- free_flag.zip">free_flagfree_flag.zip
- crackme.zip">crackme crackme.zip
- ck.zip">ckck.zip
- maze.zip">mazemaze.zip
- ALL_IN_ALL.zip">ALL_IN_ALLALL_IN_ALL.zip
- rand.zip">randrand.zip
- DEX.zip">DEXDEX.zip
- motion.zip">motionmotion.zip
- keygen.zip">keygenkeygen.zip
free_flagfree_flag.zip
签到题,异或一下得flag
enflag = [0x78, 0x64, 0x3F, 0x53, 0x6D, 0x79, 0x78, 0x64, 0x62, 0x3F,0x78, 0x3D, 0x6F, 0x38, 0x3D, 0x78, 0x3C, 0x62, 0x53, 0x39,0x75, 0x39, 0x78, 0x3F, 0x61, 0x53, 0x3D, 0x39, 0x53, 0x62,0x3C, 0x78, 0x53, 0x3C, 0x39, 0x53, 0x39, 0x3F, 0x6F, 0x79,0x7E, 0x3F, 0x0A]cipher = 0xCfor s in enflag:print(chr(s^cipher),end='')
crackme crackme.zip
upx脱壳。用户名填入crackme,在判断位置断点,并让程序防止跳转,每次断点查看v17变量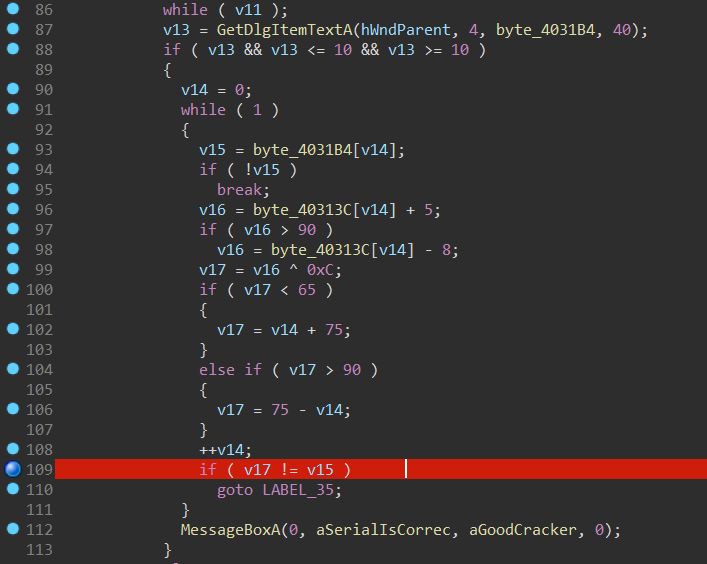
flag = [0x58,0x42,0x49,0x48,0x44,0x43,0x45,0x43,0x53,0x42]for i in flag:print(chr(i),end='')
md5 32位小写
ckck.zip
题目说猜猜是什么加密算法,F5后已经可以盲猜一波base64换表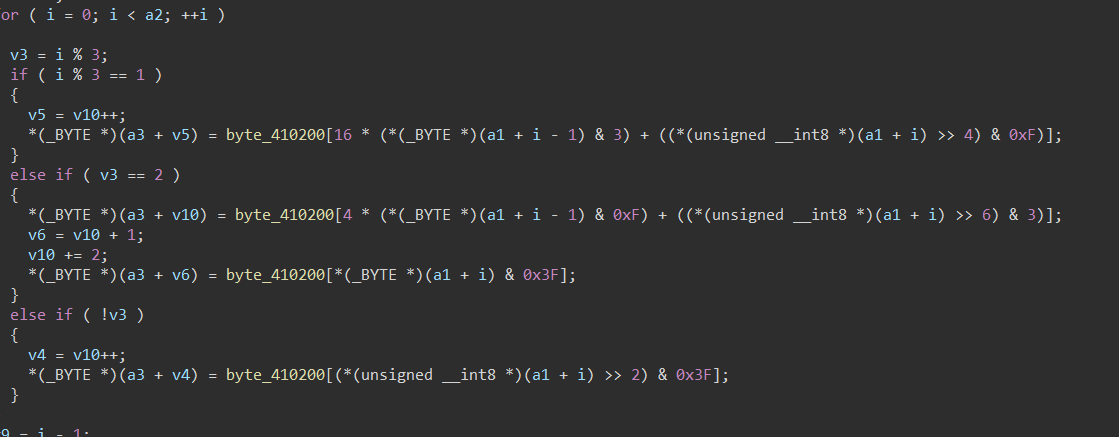
import base64my_base64table = ",.0fgWV#`/1Heox$~\"2dity%_;j3csz^+@{4bKrA&=}5laqB*-[69mpC()]78ndu"std_base64table ="ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/"s = "ef\"^sVK@3r@Ke4e6%6`)"s = s.translate(str.maketrans(my_base64table,std_base64table))print(base64.b64decode(s))#04_tianhe233_29
mazemaze.zip
迷宫题,ssddwdwdddssaasasaaassddddwdds
即flag{545d406061561f34247732d50c56ef0d}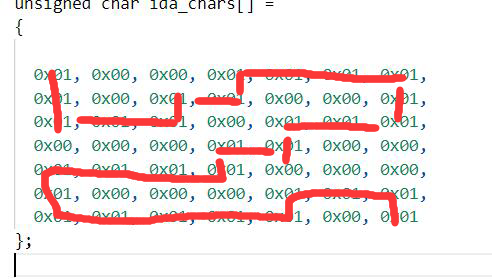
ALL_IN_ALLALL_IN_ALL.zip
用frida-dexdump把壳脱掉,再用jeb打开dex,发现校验函数是checkSN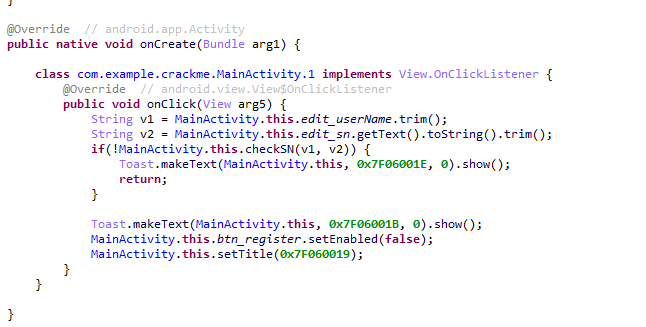
因为没jeb付费版本…无奈只能用jadx,发现就是判断输入就是userName和md5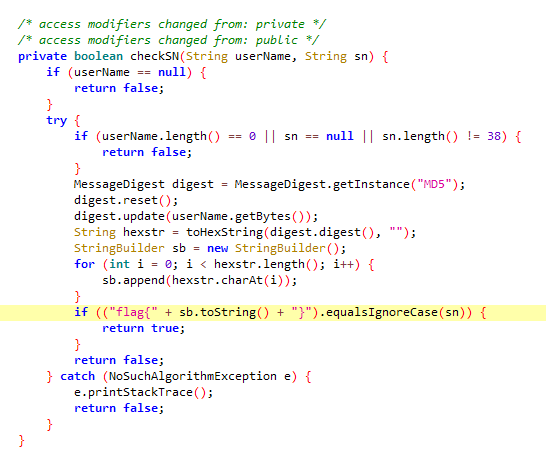
通过用反射大师找到userName为HuMen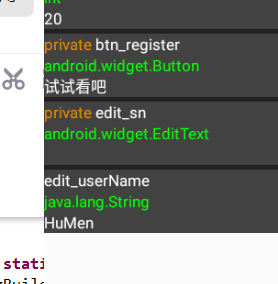
得到flag为flag{749fef1ed34917cc23376494813053b2}
randrand.zip
有空再补
DEXDEX.zip
参考这篇文章学习dex格式https://www.cnblogs.com/dengkaiting/p/11069351.html,用jeb等软件打不开这个dex文件。用010editor进行分析,打开后有模板可以直接用,注意到有四个零值,前两个零值是正常的,但后面两个需要输入method和class的offset(偏移),题目将这里修改为0了所以软件打不开。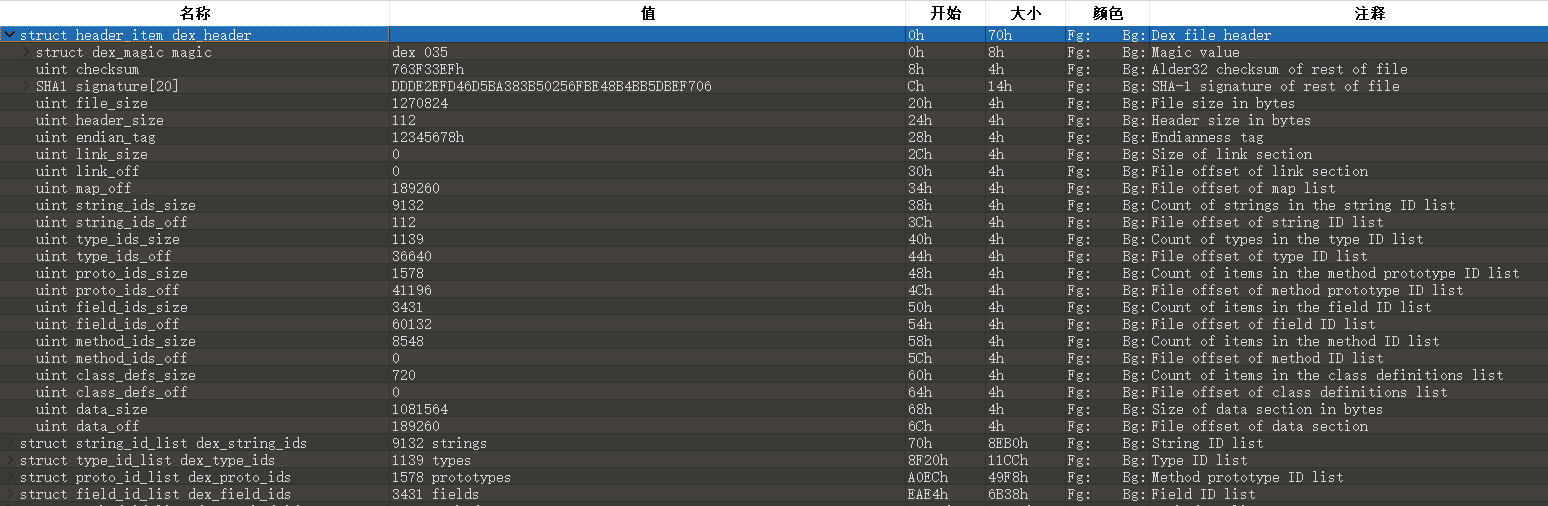
010editor已经将method和class的存储位置帮你找到了,在模板那里点一下即可跳转,如下图的method偏移为1561C,然后修改dex header的偏移即可(注意这里是小端序,若不知道是小端序还是大端序的话建议转10进制后直接在010的模板里修改)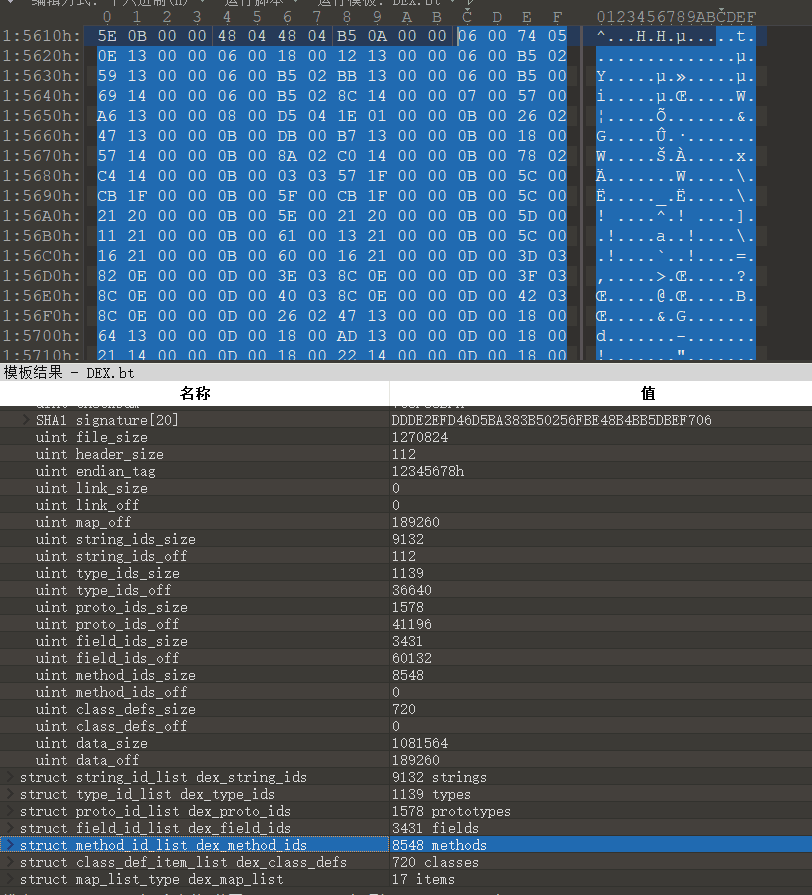
用jeb打开dex进行分析,可见直接运行一次出flag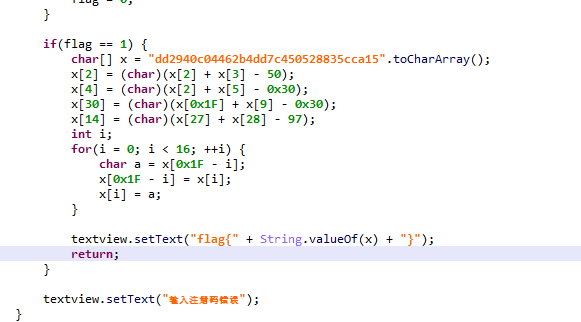
public class HelloWorld {public static void main(String []args) {char[] x = "dd2940c04462b4dd7c450528835cca15".toCharArray();x[2] = (char)(x[2] + x[3] - 50);x[4] = (char)(x[2] + x[5] - 0x30);x[30] = (char)(x[0x1F] + x[9] - 0x30);x[14] = (char)(x[27] + x[28] - 97);int i;for(i = 0; i < 16; ++i) {char a = x[0x1F - i];x[0x1F - i] = x[i];x[i] = a;}System.out.println("flag{" + String.valueOf(x) + "}");}}
flag{59acc538825054c7de4b26440c0999dd}
motionmotion.zip
同上
keygenkeygen.zip
同上

