- 摘要
- 1. 简介(Introduction )
- 2. 专业术语(Terminology)
- 3.用于数字签名和MAC的密码算法(Cryptographic Algorithms for Digital Signatures and MACs)
- 4.密钥管理的加密算法(Cryptographic Algorithms for Key Management)
- 5.用于内容加密的密码算法(Cryptographic Algorithms for Content Encryption)
- 6.密钥的加密算法(Cryptographic Algorithms for Keys)
- 7. IANA注意事项(IANA Considerations)
- 8.安全注意事项(Security Considerations)
- 9.国际化注意事项(Internationalization Considerations)
- 10. 参考(References)
RFC7518-JSON Web Algorithms (JWA)
摘要
1. 简介(Introduction )
2. 专业术语(Terminology)
3.用于数字签名和MAC的密码算法(Cryptographic Algorithms for Digital Signatures and MACs)
4.密钥管理的加密算法(Cryptographic Algorithms for Key Management)
4.1 JWE的“ alg”(算法)标头参数值(”alg” (Algorithm) Header Parameter Values for JWE)
下表是由本规范定义的用于JWE的“ alg”(算法)标头参数值的集合。这些算法用于加密CEK,生成JWE加密密钥或使用密钥协议达成共识 CEK。
The table below is the set of “alg” (algorithm) Header Parameter values that are defined by this specification for use with JWE.These algorithms are used to encrypt the CEK, producing the JWE Encrypted Key, or to use key agreement to agree upon the CEK.
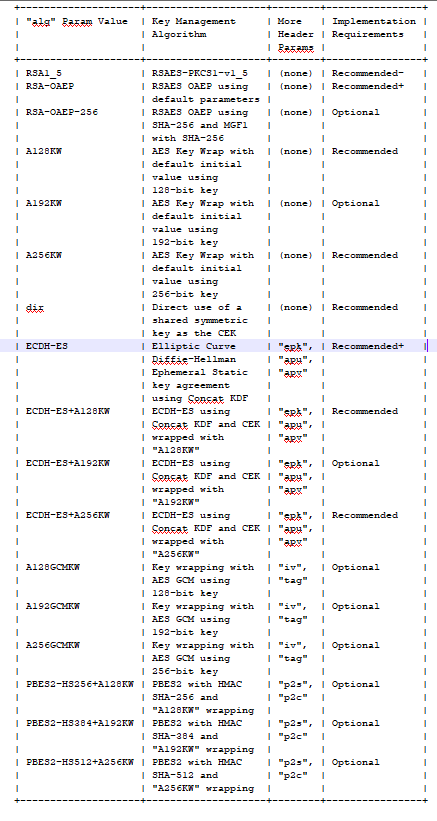
More Header Params列表示除了“alg”之外,算法还使用了哪些额外的头参数,这些参数都使用了。除了“dir”和“ECDH-ES”之外,所有的密钥值都是JWE加密的。
在实现需求栏中使用“+”表示需求强度可能会在规范的未来版本中增加。使用“-”表示需求强度在未来的规范版本中可能会降低。
在附录a .2中有一个对照表,它将本规范中定义的JWE“alg”(算法)值与其他标准和软件包中使用的等价标识符进行了交叉引用。
The More Header Params column indicates what additional Header Parameters are used by the algorithm, beyond “alg”, which all use. All but “dir” and “ECDH-ES” also produce a JWE Encrypted Key value.
The use of “+” in the Implementation Requirements column indicates that the requirement strength is likely to be increased in a future version of the specification. The use of “-“ indicates that the requirement strength is likely to be decreased in a future version of the specification.
See Appendix A.2 for a table cross-referencing the JWE “alg”(algorithm) values defined in this specification with the equivalent identifiers used by other standards and software packages.
4.2 Key Encryption with RSAES-PKCS1-v1_5
4.3. Key Encryption with RSAES OAEP
4.4. Key Wrapping with AES Key Wrap
4.5. Direct Encryption with a Shared Symmetric Key
4.6. Key Agreement with Elliptic Curve Diffie-Hellman Ephemeral Static (ECDH-ES)
5.用于内容加密的密码算法(Cryptographic Algorithms for Content Encryption)
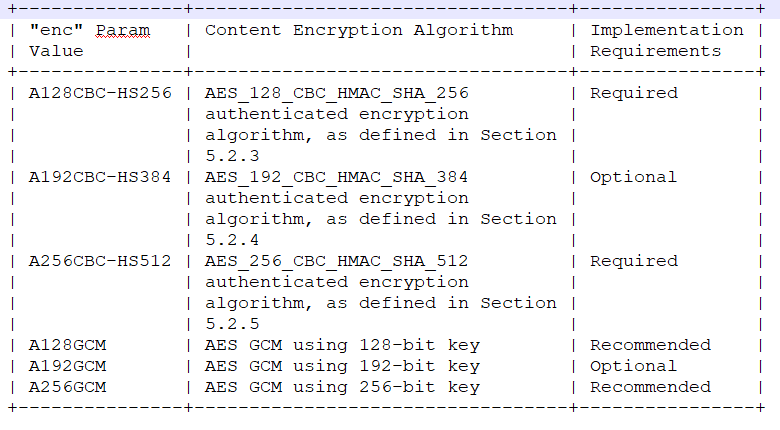
下表是此规范定义的用于JWE的“ enc”(加密算法)标头参数值的集合。
The table below is the set of “enc” (encryption algorithm) Header Parameter values that are defined by this specification for use with JWE.