https://casbin.org/docs/zh-CN/tutorials
Model
在 Casbin 中, 访问控制模型被抽象为基于 PERM (Policy, Effect, Request, Matcher) 的一个文件。
PERM模式由四个基础(策略、效果、请求、匹配)组成,描述了资源与用户之间的关系。
# Request definition[request_definition]r = sub, obj, act# Policy definition[policy_definition]p = sub, obj, act# Policy effect[policy_effect]e = some(where (p.eft == allow))# Matchers[matchers]m = r.sub == p.sub && r.obj == p.obj && r.act == p.act
Request
定义请求参数。要求至少有一个主题(subject 访问实体),对象(object 访问资源),动作(action 访问方法)
例如r = {sub, obj, act}
Policy
定义访问策略的模型。实际上,它定义了Policy规则文档中字段的名称和顺序。
例如p = {sub, obj, act}或者p = {sub, obj, act, eft}
Matcher
request和policy的匹配关系
例如 m = r.sub == p.sub && r.obj == p.obj && r.act == p.act
Effect
对匹配结果的再次逻辑组合判断
例如e = some(where(p.eft == allow))
RBAC
[role_definition]g = _, _g2 = _, _
[role_definition]是为RBAC角色继承关系的定义。users和resources可以有角色和他们的继承关系。
casbin在policy中存储着实际的 用户-角色(或资源-角色),例如
p, data2_admin, data2, readg, alice, data2_admin//表示alice是data2_admin角色的一个成员//alice可以是一个用户、资源或者是权限
在matcher中,你应该检查这个权限
[matchers]m = g(r.sub, p.sub) && r.obj == p.obj && r.act == p.act
If A has role B, B has role C, then A has role C.
use pattern matching in RBAC
p, alice, book_group, readg, /book/1, book_groupg, /book/2, book_group
g, /book/:id, book_group
p, admin, domain1, data1, readp, admin, domain1, data1, writep, admin, domain2, data2, readp, admin, domain2, data2, writeg, alice, admin, *g, bob, admin, domain2
In this example, we want alice to read and write data in domain1 and domain2, pattern matching* in gmakes alice have the access to two domains.
Role definition with domains tenants
[role_definition]g = _, _, _
p, admin, tenant1, data1, readp, admin, tenant2, data2, readg, alice, admin, tenant1g, alice, user, tenant2
[matchers]m = g(r.sub, p.sub, r.dom) && r.dom == p.dom && r.obj == p.obj && r.act == p.act
It means admin role in tenant1 can read data1. And alice has admin role in tenant1, and has user role in tenant2. So she can read data1. However, since alice is not an admin in tenant2, she cannot read data2.
ABAC
ABAC is Attribute-Based Access Control
type testResource struct {Name stringOwner string}
[request_definition]r = sub, obj, act[policy_definition]p = sub, obj, act[policy_effect]e = some(where (p.eft == allow))[matchers]m = r.sub == r.obj.Owner
We use r.obj.Owner instead of r.obj in the matcher. The r.obj passed in the Enforce() function will be a struct or class instance instead of string.我们在匹配器中使用r.obj.owner而不是r.obj。在Enforce()函数中传递的r.obj将是一个结构或类实例,而不是字符串。
Super Admin
[request_definition]r = sub, obj, act[policy_definition]p = sub, obj, act[policy_effect]e = some(where (p.eft == allow))[matchers]m = r.sub == p.sub && r.obj == p.obj && r.act == p.act || r.sub == "root"
Model存储
从.conf文件中加载
e := casbin.NewEnforcer("examples/rbac_model.conf", "examples/rbac_policy.csv")
从代码加载
import ("github.com/casbin/casbin/v2""github.com/casbin/casbin/v2/model""github.com/casbin/casbin/v2/persist/file-adapter")// 从Go代码初始化模型m := model.NewModel()m.AddDef("r", "r", "sub, obj, act")m.AddDef("p", "p", "sub, obj, act")m.AddDef("g", "g", "_, _")m.AddDef("e", "e", "some(where (p.eft == allow))")m.AddDef("m", "m", "g(r.sub, p.sub) && r.obj == p.obj && r.act == p.act")// 从CSV文件adapter加载策略规则// 使用自己的 adapter 替换。a := fileadapter.NewAdapter("examples/rbac_policy.csv")// 创建enforcere := casbin.NewEnforcer(m, a)
从字符串中加载
import ("github.com/casbin/casbin/v2""github.com/casbin/casbin/v2/model")// 从字符串初始化模型text :=`[request_definition]r = sub, obj, act[policy_definition]p = sub, obj, act[role_definition]g = _, _[policy_effect]e = some(where (p.eft == allow))[matchers]m = g(r.sub, p.sub) && r.obj == p.obj && r.act == p.act`m, _ := model.NewModelFromString(text)// 从CSV文件adapter加载策略规则// 使用自己的 adapter 替换a := fileadapter.NewAdapter("示例/rbac_policy.csv")// 创建执行者。e := casbin.NewEnforcer(m, a)
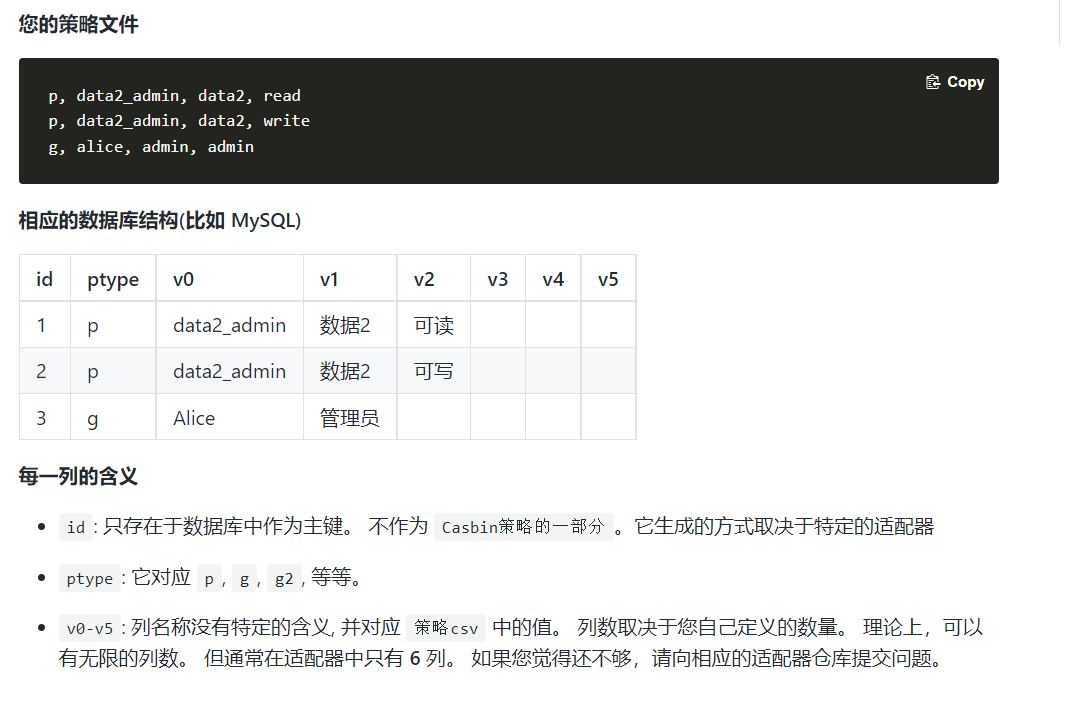
Policy存储
从csv文件和数据库载入两种方式
https://casbin.org/docs/zh-CN/policy-storage
p, alice, data1, readp, bob, data2, writep, data2_admin, data2, readp, data2_admin, data2, writeg, alice, data2_admin