文中内容来自:Digging into Linux namespaces - part 1: https://blog.quarkslab.com/digging-into-linux-namespaces-part-1.html
In the current stable Linux Kernel version 5.7 there are seven different namespaces:
- PID namespace: isolation of the system process tree;
- NET namespace: isolation of the host network stack;
- MNT namespace: isolation of host filesystem mount points;
- UTS namespace: isolation of hostname;
- IPC namespace: isolation for interprocess communication utilities (shared segments, semaphores);
- USER namespace: isolation of system users IDs;
- CGROUP namespace: isolation of the virtual cgroup filesystem of the host.
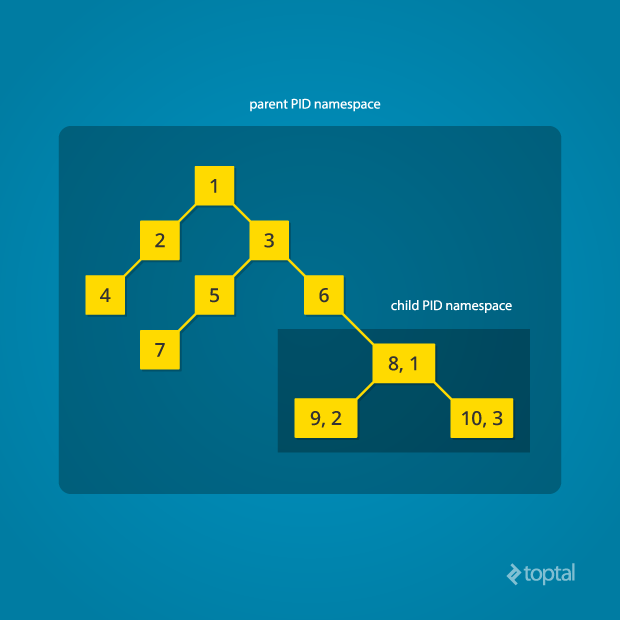
PID namespace
- Processes within a namespace only see (interact with) the processes in the same PID namespace (isolation);
- Each PID namespace has its own numbering starting at 1 (relative);
- This numbering is unique per process namespace - If PID 1 goes away then the whole namespace is deleted;
- Namespaces can be nested;
- A process ends up having multiple PIDs (when namespaces are nested);
- All ‘ps’-like commands use the virtual procfs file system mount to deliver their functionalities.
NET namespace
- Processes within a given network namespace get their own private network stack, including network interfaces, routing tables, iptables rules, sockets (ss, netstat);
- The connection between network namespaces can be done using two virtual interfaces;
- Communication between isolated network stacks in the same namespace is done using a bridge;
- The NET namespace can be used to simulate a “box” of Linux processes where only a few of them would be able to reach the outside world (by removing the host’s default gateway from the routing rules of some NET namespaces).


