verifySize) * i + fontSize/2, h/2);g2.setTransform(affine);g2.drawChars(chars, i, 1, ((w-10) / verifySize) * i + 5, h/2 + fontSize/2 - 10);}g2.dispose();ImageIO.write(image, "jpg", os);}private static Color getRandColor(int fc, int bc) {if (fc > 255)fc = 255;if (bc > 255)bc = 255;int r = fc + random.nextInt(bc - fc);int g = fc + random.nextInt(bc - fc);int b = fc + random.nextInt(bc - fc);return new Color(r, g, b);}private static int getRandomIntColor() {int[] rgb = getRandomRgb();int color = 0;for (int c : rgb) {color = color << 8;color = color | c;}return color;}private static int[] getRandomRgb() {int[] rgb = new int[3];for (int i = 0; i < 3; i++) {rgb[i] = random.nextInt(255);}return rgb;}private static void shear(Graphics g, int w1, int h1, Color color) {shearX(g, w1, h1, color);shearY(g, w1, h1, color);}private static void shearX(Graphics g, int w1, int h1, Color color) {int period = random.nextInt(2);boolean borderGap = true;int frames = 1;int phase = random.nextInt(2);for (int i = 0; i < h1; i++) {double d = (double) (period >> 1)* Math.sin((double) i / (double) period+ (6.2831853071795862D * (double) phase)/ (double) frames);g.copyArea(0, i, w1, 1, (int) d, 0);if (borderGap) {g.setColor(color);g.drawLine((int) d, i, 0, i);g.drawLine((int) d + w1, i, w1, i);}}}private static void shearY(Graphics g, int w1, int h1, Color color) {int period = random.nextInt(40) + 10; // 50;boolean borderGap = true;int frames = 20;int phase = 7;for (int i = 0; i < w1; i++) {double d = (double) (period >> 1)* Math.sin((double) i / (double) period+ (6.2831853071795862D * (double) phase)/ (double) frames);g.copyArea(i, 0, 1, h1, 0, (int) d);if (borderGap) {g.setColor(color);g.drawLine(i, (int) d, i, 0);g.drawLine(i, (int) d + h1, i, h1);}}}public static void main(String[] args) throws IOException {//获取验证码String s = generateVerifyCode(4);//将验证码放入图片中outputImage(260,60,new File("/Users/chenyannan/Desktop/安工资料/aa.jpg"),s);System.out.println(s);}}
2.开发页面加入验证码
<form action="${pageContext.request.contextPath}/user/login" method="post">用户名:<input type="text" name="username" > <br/>密码 : <input type="text" name="password"> <br>请输入验证码: <input type="text" name="code"><img src="${pageContext.request.contextPath}/user/getImage" alt=""><br><input type="submit" value="登录"></form>
3.开发控制器
@RequestMapping("getImage")public void getImage(HttpSession session, HttpServletResponse response) throws IOException {//生成验证码String code = VerifyCodeUtils.generateVerifyCode(4);//验证码放入sessionsession.setAttribute("code",code);//验证码存入图片ServletOutputStream os = response.getOutputStream();response.setContentType("image/png");VerifyCodeUtils.outputImage(220,60,os,code);}
4.放行验证码
map.put("/user/getImage","anon");//验证码

5.修改认证流程
@RequestMapping("login")public String login(String username, String password,String code,HttpSession session) {//比较验证码String codes = (String) session.getAttribute("code");try {if (codes.equalsIgnoreCase(code)){//获取主体对象Subject subject = SecurityUtils.getSubject();subject.login(new UsernamePasswordToken(username, password));return "redirect:/index.jsp";}else{throw new RuntimeException("验证码错误!");}} catch (UnknownAccountException e) {e.printStackTrace();System.out.println("用户名错误!");} catch (IncorrectCredentialsException e) {e.printStackTrace();System.out.println("密码错误!");}catch (Exception e){e.printStackTrace();System.out.println(e.getMessage());}return "redirect:/login.jsp";}
6.修改salt不能序列化的问题
//自定义salt实现 实现序列化接口public class MyByteSource implements ByteSource,Serializable {private byte[] bytes;private String cachedHex;private String cachedBase64;//加入无参数构造方法实现序列化和反序列化public MyByteSource(){}public MyByteSource(byte[] bytes) {this.bytes = bytes;}public MyByteSource(char[] chars) {this.bytes = CodecSupport.toBytes(chars);}public MyByteSource(String string) {this.bytes = CodecSupport.toBytes(string);}public MyByteSource(ByteSource source) {this.bytes = source.getBytes();}public MyByteSource(File file) {this.bytes = (new MyByteSource.BytesHelper()).getBytes(file);}public MyByteSource(InputStream stream) {this.bytes = (new MyByteSource.BytesHelper()).getBytes(stream);}public static boolean isCompatible(Object o) {return o instanceof byte[] || o instanceof char[] || o instanceof String || o instanceof ByteSource || o instanceof File || o instanceof InputStream;}public byte[] getBytes() {return this.bytes;}public boolean isEmpty() {return this.bytes == null || this.bytes.length == 0;}public String toHex() {if (this.cachedHex == null) {this.cachedHex = Hex.encodeToString(this.getBytes());}return this.cachedHex;}public String toBase64() {if (this.cachedBase64 == null) {this.cachedBase64 = Base64.encodeToString(this.getBytes());}return this.cachedBase64;}public String toString() {return this.toBase64();}public int hashCode() {return this.bytes != null && this.bytes.length != 0 ? Arrays.hashCode(this.bytes) : 0;}public boolean equals(Object o) {if (o == this) {return true;} else if (o instanceof ByteSource) {ByteSource bs = (ByteSource)o;return Arrays.equals(this.getBytes(), bs.getBytes());} else {return false;}}private static final class BytesHelper extends CodecSupport {private BytesHelper() {}public byte[] getBytes(File file) {return this.toBytes(file);}public byte[] getBytes(InputStream stream) {return this.toBytes(stream);}}}
7.启动测试
6.9.5 JSP中Shiro常用标签
此模块参考:https://www.cnblogs.com/fancongcong/p/8093258.html
<shiro:guest>游客访问 <a href = "login.jsp"></a></shiro:guest>user 标签:用户已经通过认证\记住我 登录后显示响应的内容<shiro:user>欢迎[<shiro:principal/>]登录 <a href = "logout">退出</a></shiro:user>authenticated标签:用户身份验证通过,即 Subjec.login 登录成功 不是记住我登录的<shiro:authenticted>用户[<shiro:principal/>] 已身份验证通过</shiro:authenticted>notAuthenticated标签:用户未进行身份验证,即没有调用Subject.login进行登录,包括"记住我"也属于未进行身份验证<shiro:notAuthenticated>未身份验证(包括"记住我")</shiro:notAuthenticated>principal 标签:显示用户身份信息,默认调用Subjec.getPrincipal()获取,即Primary Principal<shiro:principal property = "username"/>hasRole标签:如果当前Subject有角色将显示body体内的内容<shiro:hashRole name = "admin">用户[<shiro:principal/>]拥有角色admin</shiro:hashRole>hasAnyRoles标签:如果Subject有任意一个角色(或的关系)将显示body体里的内容<shiro:hasAnyRoles name = "admin,user">用户[<shiro:pricipal/>]拥有角色admin 或者 user</shiro:hasAnyRoles>lacksRole:如果当前 Subjec没有角色将显示body体内的内容<shiro:lacksRole name = "admin">用户[<shiro:pricipal/>]没有角色admin</shiro:lacksRole>hashPermission:如果当前Subject有权限将显示body体内容<shiro:hashPermission name = "user:create">用户[<shiro:pricipal/>] 拥有权限user:create</shiro:hashPermission>lacksPermission:如果当前Subject没有权限将显示body体内容<shiro:lacksPermission name = "org:create">用户[<shiro:pricipal/>] 没有权限org:create</shiro:lacksPermission>