PrepareedStatement 可以防止SQL注入
package com.kuang.lesson03;import com.kuang.lesson02.utils.JdbcUtils;import java.util.Date;import java.sql.*;public class TestInsert {public static void main(String[] args) throws SQLException {Connection conn = null;PreparedStatement st =null;try {conn= JdbcUtils.getConnection();//区别//使用?占位符代替参数String sql="insert into users(id,`NAME`,`PASSWORD`,`email`,`birthday`) values(?,?,?,?,?)";st=conn.prepareStatement(sql);//预编译,先写sql,然后不执行st.setInt(1,4);//idst.setString(2,"qiangjiang");//namest.setString(3,"123123");st.setString(4,"2233445");//注意点: sql.Date 数据库 java.sql.Date()// util.Date Java new Date().getTime 获得时间戳st.setDate(5,new java.sql.Date(new Date().getTime()));//执行int i = st.executeUpdate();if(i>0){System.out.println("插入成功");}} catch (SQLException e) {e.printStackTrace();}finally {JdbcUtils.release(conn,st,null);}}}
其他的类似,只需要改sql语句和手动给参即可。
删除类似: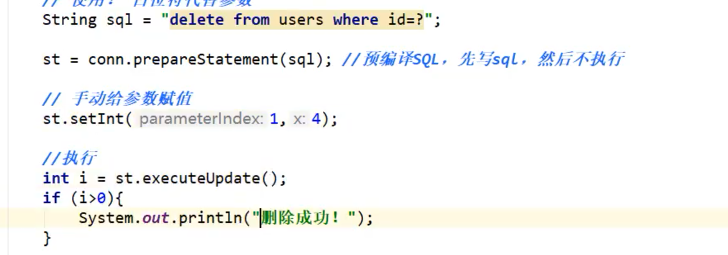
更新: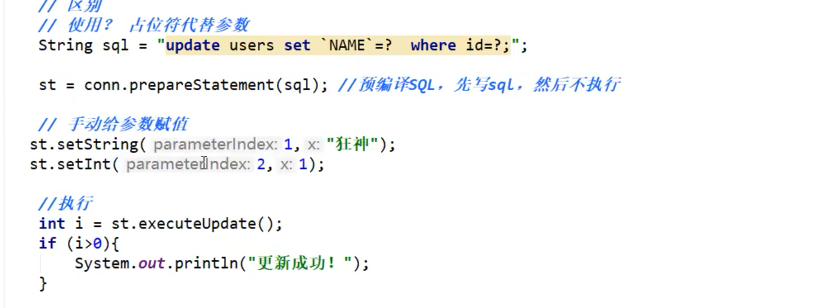
查询:
package com.kuang.lesson03;import com.kuang.lesson02.utils.JdbcUtils;import javax.annotation.Resource;import java.sql.Connection;import java.sql.PreparedStatement;import java.sql.ResultSet;import java.sql.SQLException;public class TestSelect {public static void main(String[] args) throws SQLException {Connection conn=null;PreparedStatement st=null;ResultSet rs=null;try {conn=JdbcUtils.getConnection();String sql="select * from users where id = ?";st=conn.prepareStatement(sql);st.setInt(1,1);rs=st.executeQuery();if(rs.next()){System.out.println(rs.getString("NAME"));}} catch (SQLException e) {e.printStackTrace();}finally {JdbcUtils.release(conn,st,rs);}}}
如何解决sql注入问题?
package com.kuang.lesson03;
import com.kuang.lesson02.utils.JdbcUtils;
import java.sql.*;
public class SqlInjection {
public static void main(String[] args) {
// login("zhansan","123456");
login("''or '1=1","123456");
}
public static void login(String username,String password){
Connection conn=null;
PreparedStatement st=null;
ResultSet rs=null;
try {
conn= JdbcUtils.getConnection();
//SELECT * FROM users WHERE `name` = 'zhansan' AND `password` = '123456';
String sql="SELECT * FROM users WHERE `NAME` = ? and `PASSWORD`=?";
st=conn.prepareStatement(sql);
st.setString(1,username);
st.setString(2,password);
rs=st.executeQuery();
while (rs.next()){
System.out.println(rs.getString("NAME"));
System.out.println(rs.getString("password"));
System.out.println("=====================================");
}
} catch (SQLException e) {
e.printStackTrace();
}finally {
try {
JdbcUtils.release(conn,st,rs);
} catch (SQLException e) {
e.printStackTrace();
}
}
}
}
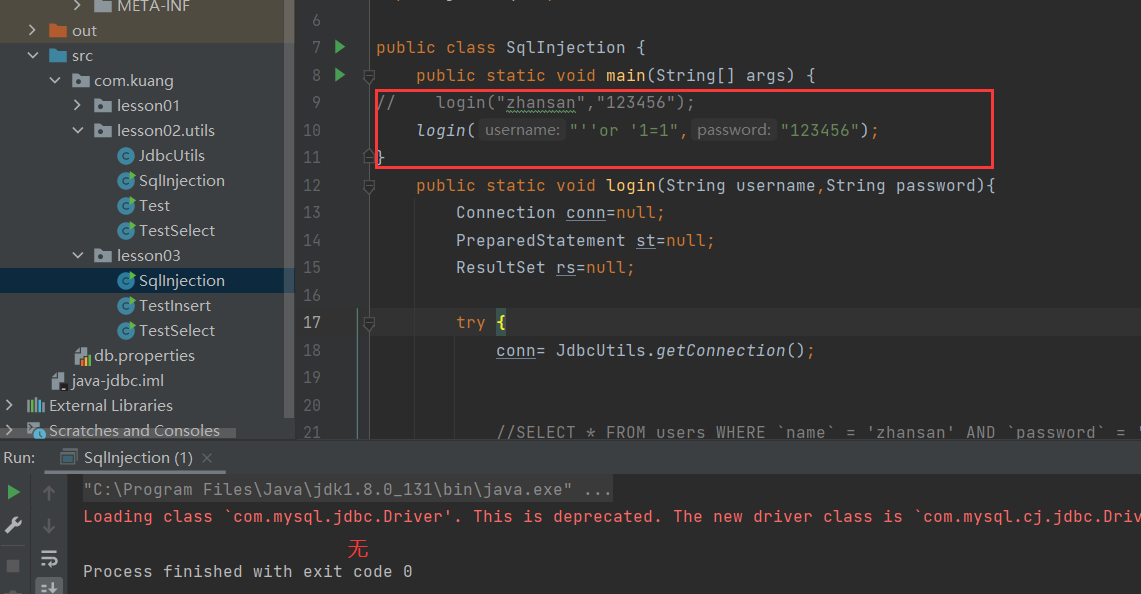
Preparedstatement 防止SQL注入的本质,把传递进来的参数当做字符
假设其中存在转义字符,比如说 ` 会被直按转义

