应急响应补充知识点
挖矿靶机分析PDF外加其他
Python开发相关知识点
1.开发基础环境配置说明
Windows10 + Pycharm
2.Python开发学习的意义
- 学习相关安全工具原理
- 掌握自定义工具及拓展开发
- 解决实战中无工具或手动麻烦批量化等情况
- 在二次开发Bypass,日常任务,批量测试利用等方面均有帮助
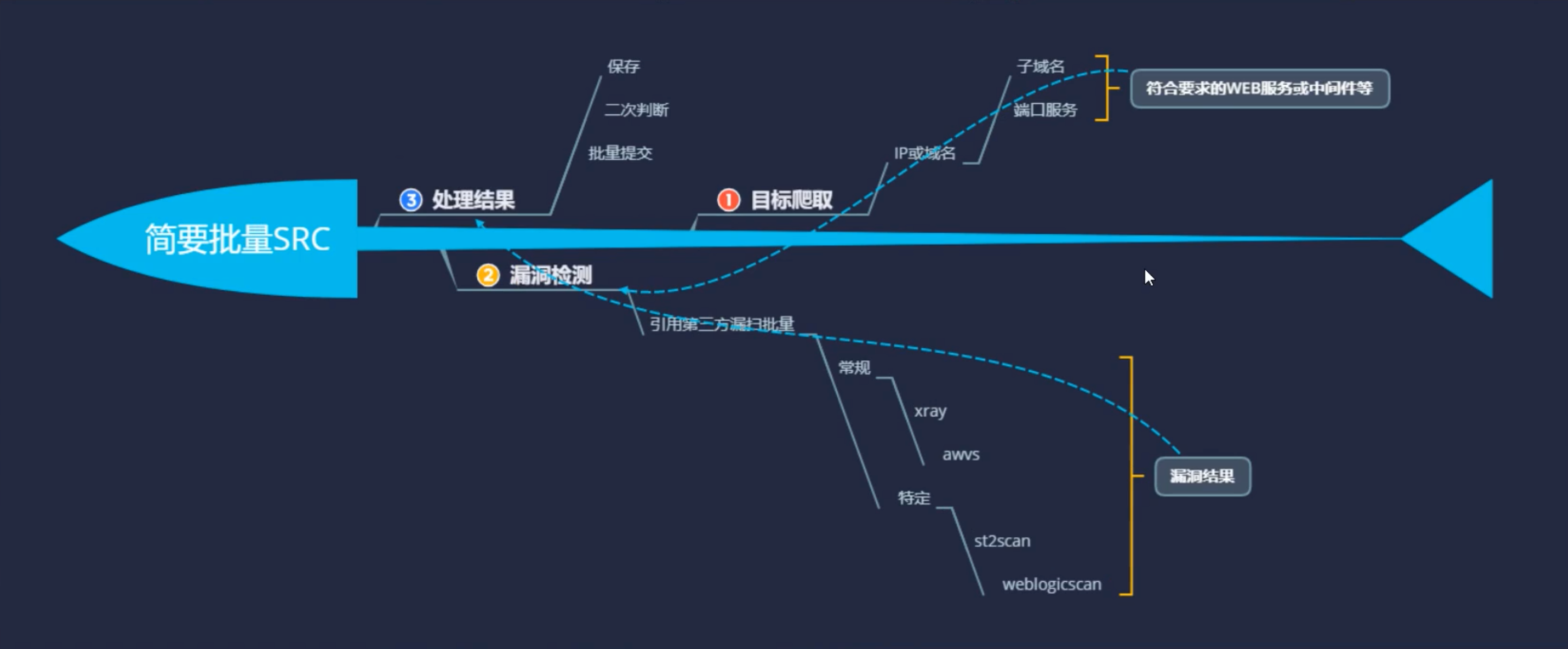
- 利用场景:SRC批量收集和利用,AWD批量利用获取FLAG,CTF加解密脚本等
3.本篇直播涉及的技术方向
Socket,爬虫,正则表达式,框架方向
4.本次直播涉及知识点
Socket部分技术,进程命令执行,交互参数执行,Nmap工具模块使用,异常处理等
# -*- codeing = utf-8 -*-# @Time : 2021/5/25 11:16 上午# @Author : GLSakura# @File : 76test.py# @Software : PyCharmimport osimport socket# pip install python-whoisfrom whois import whoisimport time# import sysimport nmap# ip查询-socketdef ip_check(url):ip = socket.gethostbyname(url)print(ip)# CDN判断-利用返回IP条数进行判断def cdn_check(url):ns = "nslookup " + url# data=os.system(ns)# print(data)# 结果无法读取操作data = os.popen(ns, "r").read()if data.count(".") > 15:print("存在CDN")else:print(data)print("不存在CDN")# 端口扫描# 1.原生自写socket协议tcp,udp扫描# 2.调用第三方模块等扫描# 3.调用系统工具脚本执行def port_check(url):ports = {'21', '22', '80'}server = socket.socket(socket.AF_INET, socket.SOCK_STREAM)for port in ports:ip = socket.gethostbyname(url)result = server.connect_ex((ip, int(port)))if result == 0:print(port + '\topen')else:print(port + '\tclose')# whois查询def whois_check(url):data = whois(url)print(data)# 子域名查询def domain_check(url):url = url.replace('www.', '')for domain_data in open("/Users/glan/Sec/Dicts/fuzzDicts/subdomainDicts/main.txt"):domain_data = domain_data.replace('\n', '')domain_url = domain_data + '.' + urltry:ip = socket.gethostbyname(domain_url)print(domain_url + '\t\t->\t' + ip)time.sleep(0.1)except Exception as e:pass# nmap扫描def nmap_check(url):nm = nmap.PortScanner()ret = nm.scan(hosts=url, ports='22')print(ret)if __name__ == '__main__':url = 'www.baidu.com'ip_check(url)cdn_check(url)nmap_check(url)whois(url)domain_check(url)