https://github.com/goharbor/harbor-helm
https://github.com/kubesphere/helm-charts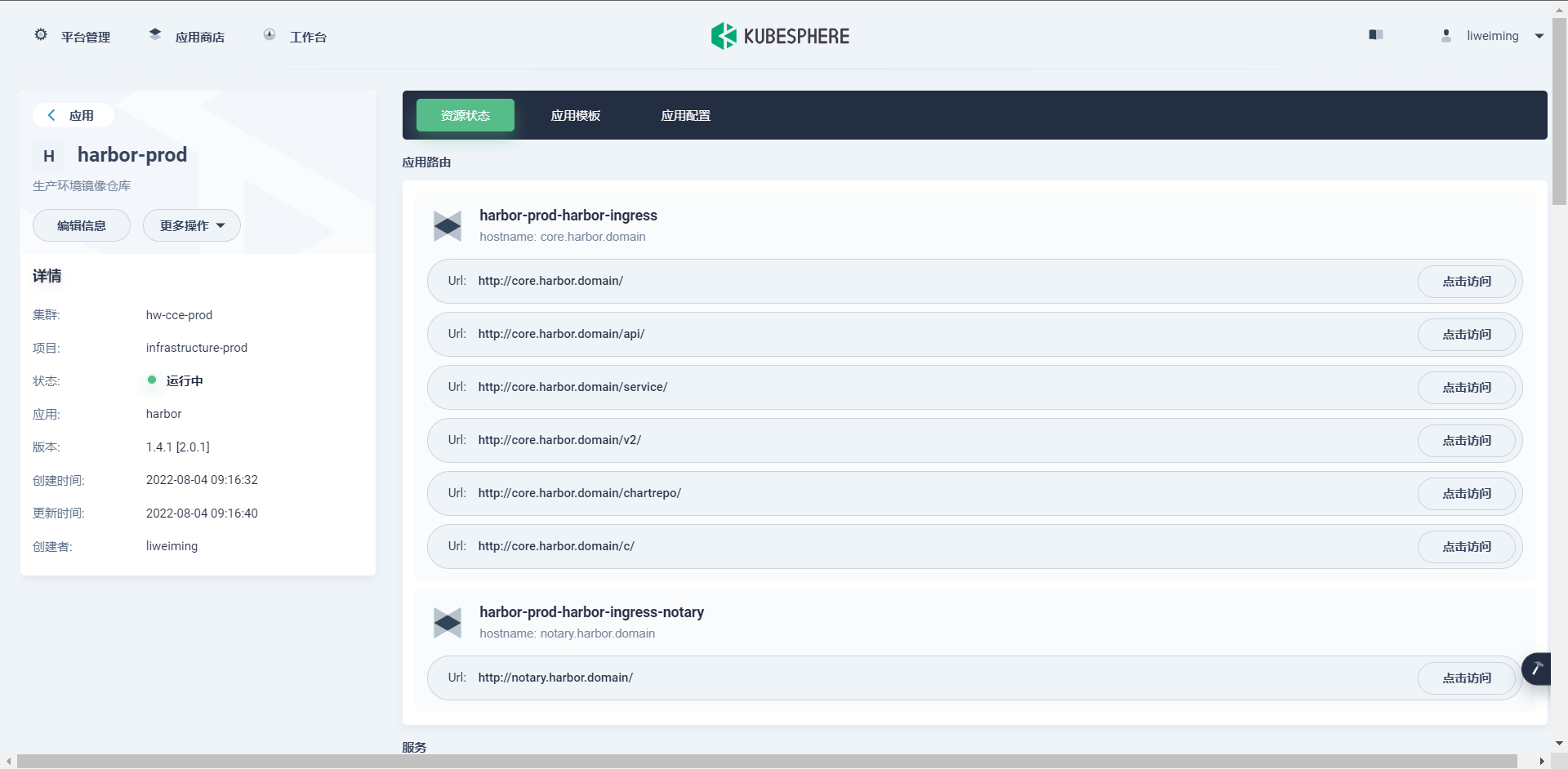
expose:# 配置服务暴露方式:ingress、clusterIP或nodePort多种类型type: ingress# 是否开启 tlstls:# 注:如果服务暴露方式是 ingress 并且tls被禁用,则在pull/push镜像时,则必须包含端口。详细查看文档:https://github.com/goharbor/harbor/issues/5291enabled: truecertSource: autoauto:# common name 是用于生成证书的,当类型是 clusterIP 或者 nodePort 并且 secretName 为空的时候才需要commonName: ""secret:# 如果你想使用自己的 TLS 证书和私钥,请填写这个 secret 的名称,这个 secret 必须包含名为 tls.crt 和 tls.key 的证书和私钥文件,如果没有设置则会自动生成证书和私钥文件secretName: ""# 默认 Notary 服务会使用上面相同的证书和私钥文件,如果你想用一个独立的则填充下面的字段,注意只有类型是 ingress 的时候才需要notarySecretName: ""ingress:hosts:core: core.harbor.domainnotary: notary.harbor.domaincontroller: defaultannotations:ingress.kubernetes.io/ssl-redirect: "true"ingress.kubernetes.io/proxy-body-size: "0"nginx.ingress.kubernetes.io/ssl-redirect: "true"nginx.ingress.kubernetes.io/proxy-body-size: "0"notary:annotations: {}harbor:annotations: {}# ClusterIP 的服务名称clusterIP:name: harborannotations: {}ports:httpPort: 80httpsPort: 443# Notary 服务监听端口,只有当 notary.enabled 设置为 true 的时候有效notaryPort: 4443# nodePort 的服务名称nodePort:name: harborports:http:port: 80nodePort: 30002https:port: 443nodePort: 30003notary:port: 4443nodePort: 30004# loadBalancer 的服务名称loadBalancer:name: harbor# 如果LoadBalancer支持IP分配,则需要配置IPIP: ""ports:httpPort: 80httpsPort: 443notaryPort: 4443annotations: {}sourceRanges: []# Harbor 核心服务外部访问 URL;主要用于:# 1) 补全 portal 页面上面显示的 docker/helm 命令# 2) 补全返回给 docker/notary 客户端的 token 服务 URL# 格式:protocol://domain[:port]。# 1) 如果 expose.type=ingress,"domain"的值就是 expose.ingress.hosts.core 的值# 2) 如果 expose.type=clusterIP,"domain"的值就是 expose.clusterIP.name 的值# 3) 如果 expose.type=nodePort,"domain"的值就是 k8s 节点的 IP 地址# 如果在代理后面部署 Harbor,请将其设置为代理的 URLexternalURL: https://core.harbor.domaininternalTLS:enabled: falsecertSource: "auto"trustCa: ""core:secretName: ""crt: ""key: ""jobservice:secretName: ""crt: ""key: ""registry:secretName: ""crt: ""key: ""portal:secretName: ""crt: ""key: ""chartmuseum:secretName: ""crt: ""key: ""# trivy镜像扫描证书相关的配置trivy:secretName: ""crt: ""key: ""# 默认情况下开启数据持久化,在k8s集群中需要动态的挂载卷默认需要一个StorageClass对象# 如果你有已经存在可以使用的持久卷,需要在"storageClass"中指定你的 storageClass 或者设置 "existingClaim"# 对于存储 docker 镜像和 Helm charts 包,你也可以用 "azure"、"gcs"、"s3"、"swift" 或者 "oss",直接在 "imageChartStorage" 区域设置即可persistence:enabled: true# 设置成"keep"避免在执行 helm 删除操作期间移除 PVC,留空则在 chart 被删除后删除 PVCresourcePolicy: "keep"persistentVolumeClaim:registry:existingClaim: ""# 指定"storageClass",或者使用默认的 StorageClass 对象,设置成"-"禁用动态分配挂载卷storageClass: ""subPath: ""accessMode: ReadWriteOncesize: 5Gichartmuseum:existingClaim: ""storageClass: ""subPath: ""accessMode: ReadWriteOncesize: 5Gijobservice:existingClaim: ""storageClass: ""subPath: ""accessMode: ReadWriteOncesize: 1Gi# 如果使用外部的数据库服务,下面的设置将会被忽略database:existingClaim: ""storageClass: ""subPath: ""accessMode: ReadWriteOncesize: 1Gi# 如果使用外部的 Redis 服务,下面的设置将会被忽略redis:existingClaim: ""storageClass: ""subPath: ""accessMode: ReadWriteOncesize: 1Gitrivy:existingClaim: ""storageClass: ""subPath: ""accessMode: ReadWriteOncesize: 5Gi# 定义使用什么存储后端来存储镜像和 charts 包,详细文档地址:https://github.com/docker/distribution/blob/master/docs/configuration.md#storageimageChartStorage:# 正对镜像和chart存储是否禁用跳转,对于一些不支持的后端(例如对于使用minio的`s3`存储),需要禁用它。为了禁止跳转,只需要设置`disableredirect=true`即可,详细文档地址:https://github.com/docker/distribution/blob/master/docs/configuration.md#redirectdisableredirect: false# 指定存储类型:"filesystem", "azure", "gcs", "s3", "swift", "oss",在相应的区域填上对应的信息。# 如果你想使用 pv 则必须设置成"filesystem"类型type: filesystemfilesystem:rootdirectory: /storage#maxthreads: 100azure:accountname: accountnameaccountkey: base64encodedaccountkeycontainer: containername#realm: core.windows.netgcs:bucket: bucketname# The base64 encoded json file which contains the keyencodedkey: base64-encoded-json-key-file#rootdirectory: /gcs/object/name/prefix#chunksize: "5242880"s3:region: us-west-1bucket: bucketname#accesskey: awsaccesskey#secretkey: awssecretkey#regionendpoint: http://myobjects.local#encrypt: false#keyid: mykeyid#secure: true#skipverify: false#v4auth: true#chunksize: "5242880"#rootdirectory: /s3/object/name/prefix#storageclass: STANDARD#multipartcopychunksize: "33554432"#multipartcopymaxconcurrency: 100#multipartcopythresholdsize: "33554432"swift:authurl: https://storage.myprovider.com/v3/authusername: usernamepassword: passwordcontainer: containername#region: fr#tenant: tenantname#tenantid: tenantid#domain: domainname#domainid: domainid#trustid: trustid#insecureskipverify: false#chunksize: 5M#prefix:#secretkey: secretkey#accesskey: accesskey#authversion: 3#endpointtype: public#tempurlcontainerkey: false#tempurlmethods:oss:accesskeyid: accesskeyidaccesskeysecret: accesskeysecretregion: regionnamebucket: bucketname#endpoint: endpoint#internal: false#encrypt: false#secure: true#chunksize: 10M#rootdirectory: rootdirectoryimagePullPolicy: IfNotPresentimagePullSecrets:# - name: docker-registry-secret# - name: internal-registry-secret# The update strategy for deployments with persistent volumes(jobservice, registry# and chartmuseum): "RollingUpdate" or "Recreate"# Set it as "Recreate" when "RWM" for volumes isn't supportedupdateStrategy:type: RollingUpdatelogLevel: info# Harbor admin 初始密码,Harbor 启动后通过 Portal 修改该密码harborAdminPassword: "Harbor12345"caSecretName: ""# 用于加密的一个 secret key,必须是一个16位的字符串secretKey: "not-a-secure-key"proxy:httpProxy:httpsProxy:noProxy: 127.0.0.1,localhost,.local,.internalcomponents:- core- jobservice- trivy# If expose the service via "ingress", the Nginx will not be used# 如果你通过"ingress"保留服务,则下面的Nginx不会被使用nginx:image:repository: goharbor/nginx-photontag: devserviceAccountName: ""automountServiceAccountToken: falsereplicas: 1# resources:# requests:# memory: 256Mi# cpu: 100mnodeSelector: {}tolerations: []affinity: {}# 额外的 Deployment 的一些 annotationspodAnnotations: {}priorityClassName:portal:image:repository: goharbor/harbor-portaltag: devserviceAccountName: ""automountServiceAccountToken: falsereplicas: 1# resources:# requests:# memory: 256Mi# cpu: 100mnodeSelector: {}tolerations: []affinity: {}podAnnotations: {}priorityClassName:core:image:repository: goharbor/harbor-coretag: devserviceAccountName: ""automountServiceAccountToken: falsereplicas: 1startupProbe:enabled: trueinitialDelaySeconds: 10# resources:# requests:# memory: 256Mi# cpu: 100mnodeSelector: {}tolerations: []affinity: {}podAnnotations: {}secret: ""secretName: ""xsrfKey: ""priorityClassName:jobservice:image:repository: goharbor/harbor-jobservicetag: devreplicas: 1serviceAccountName: ""automountServiceAccountToken: falsemaxJobWorkers: 10# jobs 的日志收集器:"file", "database" or "stdout"jobLoggers:- file# - database# - stdout# resources:# requests:# memory: 256Mi# cpu: 100mnodeSelector: {}tolerations: []affinity: {}podAnnotations: {}secret: ""priorityClassName:registry:serviceAccountName: ""automountServiceAccountToken: falseregistry:image:repository: goharbor/registry-photontag: dev# resources:# requests:# memory: 256Mi# cpu: 100mcontroller:image:repository: goharbor/harbor-registryctltag: dev# resources:# requests:# memory: 256Mi# cpu: 100mreplicas: 1nodeSelector: {}tolerations: []affinity: {}podAnnotations: {}priorityClassName:secret: ""relativeurls: falsecredentials:username: "harbor_registry_user"password: "harbor_registry_password"# e.g. "htpasswd -nbBC10 $username $password"htpasswd: "harbor_registry_user:$2y$10$9L4Tc0DJbFFMB6RdSCunrOpTHdwhid4ktBJmLD00bYgqkkGOvll3m"middleware:enabled: falsetype: cloudFrontcloudFront:baseurl: example.cloudfront.netkeypairid: KEYPAIRIDduration: 3000sipfilteredby: noneprivateKeySecret: "my-secret"chartmuseum:enabled: trueserviceAccountName: ""automountServiceAccountToken: falseabsoluteUrl: falseimage:repository: goharbor/chartmuseum-photontag: devreplicas: 1# resources:# requests:# memory: 256Mi# cpu: 100mnodeSelector: {}tolerations: []affinity: {}podAnnotations: {}priorityClassName:trivy:enabled: trueimage:repository: goharbor/trivy-adapter-photontag: devserviceAccountName: ""automountServiceAccountToken: falsereplicas: 1debugMode: falsevulnType: "os,library"severity: "UNKNOWN,LOW,MEDIUM,HIGH,CRITICAL"ignoreUnfixed: falseinsecure: falsegitHubToken: ""skipUpdate: falseresources:requests:cpu: 200mmemory: 512Milimits:cpu: 1memory: 1GinodeSelector: {}tolerations: []affinity: {}podAnnotations: {}priorityClassName:notary:enabled: trueserver:serviceAccountName: ""automountServiceAccountToken: falseimage:repository: goharbor/notary-server-photontag: devreplicas: 1# resources:# requests:# memory: 256Mi# cpu: 100mnodeSelector: {}tolerations: []affinity: {}podAnnotations: {}priorityClassName:signer:serviceAccountName: ""automountServiceAccountToken: falseimage:repository: goharbor/notary-signer-photontag: devreplicas: 1# resources:# requests:# memory: 256Mi# cpu: 100mnodeSelector: {}tolerations: []affinity: {}podAnnotations: {}priorityClassName:secretName: ""database:# 如果使用外部的数据库,则设置 type=external,然后填写 external 区域的一些连接信息type: internalinternal:serviceAccountName: ""automountServiceAccountToken: falseimage:repository: goharbor/harbor-dbtag: dev# 内部的数据库的初始化超级用户的密码password: "changeit"shmSizeLimit: 512Mi# resources:# requests:# memory: 256Mi# cpu: 100mnodeSelector: {}tolerations: []affinity: {}priorityClassName:initContainer:migrator: {}# resources:# requests:# memory: 128Mi# cpu: 100mpermissions: {}# resources:# requests:# memory: 128Mi# cpu: 100mexternal:host: "192.168.0.1"port: "5432"username: "user"password: "password"coreDatabase: "registry"notaryServerDatabase: "notary_server"notarySignerDatabase: "notary_signer"sslmode: "disable"maxIdleConns: 100maxOpenConns: 900podAnnotations: {}redis:# 如果使用外部的 Redis 服务,设置 type=external,然后补充 external 部分的连接信息。type: internalinternal:serviceAccountName: ""automountServiceAccountToken: falseimage:repository: goharbor/redis-photontag: dev# resources:# requests:# memory: 256Mi# cpu: 100mnodeSelector: {}tolerations: []affinity: {}priorityClassName:external:addr: "192.168.0.2:6379"sentinelMasterSet: ""# coreDatabaseIndex 必须设置为0coreDatabaseIndex: "0"jobserviceDatabaseIndex: "1"registryDatabaseIndex: "2"chartmuseumDatabaseIndex: "3"trivyAdapterIndex: "5"password: ""podAnnotations: {}exporter:replicas: 1# resources:# requests:# memory: 256Mi# cpu: 100mpodAnnotations: {}serviceAccountName: ""automountServiceAccountToken: falseimage:repository: goharbor/harbor-exportertag: devnodeSelector: {}tolerations: []affinity: {}cacheDuration: 23cacheCleanInterval: 14400priorityClassName:metrics:enabled: falsecore:path: /metricsport: 8001registry:path: /metricsport: 8001jobservice:path: /metricsport: 8001exporter:path: /metricsport: 8001serviceMonitor:enabled: falseadditionalLabels: {}interval: ""metricRelabelings: []# - action: keep# regex: 'kube_(daemonset|deployment|pod|namespace|node|statefulset).+'# sourceLabels: [__name__]# Relabel configs to apply to samples before ingestion.relabelings: []# - sourceLabels: [__meta_kubernetes_pod_node_name]# separator: ;# regex: ^(.*)$# targetLabel: nodename# replacement: $1# action: replace
expose:# Set the way how to expose the service. Set the type as "ingress",# "clusterIP", "nodePort" or "loadBalancer" and fill the information# in the corresponding sectiontype: ingresstls:# Enable the tls or not. Note: if the type is "ingress" and the tls# is disabled, the port must be included in the command when pull/push# images. Refer to https://github.com/goharbor/harbor/issues/5291# for the detail.enabled: true# Fill the name of secret if you want to use your own TLS certificate.# The secret contains keys named:# "tls.crt" - the certificate (required)# "tls.key" - the private key (required)# "ca.crt" - the certificate of CA (optional), this enables the download# link on portal to download the certificate of CA# These files will be generated automatically if the "secretName" is not setsecretName: ""# By default, the Notary service will use the same cert and key as# described above. Fill the name of secret if you want to use a# separated one. Only needed when the type is "ingress".notarySecretName: ""# The common name used to generate the certificate, it's necessary# when the type isn't "ingress" and "secretName" is nullcommonName: ""ingress:hosts:core: core.harbor.domainnotary: notary.harbor.domain# set to the type of ingress controller if it has specific requirements.# leave as `default` for most ingress controllers.# set to `gce` if using the GCE ingress controller# set to `ncp` if using the NCP (NSX-T Container Plugin) ingress controllercontroller: defaultannotations:ingress.kubernetes.io/ssl-redirect: "true"ingress.kubernetes.io/proxy-body-size: "0"nginx.ingress.kubernetes.io/ssl-redirect: "true"nginx.ingress.kubernetes.io/proxy-body-size: "0"clusterIP:# The name of ClusterIP servicename: harborports:# The service port Harbor listens on when serving with HTTPhttpPort: 80# The service port Harbor listens on when serving with HTTPShttpsPort: 443# The service port Notary listens on. Only needed when notary.enabled# is set to truenotaryPort: 4443nodePort:# The name of NodePort servicename: harborports:http:# The service port Harbor listens on when serving with HTTPport: 80# The node port Harbor listens on when serving with HTTPnodePort: 30002https:# The service port Harbor listens on when serving with HTTPSport: 443# The node port Harbor listens on when serving with HTTPSnodePort: 30003# Only needed when notary.enabled is set to truenotary:# The service port Notary listens onport: 4443# The node port Notary listens onnodePort: 30004loadBalancer:# The name of LoadBalancer servicename: harbor# Set the IP if the LoadBalancer supports assigning IPIP: ""ports:# The service port Harbor listens on when serving with HTTPhttpPort: 80# The service port Harbor listens on when serving with HTTPShttpsPort: 443# The service port Notary listens on. Only needed when notary.enabled# is set to truenotaryPort: 4443annotations: {}sourceRanges: []# The external URL for Harbor core service. It is used to# 1) populate the docker/helm commands showed on portal# 2) populate the token service URL returned to docker/notary client## Format: protocol://domain[:port]. Usually:# 1) if "expose.type" is "ingress", the "domain" should be# the value of "expose.ingress.hosts.core"# 2) if "expose.type" is "clusterIP", the "domain" should be# the value of "expose.clusterIP.name"# 3) if "expose.type" is "nodePort", the "domain" should be# the IP address of k8s node## If Harbor is deployed behind the proxy, set it as the URL of proxyexternalURL: https://core.harbor.domain# The internal TLS used for harbor components secure communicating. In order to enable https# in each components tls cert files need to provided in advance.internalTLS:# If internal TLS enabledenabled: false# There are three ways to provide tls# 1) "auto" will generate cert automatically# 2) "manual" need provide cert file manually in following value# 3) "secret" internal certificates from secretcertSource: "auto"# The content of trust ca, only available when `certSource` is "manual"trustCa: ""# core related cert configurationcore:# secret name for core's tls certssecretName: ""# Content of core's TLS cert file, only available when `certSource` is "manual"crt: ""# Content of core's TLS key file, only available when `certSource` is "manual"key: ""# jobservice related cert configurationjobservice:# secret name for jobservice's tls certssecretName: ""# Content of jobservice's TLS key file, only available when `certSource` is "manual"crt: ""# Content of jobservice's TLS key file, only available when `certSource` is "manual"key: ""# registry related cert configurationregistry:# secret name for registry's tls certssecretName: ""# Content of registry's TLS key file, only available when `certSource` is "manual"crt: ""# Content of registry's TLS key file, only available when `certSource` is "manual"key: ""# portal related cert configurationportal:# secret name for portal's tls certssecretName: ""# Content of portal's TLS key file, only available when `certSource` is "manual"crt: ""# Content of portal's TLS key file, only available when `certSource` is "manual"key: ""# chartmuseum related cert configurationchartmuseum:# secret name for chartmuseum's tls certssecretName: ""# Content of chartmuseum's TLS key file, only available when `certSource` is "manual"crt: ""# Content of chartmuseum's TLS key file, only available when `certSource` is "manual"key: ""# clair related cert configurationclair:# secret name for clair's tls certssecretName: ""# Content of clair's TLS key file, only available when `certSource` is "manual"crt: ""# Content of clair's TLS key file, only available when `certSource` is "manual"key: ""# trivy related cert configurationtrivy:# secret name for trivy's tls certssecretName: ""# Content of trivy's TLS key file, only available when `certSource` is "manual"crt: ""# Content of trivy's TLS key file, only available when `certSource` is "manual"key: ""# The persistence is enabled by default and a default StorageClass# is needed in the k8s cluster to provision volumes dynamicly.# Specify another StorageClass in the "storageClass" or set "existingClaim"# if you have already existing persistent volumes to use## For storing images and charts, you can also use "azure", "gcs", "s3",# "swift" or "oss". Set it in the "imageChartStorage" sectionpersistence:enabled: true# Setting it to "keep" to avoid removing PVCs during a helm delete# operation. Leaving it empty will delete PVCs after the chart deletedresourcePolicy: "keep"persistentVolumeClaim:registry:# Use the existing PVC which must be created manually before bound,# and specify the "subPath" if the PVC is shared with other componentsexistingClaim: ""# Specify the "storageClass" used to provision the volume. Or the default# StorageClass will be used(the default).# Set it to "-" to disable dynamic provisioningstorageClass: ""subPath: ""accessMode: ReadWriteOncesize: 5Gichartmuseum:existingClaim: ""storageClass: ""subPath: ""accessMode: ReadWriteOncesize: 5Gijobservice:existingClaim: ""storageClass: ""subPath: ""accessMode: ReadWriteOncesize: 1Gi# If external database is used, the following settings for database will# be ignoreddatabase:existingClaim: ""storageClass: ""subPath: ""accessMode: ReadWriteOncesize: 1Gi# If external Redis is used, the following settings for Redis will# be ignoredredis:existingClaim: ""storageClass: ""subPath: ""accessMode: ReadWriteOncesize: 1Gitrivy:existingClaim: ""storageClass: ""subPath: ""accessMode: ReadWriteOncesize: 5Gi# Define which storage backend is used for registry and chartmuseum to store# images and charts. Refer to# https://github.com/docker/distribution/blob/master/docs/configuration.md#storage# for the detail.imageChartStorage:# Specify whether to disable `redirect` for images and chart storage, for# backends which not supported it (such as using minio for `s3` storage type), please disable# it. To disable redirects, simply set `disableredirect` to `true` instead.# Refer to# https://github.com/docker/distribution/blob/master/docs/configuration.md#redirect# for the detail.disableredirect: false# Specify the "caBundleSecretName" if the storage service uses a self-signed certificate.# The secret must contain keys named "ca.crt" which will be injected into the trust store# of registry's and chartmuseum's containers.# caBundleSecretName:# Specify the type of storage: "filesystem", "azure", "gcs", "s3", "swift",# "oss" and fill the information needed in the corresponding section. The type# must be "filesystem" if you want to use persistent volumes for registry# and chartmuseumtype: filesystemfilesystem:rootdirectory: /storage#maxthreads: 100azure:accountname: accountnameaccountkey: base64encodedaccountkeycontainer: containername#realm: core.windows.netgcs:bucket: bucketname# The base64 encoded json file which contains the keyencodedkey: base64-encoded-json-key-file#rootdirectory: /gcs/object/name/prefix#chunksize: "5242880"s3:region: us-west-1bucket: bucketname#accesskey: awsaccesskey#secretkey: awssecretkey#regionendpoint: http://myobjects.local#encrypt: false#keyid: mykeyid#secure: true#v4auth: true#chunksize: "5242880"#rootdirectory: /s3/object/name/prefix#storageclass: STANDARDswift:authurl: https://storage.myprovider.com/v3/authusername: usernamepassword: passwordcontainer: containername#region: fr#tenant: tenantname#tenantid: tenantid#domain: domainname#domainid: domainid#trustid: trustid#insecureskipverify: false#chunksize: 5M#prefix:#secretkey: secretkey#accesskey: accesskey#authversion: 3#endpointtype: public#tempurlcontainerkey: false#tempurlmethods:oss:accesskeyid: accesskeyidaccesskeysecret: accesskeysecretregion: regionnamebucket: bucketname#endpoint: endpoint#internal: false#encrypt: false#secure: true#chunksize: 10M#rootdirectory: rootdirectoryimagePullPolicy: IfNotPresent# Use this set to assign a list of default pullSecretsimagePullSecrets:# - name: docker-registry-secret# - name: internal-registry-secret# The update strategy for deployments with persistent volumes(jobservice, registry# and chartmuseum): "RollingUpdate" or "Recreate"# Set it as "Recreate" when "RWM" for volumes isn't supportedupdateStrategy:type: RollingUpdate# debug, info, warning, error or fatallogLevel: info# The initial password of Harbor admin. Change it from portal after launching HarborharborAdminPassword: "Harbor12345"# The secret key used for encryption. Must be a string of 16 chars.secretKey: "not-a-secure-key"# The proxy settings for updating clair vulnerabilities from the Internet and replicating# artifacts from/to the registries that cannot be reached directlyproxy:httpProxy:httpsProxy:noProxy: 127.0.0.1,localhost,.local,.internalcomponents:- core- jobservice- clair## UAA Authentication Options# If you're using UAA for authentication behind a self-signed# certificate you will need to provide the CA Cert.# Set uaaSecretName below to provide a pre-created secret that# contains a base64 encoded CA Certificate named `ca.crt`.# uaaSecretName:# If expose the service via "ingress", the Nginx will not be usednginx:image:repository: goharbor/nginx-photontag: v2.0.0replicas: 1# resources:# requests:# memory: 256Mi# cpu: 100mnodeSelector: {}tolerations: []affinity: {}## Additional deployment annotationspodAnnotations: {}portal:image:repository: goharbor/harbor-portaltag: v2.0.0replicas: 1# resources:# requests:# memory: 256Mi# cpu: 100mnodeSelector: {}tolerations: []affinity: {}## Additional deployment annotationspodAnnotations: {}core:image:repository: goharbor/harbor-coretag: v2.0.0replicas: 1## Liveness probe valueslivenessProbe:initialDelaySeconds: 300# resources:# requests:# memory: 256Mi# cpu: 100mnodeSelector: {}tolerations: []affinity: {}## Additional deployment annotationspodAnnotations: {}# Secret is used when core server communicates with other components.# If a secret key is not specified, Helm will generate one.# Must be a string of 16 chars.secret: ""# Fill the name of a kubernetes secret if you want to use your own# TLS certificate and private key for token encryption/decryption.# The secret must contain keys named:# "tls.crt" - the certificate# "tls.key" - the private key# The default key pair will be used if it isn't setsecretName: ""# The XSRF key. Will be generated automatically if it isn't specifiedxsrfKey: ""jobservice:image:repository: goharbor/harbor-jobservicetag: v2.0.0replicas: 1maxJobWorkers: 10# The logger for jobs: "file", "database" or "stdout"jobLogger: file# resources:# requests:# memory: 256Mi# cpu: 100mnodeSelector: {}tolerations: []affinity: {}## Additional deployment annotationspodAnnotations: {}# Secret is used when job service communicates with other components.# If a secret key is not specified, Helm will generate one.# Must be a string of 16 chars.secret: ""registry:registry:image:repository: goharbor/registry-photontag: v2.0.0# resources:# requests:# memory: 256Mi# cpu: 100mcontroller:image:repository: goharbor/harbor-registryctltag: v2.0.0# resources:# requests:# memory: 256Mi# cpu: 100mreplicas: 1nodeSelector: {}tolerations: []affinity: {}## Additional deployment annotationspodAnnotations: {}# Secret is used to secure the upload state from client# and registry storage backend.# See: https://github.com/docker/distribution/blob/master/docs/configuration.md#http# If a secret key is not specified, Helm will generate one.# Must be a string of 16 chars.secret: ""# If true, the registry returns relative URLs in Location headers. The client is responsible for resolving the correct URL.relativeurls: falsecredentials:username: "harbor_registry_user"password: "harbor_registry_password"# If you update the username or password of registry, make sure use cli tool htpasswd to generate the bcrypt hash# e.g. "htpasswd -nbBC10 $username $password"htpasswd: "harbor_registry_user:$2y$10$9L4Tc0DJbFFMB6RdSCunrOpTHdwhid4ktBJmLD00bYgqkkGOvll3m"middleware:enabled: falsetype: cloudFrontcloudFront:baseurl: example.cloudfront.netkeypairid: KEYPAIRIDduration: 3000sipfilteredby: none# The secret key that should be present is CLOUDFRONT_KEY_DATA, which should be the encoded private key# that allows access to CloudFrontprivateKeySecret: "my-secret"chartmuseum:enabled: true# Harbor defaults ChartMuseum to returning relative urls, if you want using absolute url you should enable it by change the following value to 'true'absoluteUrl: falseimage:repository: goharbor/chartmuseum-photontag: v2.0.0replicas: 1# resources:# requests:# memory: 256Mi# cpu: 100mnodeSelector: {}tolerations: []affinity: {}## Additional deployment annotationspodAnnotations: {}clair:enabled: trueclair:image:repository: goharbor/clair-photontag: v2.0.0# resources:# requests:# memory: 256Mi# cpu: 100madapter:image:repository: goharbor/clair-adapter-photontag: v2.0.0# resources:# requests:# memory: 256Mi# cpu: 100mreplicas: 1# The interval of clair updaters, the unit is hour, set to 0 to# disable the updatersupdatersInterval: 12nodeSelector: {}tolerations: []affinity: {}## Additional deployment annotationspodAnnotations: {}trivy:# enabled the flag to enable Trivy scannerenabled: trueimage:# repository the repository for Trivy adapter imagerepository: goharbor/trivy-adapter-photon# tag the tag for Trivy adapter imagetag: v2.0.0# replicas the number of Pod replicasreplicas: 1# debugMode the flag to enable Trivy debug mode with more verbose scanning logdebugMode: false# vulnType a comma-separated list of vulnerability types. Possible values are `os` and `library`.vulnType: "os,library"# severity a comma-separated list of severities to be checkedseverity: "UNKNOWN,LOW,MEDIUM,HIGH,CRITICAL"# ignoreUnfixed the flag to display only fixed vulnerabilitiesignoreUnfixed: false# insecure the flag to skip verifying registry certificateinsecure: false# gitHubToken the GitHub access token to download Trivy DB## Trivy DB contains vulnerability information from NVD, Red Hat, and many other upstream vulnerability databases.# It is downloaded by Trivy from the GitHub release page https://github.com/aquasecurity/trivy-db/releases and cached# in the local file system (`/home/scanner/.cache/trivy/db/trivy.db`). In addition, the database contains the update# timestamp so Trivy can detect whether it should download a newer version from the Internet or use the cached one.# Currently, the database is updated every 12 hours and published as a new release to GitHub.## Anonymous downloads from GitHub are subject to the limit of 60 requests per hour. Normally such rate limit is enough# for production operations. If, for any reason, it's not enough, you could increase the rate limit to 5000# requests per hour by specifying the GitHub access token. For more details on GitHub rate limiting please consult# https://developer.github.com/v3/#rate-limiting## You can create a GitHub token by following the instructions in# https://help.github.com/en/github/authenticating-to-github/creating-a-personal-access-token-for-the-command-linegitHubToken: ""# skipUpdate the flag to disable Trivy DB downloads from GitHub## You might want to set the value of this flag to `true` in test or CI/CD environments to avoid GitHub rate limiting issues.# If the value is set to `true` you have to manually download the `trivy.db` file and mount it in the# `/home/scanner/.cache/trivy/db/trivy.db` path.skipUpdate: falseresources:requests:cpu: 200mmemory: 512Milimits:cpu: 1memory: 1Gi## Additional deployment annotationspodAnnotations: {}notary:enabled: trueserver:image:repository: goharbor/notary-server-photontag: v2.0.0replicas: 1# resources:# requests:# memory: 256Mi# cpu: 100msigner:image:repository: goharbor/notary-signer-photontag: v2.0.0replicas: 1# resources:# requests:# memory: 256Mi# cpu: 100mnodeSelector: {}tolerations: []affinity: {}## Additional deployment annotationspodAnnotations: {}# Fill the name of a kubernetes secret if you want to use your own# TLS certificate authority, certificate and private key for notary# communications.# The secret must contain keys named ca.crt, tls.crt and tls.key that# contain the CA, certificate and private key.# They will be generated if not set.secretName: ""database:# if external database is used, set "type" to "external"# and fill the connection informations in "external" sectiontype: internalinternal:image:repository: goharbor/harbor-dbtag: v2.0.0# the image used by the init containerinitContainerImage:repository: busyboxtag: latest# The initial superuser password for internal databasepassword: "changeit"# resources:# requests:# memory: 256Mi# cpu: 100mnodeSelector: {}tolerations: []affinity: {}external:host: "192.168.0.1"port: "5432"username: "user"password: "password"coreDatabase: "registry"clairDatabase: "clair"notaryServerDatabase: "notary_server"notarySignerDatabase: "notary_signer"# "disable" - No SSL# "require" - Always SSL (skip verification)# "verify-ca" - Always SSL (verify that the certificate presented by the# server was signed by a trusted CA)# "verify-full" - Always SSL (verify that the certification presented by the# server was signed by a trusted CA and the server host name matches the one# in the certificate)sslmode: "disable"# The maximum number of connections in the idle connection pool.# If it <=0, no idle connections are retained.maxIdleConns: 50# The maximum number of open connections to the database.# If it <= 0, then there is no limit on the number of open connections.# Note: the default number of connections is 100 for postgre.maxOpenConns: 100## Additional deployment annotationspodAnnotations: {}redis:# if external Redis is used, set "type" to "external"# and fill the connection informations in "external" sectiontype: internalinternal:image:repository: goharbor/redis-photontag: v2.0.0# resources:# requests:# memory: 256Mi# cpu: 100mnodeSelector: {}tolerations: []affinity: {}external:host: "192.168.0.2"port: "6379"# The "coreDatabaseIndex" must be "0" as the library Harbor# used doesn't support configuring itcoreDatabaseIndex: "0"jobserviceDatabaseIndex: "1"registryDatabaseIndex: "2"chartmuseumDatabaseIndex: "3"clairAdapterIndex: "4"trivyAdapterIndex: "5"password: ""## Additional deployment annotationspodAnnotations: {}
[root@UR-20210425NAMA ~]# helm -n infrastructure-prod listNAME NAMESPACE REVISION UPDATED STATUS CHARTAPP VERSIONharbor-prod infrastructure-prod 1 2022-08-04 09:16:33.411526559 +0800 CST deployed harbor-1.4.1 2.0.1
pod
harbor-prod-harbor-chartmuseum-747ccfd78c-48p55 1/1 Running 0 14mharbor-prod-harbor-clair-5cfd8967f5-dp4tk 2/2 Running 5 14mharbor-prod-harbor-core-854ff95b5b-jg6d9 1/1 Running 3 14mharbor-prod-harbor-database-0 1/1 Running 0 14mharbor-prod-harbor-jobservice-6f84f94ff6-lxsxn 1/1 Running 1 14mharbor-prod-harbor-notary-server-556cb84bbc-6v8xh 1/1 Running 5 14mharbor-prod-harbor-notary-signer-b867684d7-mks64 1/1 Running 5 14mharbor-prod-harbor-portal-8459fc6fc4-mp49p 1/1 Running 0 14mharbor-prod-harbor-redis-0 1/1 Running 0 14mharbor-prod-harbor-registry-b494944f-rrm7s 2/2 Running 0 14mharbor-prod-harbor-trivy-0 1/1 Running 0 15m
deployments
deployment-rocketmq-console-ng-prod 1/1 1 1 112dharbor-prod-harbor-chartmuseum 1/1 1 1 17mharbor-prod-harbor-clair 1/1 1 1 17mharbor-prod-harbor-core 1/1 1 1 17mharbor-prod-harbor-jobservice 1/1 1 1 17mharbor-prod-harbor-notary-server 1/1 1 1 17mharbor-prod-harbor-notary-signer 1/1 1 1 17mharbor-prod-harbor-portal 1/1 1 1 17mharbor-prod-harbor-registry 1/1 1 1 17m
statefulsets
harbor-prod-harbor-database 1/1 18mharbor-prod-harbor-redis 1/1 18mharbor-prod-harbor-trivy 1/1 18m
service
[root@UR-20210425NAMA ~]# kubectl -n infrastructure-prod get service |grep harborharbor-prod-harbor-chartmuseum ClusterIP 172.30.253.78 <none> 80/TCP 24mharbor-prod-harbor-clair ClusterIP 172.30.197.27 <none> 8080/TCP 24mharbor-prod-harbor-core ClusterIP 172.30.195.235 <none> 80/TCP 24mharbor-prod-harbor-database ClusterIP 172.30.172.22 <none> 5432/TCP 24mharbor-prod-harbor-jobservice ClusterIP 172.30.181.47 <none> 80/TCP 24mharbor-prod-harbor-notary-server ClusterIP 172.30.130.14 <none> 4443/TCP 24mharbor-prod-harbor-notary-signer ClusterIP 172.30.200.67 <none> 7899/TCP 24mharbor-prod-harbor-portal ClusterIP 172.30.246.36 <none> 80/TCP 24mharbor-prod-harbor-redis ClusterIP 172.30.198.106 <none> 6379/TCP 24mharbor-prod-harbor-registry ClusterIP 172.30.152.60 <none> 5000/TCP,8080/TCP 24mharbor-prod-harbor-trivy ClusterIP 172.30.177.58 <none> 8080/TCP 24m[root@UR-20210425NAMA ~]#
ingress
[root@UR-20210425NAMA ~]# kubectl -n infrastructure-prod get ingressNAME CLASS HOSTS ADDRESS PORTS AGEharbor-prod-harbor-ingress <none> core.harbor.domain 80, 443 19mharbor-prod-harbor-ingress-notary <none> notary.harbor.domain 80, 443 19m
pvc
[root@UR-20210425NAMA ~]# kubectl -n infrastructure-prod get pvc |grep harbordata-harbor-prod-harbor-redis-0 Bound pvc-f6ba3c53-c077-4364-8c43-3e707e3be6e3 1Gi RWO sfsturbo-prod 22mdata-harbor-prod-harbor-trivy-0 Bound pvc-e47a5ac1-5b5b-45b9-b7d2-496ee5e37145 5Gi RWO sfsturbo-prod 22mdatabase-data-harbor-prod-harbor-database-0 Bound pvc-2ffabaae-59bf-44a9-9aaf-b2494d162162 1Gi RWO sfsturbo-prod 22mharbor-prod-harbor-chartmuseum Bound pvc-7e6258e2-e88b-4d70-a511-5ba4487caf10 5Gi RWO sfsturbo-prod 22mharbor-prod-harbor-jobservice Bound pvc-823931d4-16e3-4b01-86a7-8a8b0a149e8d 1Gi RWO sfsturbo-prod 22mharbor-prod-harbor-registry Bound pvc-96c1acdf-b6ee-4c2a-8668-e5ffffacdedd 5Gi RWO sfsturbo-prod 22m[root@UR-20210425NAMA ~]#

